Phishing
Scamming by email
What is Phishing? | Protect Yourself | Varieties
Real World Examples | Fake Links | Transfer of Trust
Anti-Phishing Tools | Resources
All trademarks, company names or logos are the property of their respective owners.
Protection against identity theft and other scams are contained in these pages:
- Identity theft
- Vishing (phone scams)
- Phishing (email scams)
- Computer & "tech support" scams
- Ransomware
This page will help teach you how to prevent yourself from becoming a victim of a phishing attempt. Phishing traditionally involves the use of email to scam you but scammers also use text messages and social media.
The information was written with computers in mind, but these warnings also apply to smartphones and tablets. Mishing (mobile phishing) is trending because of the vast mobile market, replacing email with SMS on mobile devices.
- Give yourself time to determine if a caller is legitimate before providing information.
- Be wary of any unexpected email or text message.
- Slow down when you see wording designed to panic you (urgent, account locked, etc.).
- Ignore phone calls from people you don't know.
- Be careful to enter the correct phone number when calling for support. Scammers purchase “near-digit” phone numbers.
- Delete suspicious emails and texts. Do not click on any links contained in them.
- NEVER respond to requests for Bitcoin, gift cards or wire transfers. These are scams.
- NEVER follow unexpected instructions to download software or visit websites.
- NEVER provide remote access to your computer to an unknown caller.
AI Makes Detection More Difficult
Online AI resources like ChatGPT, OpenAI, and Microsoft's Copilot will make it even harder to detect such scams.
It has the ability for someone with not very much skill set or maybe even not a great command of the English language to create a full, almost flawless script to use in an attack against somebody in a phone scam or an email phishing scam or what have you.
— Robert Falzon
I received an email from a friend asking me to buy an Apple gift card. The phraseology was so plausible that I had no reason to question the content. After purchasing the gift card I phoned her, only to discover that the email had not come from her. She had been hacked.Fortunately, I had not sent the number on the Apple gift card as she had requested, to have done so would mean the hackers would have access to it.
These sophisticated scammers/hackers possibly used AI to impersonate her.
— Sue Mackinnon
Phishing: Obtaining Information by Deceit
Phishing is a form of spam intended to obtain financial and personal information by deceit.
Phishing is sending emails or other electronic communications to fraudulently or unlawfully induce recipients to reveal personal or sensitive information, such as passwords, dates of birth, Social Security Numbers, passport numbers, credit card information, financial information, or other sensitive information, or to gain access to accounts or records, exfiltration of documents or other sensitive information, payment and/or financial benefit.
— Microsoft
It Starts with Email
A staggering 91% of cybercrime starts with email, according to a report by security firm FireEye. Phishing attacks have increased six-fold since the start of COVID, according to Zimperium, and mobile devices are now the main target.
— CSO
KnowBe4's Q1 2024 global phishing report finds that HR and IT related email subjects account for more than 42% and 30% of top phishing email subjects respectively
— KnowBe4

Credit: KnowBe4
Or a Text Message
In the case of mobile phones, it is more often a text message.
Mishing (mobile phishing) takes advantage of the messaging capability of mobile devices to send deceptive SMS warnings to entice the recipient to follow malicious links.
Mishing is a phishing attack that uses SMS messages instead of emails to deceive victims into revealing sensitive information or clicking malicious links. Cybercriminals disguise messages as urgent notifications from banks, government agencies, or corporate IT teams, tricking users into providing credentials or downloading malware.Mishing is part of a broader trend of mobile-targeting phishing, which includes:
Cybercriminals are intensifying their focus on mobile phishing, with smishing now making up 37% of phishing attacks in India, 16% in the U.S., and 9%in Brazil. Meanwhile, quishing is also gaining traction, particularly in Japan, the U.S., and India.
- Smishing: Typical phishing via SMS, where attackers impersonate trusted entities to steal login details or personal information.
- Quishing: A newer method that uses QR codes to direct users to fraudulent websites, often bypassing traditional security filters.
- Vishing: Also known as voice phishing. This is where attackers call victims pretending to be from legitimate organizations to manipulate them into sharing sensitive information.
— eSecurity Planet
Taking Advantage of Weaknesses
Phishing email take advantage of human weaknesses:
- Phishing emails take advantage of people's blind trust. The intent is to steal your on-line identity (identity theft).
- The goal is payment in untraceable forms (e.g., cryptocurrencies or the redemption codes on gift cards).
- The information gained will be used for unauthorized access to your existing accounts or to establish new ones. Crimes may be committed in your name. Your reputation could be destroyed.
There are a few basic psychological tricks that phishing attacks and phone scams attempt to use against us….[P]hishers' tactics have become more sophisticated over time. Using data from social media, it is now relatively easy to personalise the details of the messages to make them seem more convincing — a process called "spear phishing". Fraudsters are also taking advantage of increasing reliance on smart phones, with a greater number of SMS phishing (also called "smishing") attempts.
[T]hey'll try to use some familiar elements — like the name or logo of a famous brand — to gain your immediate trust. Most scams will then try to elicit a strong emotional response that stops us thinking logically. That might be the promise of an immediate reward, or a potential threat. (As I found, scam artists can get meta — warning you of an impending fraud that needs immediate action, accessible only with your bank details.
— BBC Future
The magic sauce, as it were, is in the way phishing attacks are branded.Attackers are doing their homework by researching targets on social media, message boards, media reports, and other online sources to find hyperspecific ways to manipulate human nature and emotions.
They use people's fears, their sense of urgency or curiosity, or their need for reward, validation, or an entertaining distraction.
— Menlo Security
Using Urgency to Panic Recipients
Most phishing emails use some tricks to create a sense of urgency so that you panic. Calm down and take a closer look:
Anything that urges you to act fast with a short deadline (such as 48 hours), asks for your financial information, offers you a reward, or just seems overall wrong, it probably is.Of course, you may receive a legitimate message informing you to take action. For your safety, don't click the link in the email, no matter how real it appears to be. Instead, visit the real website from your browser and log in from there to check your account status.
— Zone Alarm blog
In most cases you'll find out that a scam is involved.
Weaknesses in Software
Hackers exploit vulnerabilities in Internet software. Many email programs use Microsoft Word to display emails (and Internet Explorer before that).
Creating malicious Office macros is still the most common attack technique deployed by cyber criminals looking to compromise PCs after they've tricked victims into opening phishing emails.Macros are a function of Microsoft Office that allow users to enable automated commands to help run tasks. However, the feature is also abused by cyber criminals. As macros are often enabled by default to run commands, these can be used to execute malicious code — and thus provide cyber criminals with a sneaky way to gain control of a PC.
— ZDNET
Always upgrade or uninstall obsolete software. Use a safer browser and enable all available privacy protections.
Looks Can Be Deceiving
Phishing often employs the use of well-known brand names:
In a brand phishing attack, criminals try to imitate the official website of a well-known brand by using a similar domain name or URL and web-page design to the genuine site.The link to the fake website can be sent to targeted individuals by email or text message, a user can be redirected during web browsing, or it may be triggered from a fraudulent mobile application.
The fake website often contains a form intended to steal users' credentials, payment details or other personal information.
— Check Point blog
Essentially, they want to convince you that you're seeing something from a trusted brand (a transfer of trust).
Proprietary Images Can be Hijacked
Looks can be deceiving. The presence of brand name logos or other proprietary images does NOT guarantee authenticity.
It is easy for company logos and other images to be captured and used to mimic a company's emails or website.
The technologies employed in such phishing attempts has improved a great deal.
[P]hishing messages only seem to be getting savvier and more authentic-looking, fooling even seasoned experts. Gone are the days when obvious misspellings and grammatical errors provide a dead giveaway that shenanigans are at play.
— Trustwave Blog
It is still common for such messages to come from unlikely email addresses, whether they be Gmail, Hotmail — anything but the corporate domain. You can verify where an email came from by viewing the message headers.
How to Protect Yourself
Stop and Think Before Acting
The phishing email is designed to get you to act impulsively, before you have a chance to think.
Remember to Stop. Think. Connect. — Pause before you click or connect.
How to Protect Against Scam Emails
- Do not panic. Do not get scared by the crooks. They do not know you, nor do they have access to your computer. It is a classic scare technique. Try to ignore it, even if it sounds disturbing.
- Do not pay. Once you've paid money, you will not get it back. Instead, you might be attacked more frequently since you've shown the attacker that you are a profitable target.
- Use strong passwords. Use unique strong passwords for different services. If possible, enable multi-factor authentication in order to increase security. A password manager can help you remember all these different passwords.
- Awareness-training programs. As an organization, you should implement an awareness-training program for your employees. Also, make sure that your employees know how to report such scam emails to your IT department.
- Update all relevant systems. Ensure that all your systems are up-to-date and that you are using a comprehensive security solution that can automatically protect you from the newest cyberattacks.
- — Acronis
Legitimate businesses will never ask for personal or account information via email or phone calls placed by that business. (If you call them, you do have to provide information to prove who's calling.)
Don't follow any link either those found in emails or linked websites. The email may employ fake links on a bogus site to misdirect you into providing your login details.
Instead, use the address included in a legitimate source like a paper invoice or account statement sent to you by the company via mail.
How to Protect Yourself
- Protect yourself from phishing.
- Avoid phishing & improve your online security.
- Two simple rules that can spot nearly every email phishing scam.
- How to recognize and avoid phishing scams.
How to Read Message Headers
Email programs usually only display the short headers (from:, to: and subject:).
However, there's a lot more information hidden behind the scenes. The full headers contain a lot of tracking information which is necessary if you want to check out the validity of an email.
In most email clients (programs on your computer) you can see the full headers by viewing the message source. This varies by email client.
The Bat! Right-click on the message then select View Source. Thunderbird Click on the More in the message then select View Source.
For webmail and other services see How to view message headers on various email providers from Google help.
Scammers Getting Smarter
You can't count on identifying spam by the email sender's address. Scammers often know how to forge headers to make it appear to come from a legitimate company.
Recently I've noticed that spam with the same message seems to come from a different email address every time (probably the same scammer using stolen addresses).
HTML Email Hides Details
One of the dangers of "enhanced" or HTML email is that stuff can be hidden. See How to unmask fake links.
Firefox security features help you avoid problems with invalid or insecure sites.
Other browsers may have these features, but Firefox is the only major independent browser and Mozilla is committed to personal privacy.
Ignorance is Your Downfall
Your ignorance is your downfall. Learn the signs that you're being scammed:

Don't Get Hooked: How to recognize and avoid phishing attacks
Report Identity Theft
If you have been a victim of identity theft (or suspect you have) report identity theft then notify your local police department.
While local police may be unable to do much with an international-based crime, the report will help to establish credibility when dealing with your bank and other institutions when you try to repair the damage.
Don't let embarrassment keep you from talking to the authorities. If you were the only victim, identity theft would not be a growing problem. The sooner you report the potential identity theft, the sooner you can begin to resolve the issue.
Identity Theft is a Long-Term Problem
If you are the victim of identity theft, you can expect to fight to regain your credit rating for years — over and over again.
Victims report that it takes months or years to regain their credit rating, only to find that a new report forces them to start all over again.
Keep Paper Files
While electronic data can quickly get you into trouble, financial institutions want physical (on paper) evidence that you're not responsible.
Phishing Resources
These are some excellent resources on dealing with phishing attempts:
- Smishing, spoofing, pharming, or vishing? The complete guide to phishing scams.
- Phishing prevention: Best practices to secure your business.
- How to avoid phishing scams.
- 7 easy tips to avoid scammers on social media (Oct. 2023).
- Don't get caught! How to spot email and SMS phishing attempts (Sep. 2023).
- Is this Facebook email a fake? (Feb. 2023)
I use AntispamSniper, an excellent third-party antispam tool, with The Bat!.
Specific Varieties of Phishing
I've covered the following types of phishing, but there many others including smishing, spoofing, pharming and vishing.
Spear Phishing | Callback Phishing | Catfishing | Sextortion
Spear Phishing
“Spear” phishing is harder to detect. It uses personal information found online such as details you shared on social media or was culled from a data breach then sold on the Dark Web.
The email may appear to come from someone you can trust, but it is a scammer looking to steal from you.
The spear phisher thrives on familiarity. He knows your name, your email address, and at least a little about you. The salutation on the email message is likely to be personalized: "Hi Bob" instead of "Dear Sir." The email may make reference to a "mutual friend." Or to a recent online purchase you've made. Because the email seems to come from someone you know, you may be less vigilant and give them the information they ask for. And when it's a company you know asking for urgent action, you may be tempted to act before thinking.
These messages often have short deadlines or are made to appear urgent in their nature. The more you analyze the message, the more likely you're able to see through the deception.
- How to avoid a spear-phishing attack. 4 tips to keep you safe from timeless scams.
- Norton email scams.
- Botnet that knows your name and quotes your email is back with new tricks.
Callback Phishing
“Callback phishing” uses email with a fake invoice or other urgent item to induce the recipient to call a phone number.
Callback phishing typically involves an email, a phone call and a fake subscription/invoice notice. In recent months, hackers have impersonated businesses in order to dupe victims into making phone calls that lead to the download of malware.
— CyberTalk
Catfishing
Catfishing is using someone else's identity while online, usually to destroy that person's reputation or to hide their own identity in an attempt to defraud someone.
Catfishing is when someone uses images and information (often taken from other people's social media accounts) to create a new identity online – sometimes using an individual's entire identity as their own.
The Cybersmile Foundation
This situation often happens in online dating. Statistics show that 40% of catfishing incidents happen on dating applications alone. This number is a 7% increase compared to 2018.
DataProt
Prevention
The key to preventing yourself from becoming the victim of catfishing (or any other form of identity theft) is to be wary. Trust must be earned, not assumed.
- Being cautious — When talking to anybody that you don't know online, always remain slightly cautious, especially if you have only just started speaking with them or have no solid evidence that they are who they say they are.
- Never giving out money — Some catfishers will target people in order to scam money from them. You should never give money to anybody who asks for it online.
- Taking your time — Always be careful when sending images or sexually explicit messages to another person online. Once you press send, it can't be taken back!
- Talking to someone — If you have concerns about someone you are speaking to online, confide in someone you trust. Tell them about your concerns as they may be able to help you identify any "red flags" you may have not noticed yourself. New perspectives often bring new solutions!
- Not being afraid to ask questions — As uncomfortable as it might be, don't be afraid to ask as many questions as you need to in order to feel comfortable talking to someone. If they are a catfish, they might not be able to answer all the questions accurately and then you'll be more likely to know that something isn't right.
- Adjusting your privacy settings — Catfishers will commonly look for potential victims to target, and by having your privacy settings adjusted on your social media accounts to 'private', you are less likely to fall victim to catfishing because nobody can see the information on your profile.
- — The Cybersmile Foundation
- All you need to know about catfishing and how to protect yourself.
- Spotting a catfish: How to avoid getting hooked by a fake online.
- What is catfishing online? Signs and how to tell.
- All you need to know about catfishing and how to protect yourself.
- 14 signs you're getting catfished online.
Sextortion and Blackmail
Sextortion is obtaining intimate images under false pretenses, then using them to blackmail you into providing money (ransom) or additional images.
Simply put, sextortion is blackmail. It's when someone threatens to send a sexual image or video of you to other people if you don't pay them or provide more sexual content.Remember, the best way to fight sextortion is to prevent it. So don't send nudes
— Don't Get Sextorted.ca
The extortionist then seeks out your contacts and other vulnerabilities via your social media accounts.
Knowing who is closest to you is then used by the blackmailer to threaten to expose your activities to your friends, family and co-workers.
Teens a Target
Too often children are targeted by online predators pretending to be someone of similar age interested in friendship and more.
Once the predator gains their trust, they try to get the teen to send compromising photos which they then threaten to post online or reveal to their friends and family.
Threats may be used to further gain additional photos or even to meet the “friend” in person.
[Stephen Sauer, the director of Cybertip.ca] said oftentimes children are specifically targeted. Organized crime rings based overseas pose as young women on social media platforms that teenagers use such as Snapchat and Instagram.They convince them to send sexually explicit images or videos and then immediately threaten to share the content if the children don't provide them with money or sometimes more images.
Victoria Times Colonist
This is why it is so important for parents to monitor their children's online activities, especially on social media.
Perpetrators Likely Outside of Canada
Recent changes in British Columbia law are designed to protect those whose intimate photos are shared without their consent.
While this may work if the perpetrator is located in Canada or the United States, most blackmailers are located outside of the country and unreachable by Canadian or American law enforcement.
Suicide: The Amanda Todd Case
This sort of blackmail can result in suicide when the youth feels there no one to turn to.
One example is Amanda Todd. She committed suicide after several years of harassment from someone already convicted of the same crime by Dutch courts.
The man convicted of harassing and extorting British Columbia teenager Amanda Todd has been returned to the Netherlands, where the prosecution office says a judge will decide if he serves any of his 13-year Canadian sentence.Canada's Justice Department says Aydin Coban was taken back to his home country on Nov. 24, where he will continue serving a nearly 11-year sentence imposed by a Dutch court in 2017 for similar crimes involving more than 30 youth.
[I]t's possible he may not serve his Canadian sentence because he was already serving the maximum Dutch term for similar crimes committed around the same time he was harassing [Amanda Todd].
Victoria Times Colonist
The fact that a Dutch court decided that he'd already been sentenced the maximum term simply means that the law is no longer a deterrent. Justice can no longer be served.
Have You Been Blackmailed Online?
Unfortunately, sextortion has been on the rise lately. But there are ways to prevent and fight it.
Do NOT Pay the Blackmailer
If you are being blackmailed online, paying the scammer will not resolve the issue. You're dealing with thieves.
IMPORTANT: If you paid the scammers anything at all, they will simply turn around and ask for more. This is how this scam goes 100% of the time. Don't be fooled into thinking a one-time payment will be the end — IT NEVER IS!
— Dennis Faas
Who Do You Turn To?
Don't respond to the blackmailer on your own. It won't work.
Sextortion — What to Do (and What Not to Do)
Dennis is an experienced systems administrator and IT technical analyst specializing in cyber crimes (sextortion, blackmail, tech support scams).
Dennis Faas's Sextortion: What to do (and what not to do) will inform you about your options and the limitations of most alternatives.
The scammers are masters at this game and if you haven't had the luxury of experiencing their dirty tricks and traps ahead of time, then you'll likely fall victim to their sinister plans. The good news is that it's all completely preventable with my help.If you decide to hire me, I'll share with you my plan on how to stop sextortion, plus you'll also receive exceptional 1-on-1 consultation whereby I answer all of your questions by phone, including custom advice per your circumstances.
Don't forget - a phone call is free up to 15 minutes. Ask me anything - all you need to do is send me an email.
— Dennis Faas
His contact information and details are in the article linked above.
Cybertip.ca
Call 1-866-658-9022 or go to Cybertip.ca — Canada's national tipline for reporting the online sexual exploitation of children.
As children grow and the internet evolves, it can be difficult to keep up with online developments. Cybertip.ca, which is operated by the Canadian Centre for Child Protection (C3P), is committed to providing the public with current and age-appropriate information and resources to help educate Canadians about how to keep children safe while online and reduce child victimization.
— Cybertip.ca
Cybertip.ca provides resources on:
- Child sexual abuse.
- Online harms includes information and support related to online luring, intimate images, sextortion and online sexual violence.
- Download the sextortion lesson including PDF, PowerPoint presentation and speaking notes.
Facebook Blackmail Popular
While there are many avenues to obtain phishing information and use it against someone, Facebook is particularly attractive to blackmailers:
With…many people actively using Facebook, it makes it easy for Facebook sextortion scammers to find information about you, including: a list of your family members, friends, where you live, where you work, etc — all without having to spend time looking it up elsewhere, or having to pay a third-party website for the information. This is what makes Facebook blackmail so popular.
Dennis Faas
Social media like Facebook seem to raise particular risks, with phishers enjoying a much higher hit rate — perhaps because they can glean more information to personalise their messages, and because we are so keen to build our friendship group. Quite simply, the more you use a particular social network, the more likely you are to fall for a scam on that app.
— BBC Future
- Being blackmailed for money on Facebook? Here's what to do.
- Sextortion: All you need to know.
- Sextortion scam: What to do if you get the latest phishing spam demanding Bitcoin.
See Have you been blackmailed online? if you're a victim.
“Your Computer Hacked”
Claims that your computer has been hacked is a common approach for online blackmail attempts. Any messages using any threat, including exposing your online habits, should be immediately deleted. They are on a fishing expedition. Don't fall for it.
[I]t is often the case that the scammers have no such evidence of the user's activity; they are just bluffing to get the user to pay the ransom. A password can be bought for a few dollars on the dark web, and scammers are often clever in how they present the little information they have.
— Check Point blog
Sample Sextortion Email
Here's some of the text from a sextortion email quoting the email address as the account:
I have bad news for you. I hacked into your operating system and obtained full access to your account. After that, I made a full backup of your disk (I have all your address book, view site history, all files, phone numbers and addresses of all your contacts).I took a screenshot of the intimate website where you are satisfied (Do you understand what I mean?). After that, I made a video of your pleasure (using the camera of your device). It turned out beautiful! I firmly believe that you would not want to show these photos to your parents, friends or colleagues. I think 300 € is a very small sum for my silence.
P.S. I guarantee that I will not disturb you after the payment because you are not my only victim. It's a code of honor for hackers.
The goal was to rattle the recipient into sending 300 €. The “code of honour” is worth about as much as a politician's campaign promises, as are the other claims.
Never pay ANY ransom. Just like blackmail, there is no such thing as a one-time ransom payment…you will become their bank account until they've drained you dry.
Passwords as “Evidence”
Often the email will include a password as the “proof” of their access. These passwords were probably obtained from one of many security breaches.
Be sure to change all your passwords after learning about any breach that involves any online service you use.
Unfortunately, in the modern age, data breaches are common and massive sets of passwords make their way to the criminal corners of the Internet. Scammers likely obtained such a list for the express purpose of including a kernel of truth in an otherwise boilerplate mass email.
— EFF
Check to see if your email or password has been involved in a security breach:
- Email addresses: Have You Been Hacked?
- Passwords: Have I been pwned?
Tighten Your Security
If you have decent up-to-date computer security software, have changed the default passwords on your router and use good password hygiene it is highly unlikely that you've been hacked.
If the language is quite generic and without details, I suggest you ignore the threats. However, you should do a security audit to ensure your system is secure rather than paying a scam artist.
Learn more about how to deal with phishing attempts.
Some Real World Examples
“CRA” Phishing Scam
The CRA is often used in phishing and vishing attempts.
The following phishing attempt looked like a typical eTransfer (or would have if I'd downloaded the remote images). Notice the email address:
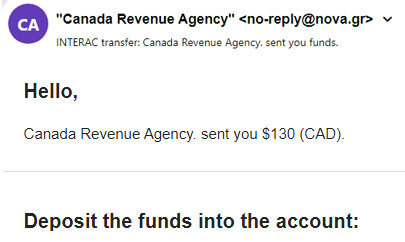
The CRA doesn't offer eTransfers. Refunds are via a cheque mailed to your address or direct deposits into your bank account.
“Geek Squad” Phishing Scam
This emailed “receipt” from “Geek Squad” is a phishing attempt:
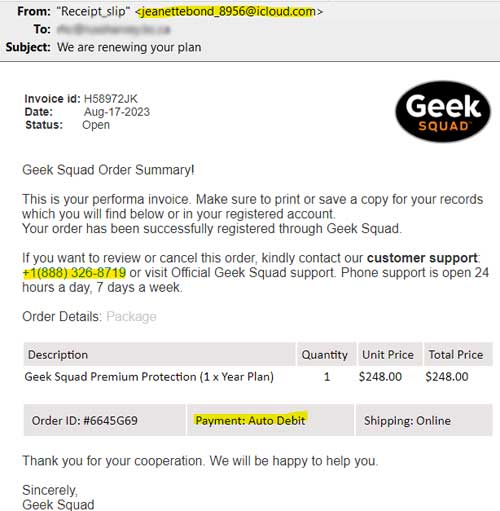
Even though I had purchased no such service, the scammer hoped that the threat of an unauthorized $248.00 charge would spur me to respond without thinking it through. Stop and review the email and question its contents.
An Unlikely Email Address
A legitimate Geek Squad email would come from a company email address, not a free webmail address like [email protected] and certainly would not identify themselves as "Receipt_slip".
A Fake Phone Number
Checking for fake links I hovered my mouse over the displayed number, revealing another number and automatically calling the second number if clicked while viewing the email on a cell phone:
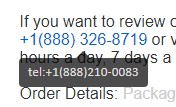
Both numbers are fake. Geek Squad's real number is 800-433-5778 (determined by googling “Geek Squad”).
While the language in this phishing attempt is quite good (unlike earlier attempts), the salutation is weird, thanking me “for my cooperation.” Supposedly they'd already “helped me” (or why an invoice?).
What to Do
I marked the mail as spam. I neither clicked on any links nor investigated any further (too risky).
To verify any such invoice, open the real Geek Squad website (part of Best Buy) then select cancelling or editing an order.
- If you do have an account, logging in will show no such invoice or service plan.
- If you don't have a Geek Squad account, how could they send you an invoice?
More About How the Scam Worked
An opinion piece in the Times Colonist provided more details about the “JP's” experience:
To enable this, he was to log in to a website (which was obviously a fake), and download a program that would enable him to claim his refund. JP did so.Here a clever piece of swindling occurred. When he logged on to the site, he was told to type in the amount of the refund. So he typed in $240.
But the website altered the amount he'd typed in to $24,000. When he drew the customer representative's attention to the error, he was led though a correction process.
— Times Colonist
The scammer then tries to get you to refund the $23,760 “overpayment” by logging into your bank account. When that fails you're asked to send a wire transfer to a bank in Asia. Does that sound like you're dealing with a legitimate business?
“Microsoft” Phishing Scam
The following is a screen capture of another email, supposedly from Microsoft:
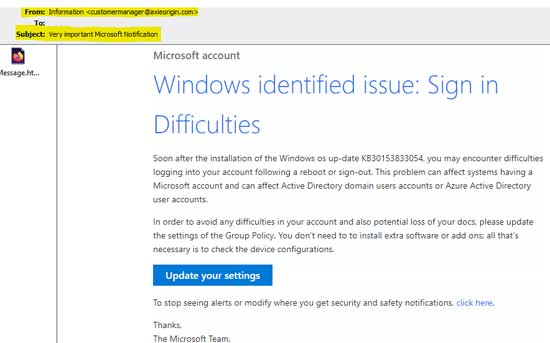
- Microsoft would never send an email from a non-Microsoft domain.
- Hovering over the “Update Your Settings” button showed that it would take you to a phishing site.
Typically, the destination page would mimic Microsoft's site. When you entered your login information, your Microsoft account would be immediately compromised.
An “Urgent Help Request”
A message can also be designed to get the victim to send money via Western Union or some other method.
This sort of email will seem to come from a “friend” or “family member” that needs money to help them pay their hotel bill or get home because they've suffered some sort of accident or are the victim of a crime.
If they reply with their financial details, the phisher can collect the funds themselves.
Stop and Examine the Email
Their goal is to get you to respond quickly before you can think too hard about the claims in the message. Beware of these signals:
- The sender indicates they are “out of contact” but in dire need.
- Watch for any attempt to get your user name and password such as a response form embedded in the email message itself. Would the sender be able to generate such a form, even if it were legitimate?
- Attached files are suspect (most contain scripts that will infect your computer).
- Altered or unusual links in the body of the message or its attachments.
- The presence of official looking logos attached to the message (most companies now use images hosted on their server).
The details in the email are usually general in nature. Some information may be accurate but the scammer doesn't know you as well as the real person does.
How Did They Manage to Contact You?
Ask yourself how the sender was able to email you when they have no cash, credit cards or cell phone?
- A genuine victim could have resolved their issues with a call to the credit card company.
- The hotel would have obtained a copy of a guest's credit card when the reservation was made (and verified it when the person checked in).
- The airline could re-issue a lost or stolen ticket.
- Emergency passports can be re-issued by embassies everywhere.
Tighten Passwords
The real owner of the email address needs to let people know they're okay and to change their password to something more secure (and probably change their security habits).
Going on a Phishing Expedition
Becoming a victim is easier than you might think. Let's have a look at the process from the perpetrator's point of view. Remember, YOU are the intended victim of this trap.
1. Create a Fake Website
The first step is to set up a look-alike site that closely resembles a site that your victims are already using or could be using.
- A phishing message could exploit a bank, Google Docs, e-Bay, PayPal or any site where you conduct business.
- The company's logo and other trademarked images are used to convey authenticity. (See the section on using transfer of trust.)
- When you click on these links and enter the requested login information, you giving the scammer access to your real account(s).
2. Send Out Thousands of Emails
Next, send an email message to thousands of potential victims indicating that there is a problem with the account.
Indicate that the recipient must act quickly to avoid having their account closed, being arrested or similar threats. You don't want the recipient taking time to think or to contact the actual company where the account is located, do you?
Of course, you don't want to be caught, so you'll purchase compromised email addresses on the Dark Web and use those to spread your message.
According to Symantec's 2015 Website Security Threat Report Part I, it costs as little as $0.50 to $10 per 1,000 stolen email addresses on the black market — a testimony as to the poor quality passwords many folks use and how easy it is to obtain them.
3. Collect the Information
The victim clicks on the link and finds themselves on what they believe to be a legitimate site, so they enter their user name (email address) and password.
Of course, this information is not going where they think it is — but directly to thieves.
4. Assume Their Identity
Taking the victim's electronic identity which was obtained via the phishing site, you can go to the actual site then log into their account.
The information obtained in this manner can then be used to purchase items, withdraw funds or set up credit in their name (if it is a financial account) or use those credentials to hack other accounts.
Unmasking Fake Links
One of the methods commonly used to scam people are fake or obfuscated links in email messages.
An obfuscated URL is a web address that has been obscured or concealed and has been made to imitate the original URL of a legitimate website. It is done to make users access a spoof website rather than the intended destination.Obfuscated URLs are one of the many phishing attacks that can fool Internet users. The spoof site is often an identical clone of the original one in order to fool users into divulging login and other personal information.
An obfuscated URL is also called a hyperlink trick.
— Techopedia
Fake links drive unsuspecting traffic to websites that:
- generate revenue for them via pay-per-click ads or similar revenue generators; or
- pretend to be a legitimate site like a bank (in order to steal account information); or
- infect their computers with malware (turning their computer into part of a botnet that attacks legitimate sites or attempts to infect other computers).
Decent security software and detection provided by web browsers like Firefox can help prevent such attacks, but it is best not to click on these links in the first place.
Where Does That Link Go?
Would you click on links like the following?
Of course not.
Those looking to steal your identity aren't going to unmask themselves. They tell you the link points to something that takes advantage of your curiosity or greed.
You can't trust the linked text to tell you where the links actually go because it is ignored by your browser.
Links Have Two Components
Hyperlinks on a website (and in an email) have at least two components:
- the linked text (what you see highlighted in the link); and
- the hyperlink (the actual address where you are being sent).
Only the hyperlink itself (the hidden part) determines where the link sends you.
Just as placing a Mercedes licence holder onto a Ford doesn't turn it into a Mercedes, a misleading description doesn't change the link's destination.
Not All Links are What they Appear to Be
Take a look at the following link (a new window opens):
Hint: it doesn't take you to the Bank of America's site, but to another (but safe) site.
Using the Status Bar
If you hover over the link and look in the status bar at the bottom of the program (some browsers show the hyperlink address in a small box above or below the link itself) you can tell the destination without clicking the link (and potentially getting yourself into trouble).
Just because the linked text says it is pointing towards a particular location doesn't mean that is the actual destination.
Learning More of the Mechanics
If you are interested in the mechanics of this process, have a look at Cut 'N Paste HTML Editing. It gives some simple HTML lessons and demonstrates how HTML links work.
Short Links (URLs)
Shortened links (web addresses or URLs) are common in Twitter messages because 140 characters doesn't allow for long complex links.
These are also useful in emails where very long and complex links can be broken when the line is wrapped by your email program.
Services like TinyURL and Bitly hide the destination address.
Unmasking Shortened URLs
You can unmask the destination of these links before visiting the site. Paste the address into your browser's address bar with the changes noted below, then hit enter:
- Add preview before a TinyURL address (preview.tinyurl.com/c7b7ybm).
You're taken to TinyURL or Bitly with information showing about the true (full) destination for the shortened link. In these examples, all shortened links point back to this page.
Other Link Shorteners
If you're unable to determine the destination, I recommend using Redirect Tracker to check any short or affiliate URL (bit.ly, goo.gl, etc.) to see where it goes.
Legitimate & Illegitimate Uses
Shortened URLs are seldom needed in an email except where the length of a complex address wraps in the email window, potentially causing the link to break.
Phishing email emails commonly use shortened links to obfuscate the destination.
Emails containing the promise of a financial reward (“click bait” messages) are dangerous. I strongly recommend deleting such messages.
In most cases, clicking on these will simply bring you grief.
An Example
I received a suspicious email (supposedly from “Costco”) with a shortened link. Redirect Tracker revealed that the unmasked destination address was being redirected twice from the obfuscated address:

This is not a good sign, especially since “zharerewards” is an obvious misspelling of sharerewards.
Other Issues
Shortened URLs have security and other issues.
- Destination unknown: shortened URLs and your security.
- Short URLs considered harmful for cloud services (or PDF version).
How Can a Fake Site Exist?
First of all, people that set these fake sites up wish to remain anonymous. They are breaking the law and don't want you (or the police) to be able to find them after they steal your identity.
Short-Term Links
The provided links are only up for a short time before they are removed by the owners of the site affected or by the legal authorities.
Forged links often point to a site in an educational institution where passwords and access are easy to come by.
By their very nature, universities house a lot of smart and curious people. Smart as they are, too many don't view the issue of security as their problem.
Because of lax attitudes, many could suffer significant financial setbacks.
Delete Attached Forms
More recent phishing attempts have provided an attachment to their messages which, when opened, replace the fake site with a form which accomplishes the same nefarious purpose — to get your information using deception.
Don't be fooled. An unexpected attached form (or PDF or Zip file) is likely an attempt at identity theft. Even .DOCX and other Microsoft Office documents can be dangerous.
Configuring Your Software to Protect You
Whatever choices you make with your software, you'll want to take advantage of some advanced (and often hidden) features:
- Ensure that you can see the hints when your mouse hovers over a link or other hot spots on your browser.
- Use stronger passwords. There are complex online password generators as well as software to help remember more complex passwords. I strongly recommend Bitwarden password manager.
- Only shop on encrypted websites — those prefixed with
https://and displaying a padlock symbol in the address bar. Unencrypted sites are more vulnerable to being hacked. - Learn how to view the headers in an email message.
- Know the signs of a risky message (phone and phishing scams have a lot in common).
- Ensure your security software is current and updated frequently.
- Windows users are more vulnerable and should ensure that all critical Windows Updates are installed, including the latest service pack.
- Mac and Linux users also need to be vigilant in updating. While infections are not as common, they are becoming more frequent.
- Ensure your browser and email software are current and updated.
- Stop using and uninstall software that is no longer actively supported or maintained.
Advanced features are often hidden to provide for a cleaner, simpler look. Microsoft's hiding of known file extensions is one example.
Remember, software vendors don't have to pay to clean up problems caused by the shortcomings in their products or within optional downloads installed at the same time as their own product.
If you need help determining how to configure your software and security protection, contact someone knowledgeable. Be careful when selecting your “expert” helper (especially if they call you). Remember, you're putting your trust in this person.
I provide these services, but only in Greater Victoria (located on the west coast of Canada).
Get Help From Your ISP
Use whatever tools your ISP makes available to identify potential spam, phishing and other problematic email messages. Check your ISP's help or support website or call their help line.
Using Transfer of Trust
A successful phishing scheme, like any con, depends upon gaining your trust.
They'll use your trust of your financial institution, a major vendor (e.g., Microsoft or Apple) or other authority (CRA, CRTC, FBI, phone company, etc.).
If you believe they are who they say they pretend to be, then you'll be more likely to follow their instructions without questioning anything.
Your “trust” in the caller, web page or link is only because it appears to be from someone you know and trust.
The Internet Can Be Exploited
The original Internet was used only by scientists exchanging data. There was no need for high security. Trust was implied.
But this has changed. The Web is now used for e-commerce, personal transactions, banking, socializing and more.
Browsers and modern enhanced email messages can be exploited, particularly if you don't understand HTML markup. Without that knowledge you can't protect yourself.
Preventing Successful Phishing
There are a number of things that you can use to avoid being the victim of this type of attack:
- Be wary of any threats to close your account especially emailed notices.
- Requests for account information or passwords are NEVER legitimate.
- Be wary when using public computers. Your passwords, accounts and personal information can be retained by the browser's cache for later retrieval by anyone with access to that computer.
- Do not use open or untrusted secured wireless networks such as those at coffee shops and other public networks. Someone can be "listening in" on your traffic.
- Do not trust information emailed to you including any links to sites.
- Do not trust information on an unknown website.
- Keyloggers can capture private information on any computer.
Always use trusted sources to obtain the telephone number or website address to contact any site requiring personal information or a password.
Google is not necessarily that trusted source. Many “sponsored” links are capturing key searchable words (called key words in SEO), not providing expertise.
Anti-Phishing Tools
These tools and information sites will help you to learn more about phishing and provide you with tools to verify suspect websites and files.
I urge caution when using these tools. Be sure you understand the terminology as well as the risks.
Suspicious Websites
Check to see if a site has been flagged for phishing:
- PhishTank is a collaborative clearing house for data and information about phishing on the Internet.
- urlQuery.net is a service for detecting and analyzing web-based malware.
- Forcepoint's CSI Ace Widget allows you to check a URL to see if the site is safe.
Check the site's information and/or disclaimer pages so you understand the capabilities and shortcomings of the service. The following is from urlQuery's“ About” page but can be applied to most such services:
Currently no service or security solution provides 100% detection of malicious content. The data provided is to help give a second opinion and should not be taken as fact. As with other sandbox technologies it can be detected which can skew or make the results inaccurate. Other issues might include browser incompatibilities or settings/configurations within the browser.
Cryptocurrency Scams
cryptocurrencies are electronically generated pseudo currencies such as BitCoin. They have become very popular because they allow for anonymous transactions and because of the extraordinary growth in their value.
As a result there are now multiple cryptocurrencies and they have become a common element in scams, both in their reward offerings and in the method of extracting payment from unsuspecting victims.
Kaspersky says that fake exchanges, fake mining hardware and wallet phishing are the most popular crypto scams of the year, many of which it said have a higher-than-usual level of detail.People investing or interested in this area are often more tech-savvy than the average user. Therefore, the cybercrooks make their techniques more complex in order to get data and money from these people
— TechRepublic
Don't fall for emailed offers of cryptrocurrencies. Think before acting. If it's seems too good to be true, it's probably a scam.
Only use apps from trusted sources.
Cryptocurrency apps that have to be downloaded from outside the official iOS, Android or other app store are generally dangerous, especially if the link is provided in an email from an unknown source.
Suspicious Files
Be cautious when checking out suspicious files. In most cases you're safer simply deleting the email along with the unopened suspect file unless you were expecting it from a trusted source.
Malicious Microsoft Office attachments are more common than malicious batch scripts and PowerShell scripts.
— Tech Republic
Security software is a must. Ensure that your security software is current. Scan new downloads before installing or running it.
Delete Attached Forms
If your security program detects a problem with an attachment, you'd best delete it rather than having the program treat it even if it is an essential file sent from a trusted computer.
More recent phishing attempts have provided an attachment to their messages which, when opened, replace the fake site with a form which accomplishes the same nefarious purpose — to get your information using deception. Don't be fooled. An unexpected attached form (or PDF or Zip file) is likely an attempt at identity theft. Even .DOCX and other Microsoft Office documents can be dangerous.
You're best to discard it rather than risk infecting your own computer by opening the attachment. Instead, print out a copy of the file on the original computer while disconnected from the Internet. The original computer needs to have a full security scan with a current and updated software.
Beware of Hidden File Types
Windows hides “known” file extensions by default. While they are known to Windows, many users don't understand the risks they can pose such as what sorts of files can infect your computer.
Several file types (including .EXE, .SCR, .COM and .BAT) are not safe to open, especially when received as an email attachment.
You should change your settings to unhide known file types.
Microsoft Office files, such as those with MS Word's .DOC and .DOCX extensions, can also carry dangerous scripts.
Checking Unknown Files
If you're unsure if a file is safe, you're better off deleting it than checking it out yourself. If you need the file, use one of these resources to check it out before opening it.
- ZoneAlarm Extreme's Threat Emulation opens unknown files in a virtual sandbox to examine what they do before you risk your computer's security.
Resources
The following sites deal with phishing.
- See if you've been part of an online data breach.
- Complete guide to phishing attacks: What are the different types and defenses?
- Mishing is the new phishing — and it's more dangerous.
- Phishing basics: Protecting yourself from online threats.
- How to protect yourself from scammers.
- Anti-Phishing Working Group on preventing phishing fraud.
- Phishing Is more common (and more dangerous) than ever — Here's how to stay safe.
Recommended Reading

419, fiction by Will Ferguson, looks at the issue of phishing from both the victim and perpetrator points of view. Strongly recommended.
419 takes readers behind the scene of the world's most insidious internet scam. When Laura's father gets caught up in one such swindle and pays with his life, she is forced to leave the comfort of North America to make a journey deep into the dangerous back streets and alleyways of the Lagos underworld to confront her father's killer. What she finds there will change her life forever… — GoodReads
Related Resources
On this site:
- Resources index
- Identity theft
- Phone fraud
- Computer support scams
- Mobile security
- Security strategies
- Your privacy at risk
- Oversharing on social media?
- Spam: unsolicited emails and mailing lists
- Passwords: your electronic signature
- Safely disposing of computers
Return to top
RussHarvey.bc.ca/resources/phishing.html
Updated: May 24, 2025

