Passwords: Your Electronic Signature
Strategies for generating and using effective passwords
Long & Strong | Brute Force Attacks | Unique
Compromised Passwords | Remembering Passwords
What About Passkeys?
All trademarks, company names or logos are the property of their respective owners.
Everyone uses passwords to protect their important and confidential information.However, most people are unaware of how insecure their passwords are, compromising their accounts and exposing them to hackers.
— ThriveMyWay
It takes PassGAN < 6 minutes to crack any kind of 7 character password, even if it contains symbols. Passwords > 18 characters are generally safe against AI password crackers, as it takes PassGAN at least 10 months to crack number-only passwords and 6 quintillion years to crack passwords that contain symbols, numbers, lower-case letters, and upper-case letters.
— Security Hero
Passwords Secure Your Online Accounts
Increasingly, our lives are lived online: banking, shopping, donating, e-filing taxes, corresponding, posting on Facebook, etc. According to Mozilla, the average person has 130 online accounts. That's a lot of unique accounts — each requiring a unique password that is strong enough to resist hacking.
Passwords Protect Authority
Think of passwords as an electronic signature or “Power of Attorney.” Anyone in possession of your passwords can make purchases, access your bank accounts, access or delete files backed up or stored online, change settings, even post libelous comments about others on your social media accounts.
Your passwords need to be protected diligently. Unfortunately, consumers seem to ignore such advice:
[T]rying to balance security and convenience may contribute to unsafe shortcuts: about half of consumers (45%) only change passwords for providers when prompted by the platform, when hacked, or not at all. The same percentage (44%) often reuse the same password on most of their accounts, showing that consumers still require education on smart password creation or password management tools.
— MasterCard: Securing the digital economy March 2023
- “123456” is the most commonly used password
- A data breach because of a weak password is experienced by around 30% of internet users
- 59% of adults in the US use either their names or birthdays in their passwords.
- Approximately two-thirds of Americans use the same password across multiple accounts.
- Around 13% of Americans use the exact same password for every account.
- — ThriveMyWay 2024
- 70+ password statistics for 2025.
- 125+ password statistics to inspire better security practices in 2025.
Creating Effective Passwords
Several factors are involved in securing our online accounts with effective passwords. The recommended password length on this page and within quotes is illustrative and may be insufficient.
- Generate long and strong passwords.
- Never reuse passwords on multiple sites (including variations).
- Don't use single sign-on (SSO).
- Change compromised passwords immediately.
Use a password manager in combination with multifactor authentication (MFA/2FA) to improve security. These factors make it easier for you to keep your online accounts safe and quickly respond if a data breach reveals your account details.
Poor Password Choices Common
Unfortunately, most people view passwords as something imposed upon them rather than something that improves their security.
- 51% of people use the same password for their work and personal accounts.
- More than 60% of people never update their passwords.
- 43% of people in the US share their passwords with others (more than half share them with their partners).
- Two-factor (or multi-factor) authentication can protect against 99% of common password security issues.
- Over 1/3 of Americans use the same password for multiple accounts online.
- At work, employees use the same password 13 times on average.
- 93% of people say their bank and financial information is the one thing they want to protect.
- — ThriveMyWay 2024
The fact that social media and advertisers expend so much effort to track your browsing history should tell you that information is extremely valuable to them.
NordPass and partners found that the most common passwords are incredibly easy to guess — and it could take less than a second or two for attackers to break into accounts using these credentials. Only 44% of those recorded were considered “unique.” — ZDNET
Poor security hygiene is a strong contributor to why so many people continue to have their accounts hacked or suffer from ransomware and other malware infections.
23andMe Deflects Responsibility for Breach
One possible outcome of reusing passwords or failing to change them once that password is compromised in any of your accounts is the dismissal of any claims for a data breach involving those accounts.
23andMe's lawyers sent a letter to victims of the breach claiming that the incident was a result of users' failure to safeguard their own account credentials:
23andMe believes that unauthorized actors managed to access certain user accounts in instances where users recycled their own login credentials — that is, users used the same usernames and passwords used on 23andMe.com as on other websites that had been subject to prior security breaches, and users negligently recycled and failed to update their passwords following these past security incidents, which are unrelated to 23andMe. Therefore, the incident was not a result of 23andMe's alleged failure to maintain reasonable security measures under the CPRA.
Make Passwords Long and Strong
Over two-thirds of users create simple passwords that can be hacked quickly — in less than one second, in many cases.
— Ipswitch
Generate passwords that are both long and strong to make them more difficult to guess and not easily discoverable.
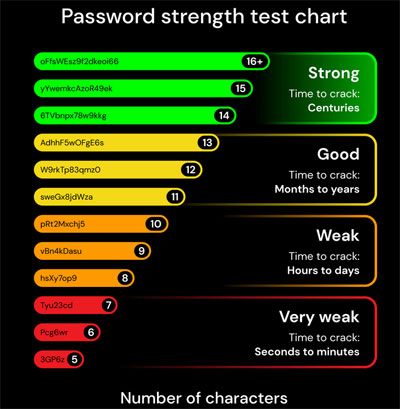
To strengthen the security of your online information, ensure your passwords are a random mix of at least 14 to 16 characters.To guide your password decisions, use the Password Strength Test chart below, which is based on the Bitwarden Password Strength Generator.
— Bitwarden
Bruce Schneier's Choosing secure passwords (2014) will give you a good idea of how passwords get hacked and reveals a great deal about hacker dictionaries (they contain lists of passwords that you'd think were great).
Longer Passwords More Secure
Passwords should be at least 14–16 characters long (I'd recommend longer where the site will allow it).
Of course, most of us don't know whether or not our data is on the dark web. The odds are that at least some of your passwords (and usernames and email addresses) are in a database of hacked accounts.That's why reusing passwords is so risky; hackers can easily use the same login combination on other websites.
— LastPass blog 2022
Strong Passwords Harder to Hack
Password strength refers to an assessment of how difficult it would be to break a password using current (or sometimes anticipated) technologies.
You should preferably use complex random characters if the site supports that. Use a random combination of letters and numbers interspersed with other characters where possible.
- Using mixed upper and lower case gives you effectively 52 letters to work from instead of 26.
- Including multiple numbers and other legal characters (such as the pound key, hyphen and the underscore) significantly increase the security of your passwords.
- Avoid starting with a capital and placing numbers and characters at the end.
New Technology Enhances Password Hacking
Newer, more powerful computers are being developed all the time and this raises the bar for what is considered a secure password. Hacking by “bad actors” financed by countries have the resources to obtain and use such equipment regardless of expense.
However, it may not be that expensive to obtain the necessary technology by using AI or by renting it:
I ran Hashcat on a Nvidia Tesla K80 — a GPU with 4992 cores that you can rent on AWS for $0.90 per hour (P2.xlarge). I started off by looking at the hashing capabilities of the K80, just to see how it fairs in comparison to a standard built-in laptop GPU.The K80 came out 16 times faster than an average Intel graphics card. The K80 can calculate ~800 million SHA-256 hashes per second…that's nearly 3 trillion per hour.
To be honest…it was far, far more successful than I had possibly imagined. Actually scarily successful…
Let me summarize. 20 hours. $0.90 per hour. That's just $18. 80% of 14 million passwords cracked.
- 2 hours: 48% of the passwords were cracked
- 8 hours: nearly 70% were cracked
- 20 hours: over 80% had been cracked
Let that sink in.
That's scary. Really scary. People need to make their passwords more secure. Replacing 'o' with '0' and 'e' with '3' does not make your password secure. Adding numbers and symbols to the end of a word doesn't either. It's too predictable.
— Alice Henshaw 2019
Password Strength Meters
Many sites will indicate an approximation of the strength of your password.
Don't use third-party sites to check the strength of your password. Even if these sites aren't attempting to hack your accounts the mere fact that you've revealed a password to any site other than the one you use it to sign-in potentially makes it vulnerable.
- Think you have a strong password against AI? Find out… (but not with your real passwords).
Wikipedia's password strength entry includes examples of weak passwords such as the default passwords supplied by vendors (e.g., “admin”) and passwords that are more vulnerable to a “dictionary” attack.
Password Restrictions
Many sites have restrictions placed on both the size of allowed passwords and their complexity (including the use of anything but alpha-numeric characters).
The allowed legal characters can vary by site. Most will allow all letters and numbers, but some symbols (like /, \, < or >) may not be allowed.
- Using a longer selection and correcting for the disallowed symbols will still provide for a stronger password of sufficient length.
- Some sites will only let you create an all-lower-case password, but will let you change that later. Make that extra effort to ensure your account remains secure.
I find it annoying that many of these sites only tell you their restrictions AFTER you've attempted to enter a new password, particularly the special characters that are not allowed.
Server Choices Affect Security
Even if you're using a decent password, the level of security used by the sites storing our information and how the password information is transmitted can make you vulnerable.
- Sites limiting passwords to eight alpha-numeric characters aren't bothering to encrypt stored passwords.
- If your password is stored in plain text then anyone, employee or hacker, has immediate access to your password and the other information the server has stored about you.
Most data breaches have occurred because of an employee either using a weak password that allowed access to the system or were themselves the perpetrator.
Passwords Vulnerable to Brute Force Attacks
Brute force attacks refer to the process of testing one potential password after another until the password is discovered.
When a hacker breaks into a company, they usually look for and download the entire password database.In short, not all encryption algorithms are built equally, and even worse, many companies don't protect their passwords correctly.
Some hashing methods are old and weak, and as a result can be broken by hackers. More commonly though, hackers take the stolen hashes, and begin to extract the passwords with a few methods.
— Hive Systems
This chart is a visualization of password vulnerability to brute force attacks in 2025. Be sure that all your passwords are in the green area of the chart:

Credit: Hive Systems
Using numbers, upper/lower letters and symbols in a password makes it harder to hack than a less complex password of the same length. Longer passwords are less vulnerable to brute force attacks.
That assumes the use of random characters and lots of other factors can considerably shorten the indicated timelines:
- Hacker “dictionaries” are faster than brute force attacks.
- If your password has been hacked elsewhere (even if yours wasn't the account hacked) it will be more vulnerable.
- Restrictions on passwords to only letters and numbers or to 8 characters can considerably weaken them.
- Patterns like starting with a capital letter and ending with numbers or symbols increase predictability.
Remember, passwords considered secure this year may be vulnerable next year. Clearly, the 12 character password length recommended by several online sources is inadequate. The emergence of AI and the ability to rent powerful computers by the hour is may have already greatly reduced the life-expectancy shown in the HiveSystems chart by the time you read this.
“Dictionary” Attacks
Since some combinations are more likely, the hacker will build a “dictionary” of potential passwords. This dictionary contains foreign words, places and patterns of characters that form commonly-used world-wide passwords. Data breaches have revealed personal information but also common passwords which are added to hacker dictionaries.
I had a client that used the name of a small village in Europe. He was shocked when I showed him that his “secure” password was included in a password dump used by hackers.
Don't Reuse Passwords
Would you feel safe if every apartment in your building used the same key to gain access? Reusing passwords or repeating phrases within your passwords is just as risky. Once hackers catch on, all your accounts are vulnerable.
Users tend to use a single password at many different web sites.By now there are several reported cases where attackers breaks into a low security site to retrieve thousands of user name/password pairs and directly try them one by one at a high security e-commerce site such as eBay.
As expected, this attack is remarkably effective.
— Stanford Security Lab
Generate Unique Passwords for Every Site
Without the aid of password management software, people tend to reuse passwords or generate similar passwords with an extra number or other modifier. This is not security-smart.
Passwords are immensely valuable, whether they are for email, e-commerce sites, or even “just” a social media platform. Criminals aren't after your Spotify passwords because they want to see who your favorite artists are.They are banking on the high likelihood that the same password will unlock your email, retail Website, or even your work network.
— Check Point blog
By generating a unique password for every site, each site obtains only your name, email and whatever other information you provided directly to that particular site. The fallout is limited to that one site.
Hundreds of online accounts can be compromised in a data breach on any given day. Reusing passwords could put your most sensitive accounts at risk. Compromised accounts are vulnerable from anywhere in the world.
Make Them Random
Unfortunately, people are creatures of habit and tend to follow the same sort of process in creating passwords such as familiar names (girlfriends, sports teams, etc.) and predictable patterns.
Respondents also retain a fondness for “keepsake passwords” including personally significant details as a family or pet name, a birthday or other important date, or a current or previous address, with 48% reporting that practice the last time they created or updated a password.
— PCMag
Patterns Make Passwords More Vulnerable
Passwords with simple phrases or common combinations are easily guessed.
If you can say your password (even with variations like “password with a zero”) it can be compromised in as little as one second using a dictionary attack.
We tend to start with a capital and leave the numbers and special characters at the end. This makes their discovery easier.
Avoid simple substitutions like @ for a, 3 for e and 0 for o (e.g., N3wP@ssw0rd1922!).
In one 2010 case study, the top three compromised passwords were 123456, password and 12345678.
— Duo Security
Keyboard Sequences NOT Secure
Keyboard sequences like qwerty, or zxcvbnm or patterns like “Z” on the number pad appear to be complex passwords. 123456 is used by 17% of users.
This practice is known to hackers, yet is still common according to the information culled from recent exploits.
Single Sign-on (SSO) Flawed
Single sign-on (SSO) uses your Google, Facebook or Apple ID to log into third-party sites.
If you've signed up for access to third-party sites using your Facebook or Google account rather than creating a new user name and password, you may want to revoke that access. SSO may be convenient, but creates a single point of failure.
But for all its convenience, consumer SSO has some real drawbacks, too.It creates a single point of failure if something goes wrong. If your password or access token gets stolen from an account you use for SSO, all the other sites you used it to log in with could be exposed.
And not only do you have to trust the companies that offer SSO to protect your privacy and security, you also have to trust all the third-party websites offering these options to implement them correctly.
— Wired
“Browser in the Browser” Attacks
A new “fake browser” phishing attack called “browser in the browser” (BITB) can take advantage of JavaScript, SSO and a fake login window to obtain the user's password. The fake window can fool all but the most astute observer with some understanding of how JavaScript and the login should look.
Browser in the browser attacks consist of simulating a browser window within the browser to spoof a legitimate domain. The attack takes advantage of third parties' single sign-on (SSO) option, which has become increasingly common for users to log into many different websites.The principle is pretty straightforward: The user connects to a website, which in turn opens a new browser window that asks for Google, Apple, Microsoft or other third parties' credentials, to allow the user to log in.
This benefits the user because they don't need to remember or use an additional password to log into the website.That's where the BITB attack comes in. In a BITB attack, the user is being served a fraudulent pop-up window that will request their SSO password. The main difference from a usual phishing case lies in the fact that in addition to popping up that window, it can show any URL, including a legitimate one.
The trick works well. People have become so used to this authentication model that they do not really pay attention to it anymore and just type their credentials to log in.
— Tech Republic
SSO Can Threaten Your Privacy
While sites using SSO may not be provided with your Facebook or Google password, they can access information that allows them to improve their profile of you.
That website obtains unlimited access to your social media profile — your interests, friends, occupation, religion, political views hobbies, etc.
Logging in to a website using a service such as Facebook or Google allows the website to make a request for data about you.Linking two or more sites allows companies to collect more data, building an increasingly rounded profile about you.
Allowing one account to have access to others means that if the least secure account is hacked, the rest could also be compromised.
— Natasha Stokes
Facebook and Google both collect vast amounts of data on users then resell it to others, threatening your privacy. These two companies control nearly all Internet advertising revenue.
Change Compromised Passwords
It is a good idea to change your passwords regularly but is critical after you become aware that one has been compromised in a security breach.
Frequent password change policies sound good, but they only work if you employ a password manager. Otherwise people tend to use weak passwords because they are easy to remember.
Sharing Passwords Risky
A surprising number of people share passwords without changing them afterwards.
- 79% of consumers admitted to sharing passwords with someone outside their home.
- 7% of Americans are worried about their home or devices being hacked.
- Only 13% of Americans said that identity theft is their biggest home security fear.
- Video streaming and delivery service passwords were the most likely to be shared outside the home at 35% and 29%.
- — The Zebra 2024
When you share a password, especially if it is done insecurely, you create a vulnerability that could cost you your privacy or empty your bank account.
Sharing Streaming Passwords
Many people share their streaming passwords with friends, family and others. You may justify this with cost savings, but sharing your streaming passwords is putting your privacy and personal data at risk.
The general consensus is that the only "victims" of password sharing are the streaming service companies, but the issue is often much more complex than that. Online hackers can infiltrate almost any device, find passwords, and learn other personally identifying information about you that they can use to steal your identity. And this risk only increases the more your account is used.Our survey showed that Americans are much more concerned about their homes getting broken into (33%) or a house fire (28%) than any online threat. But given that 39% of people use the same password for everything, hacking is a much greater threat than most people realize.
— The Zebra 2024
Sharing Passwords Between Work and Home
What about using the same passwords at home and at work? This reduces the protection of both your personal and your business accounts.
What's frightening is that 47% of survey respondents admit there is no difference in passwords created for work and personal accounts.Which means that one re-used password has the power to compromise an entire organization's network. A company's network security is only as strong as their weakest link — the employees.
Poor security habits can leave that door wide open for hackers.
— LastPass blog 2018
The irony is that LastPass was compromised because an employee used an insecure home computer to gain access to the development environment and users' encrypted vaults. The vulnerable software on the home computer allowed malicious actors to follow him in, recording the security protocols in the process. LastPass was severely compromised.
Remembering Passwords
Remembering complex passwords can be extremely difficult.
Even a password manager requires you to memorize your master password to protect your vault.
Memory Helpers
Remembering passwords can be made easier by using “memory helpers.” Having a sentence that makes sense to you, but is not easily discovered could be one solution.
- You can use the first letter in each word of a phrase that makes sense to you.
- For better security, you want something that combines upper & lower case letters, numbers and, where possible, symbols.
"Jason plays the Grand Piano on the 2nd & 4th Fridays in December" can help you remember JptGPot2&4FiD.
Longer passwords are now necessary. I recommend using 20+ random characters
Avoid Common Quotes or Slogans
Avoid phrases that are easily guessed, like frequently-quoted Bible verses or company slogans. There is a limit to how many of these clever phrases you can create and remember.
I recommend a password manager to generate a long and strong password to protect your online accounts. The a password manager's password must be even stronger because it protects all your other accounts.
Be Careful With Lists
Be conscious of how you keep records of your passwords and don't use vulnerable locations which can easily be compromised.
- Don't keep passwords on Post-it notes stuck onto your monitor where visitors and other employees can see them.
- If you keep a list of passwords in a file on your computer, be sure it isn't recognizable as such.
Images Containing Text Not Secure
A version of malware called SparkKitty reveals that information captured within images such as screen captures such as passwords, seed phrases and other sensitive information can be hacked.
Kaspersky found some SparkKitty versions that use Google ML Kit OCR to detect and only upload images containing text.Ultimately, cryptocurrency holders should not keep images of their wallet seed phrases on their mobile devices, as these are now actively targeted by malware. Instead, store them offline in a secure location.
— BleepingComputer
Generating Passwords
Most humans tend to use recognizable patterns when creating passwords. You want to create passwords that are long and strong that are unique for every site or application.
I recommend using a password manager to generate your passwords since they are then stored in a secure manner and usually available for use on multiple computers and devices (depending upon the one you choose).
Password Generators
Password generators are the electronic versions of the one-time coding pads you may have read about in the history books. Random-generated passwords provide better security because users are unable to select passwords that are easily compromised.
Be sure of the integrity of the site or app before depending upon the passwords it generates.
- Ultra High Security Password Generator will generate new passwords every time the browser is refreshed. Choose from the middle line where possible.
What About Passkeys?
Passkeys are a pair of cryptography keys (one public; one private) that are generated by your device. Passkeys are a much better solution for the websites that support them. Most such sites require you to set up a traditional password-based account first, then providing an advanced option to set up a passkey in settings.
Passkeys have plenty of benefits; for example, they cannot be guessed or shared. Passkeys are resistant to phishing attempts because they're unique to the sites they're created for, so they won't work on fraudulent lookalike sites. Most importantly, in the age of near-constant data breaches, your passkeys cannot be stolen by hacking into a company's server or database, making the data extracted in such breaches less valuable to criminals.
— PCMag
- Passkeys: What they are and why you need them ASAP.
- How to set up Apple's passkeys for easy sign-ins.
- Sign into Google with a passkey instead of a password.
- Lance Whitney: I set up passkeys for my Microsoft account.
Passkey Support Added to Windows 11
Microsoft added passkey support to Windows 11 in the September 2023 Moment 4 update. After you've set up passkeys for some sites, you can view them here:
Start ⇒ Settings ⇒ Accounts ⇒ Passkeys
Related Resources
On this site:
- Resources index
- Multifactor authentication
- Password managers
- The LastPass breach
- Security basics
- Security strategies
- Security policies
- Data inheritance
- Encryption: protecting your data
- Identity theft
Return to top
RussHarvey.bc.ca/resources/passwords.html
Updated: June 26, 2025