Identity Theft
Obtaining information by deceit
Identity Theft | Protect Your Identity | DNA Tests
Recommendations | Reporting ID Theft
Credit Reporting Agencies
All trademarks, company names or logos are the property of their respective owners.

Protection against identity theft and other scams are contained in these pages:
- Identity theft
- Vishing (phone scams)
- Phishing (email scams)
- Computer & "tech support" scams
- Ransomware
This page will help teach you how to prevent yourself from becoming a victim of identity theft.
When your identity is stolen, you lose some things, but gain others.You could lose all the cash in your bank account, or the title to your home.
But you might gain a criminal record, or a lien on your home mortgage.
— PCMag
93% of cybersecurity experts and 86% of business leaders believe global geopolitical instability is likely to lead to a catastrophic cyberattack in the next two years.
— MasterCard: Securing the digital economy March 2023
The information was written with computers in mind, but these warnings also apply to smartphones and tablets.
Obtaining Information by Deceit
Fraudulent phone calls, phishing emails and fake error messages generated by malware or website infections are all forms of identity theft perpetrated on innocent victims every day.
Identity theft is obtaining information about you that will enable someone else to impersonate you, allowing them to use your identity rather than their own.
While the thief obtains financial or other rewards, you are left with the financial loss or debt and may face criminal charges for crimes committed while using your ID.
The best thing you can do to thwart an attacker is to not respond to lures, texts, emails, and phishing scams. Don't blindly click links. Don't blindly open email attachments. Add two-factor authentication to as many Web logins as possible. Never hesitate to get in touch with a bank if you find something that doesn't feel right — banks are as eager as you to stop fraud as soon as possible.
— Susan Bradley
Unfortunately, it is much easier to obtain credit online than it is to prove that it wasn't you that made the application.
Identity theft can be prevented.
Examine your security practices closely to see if they are up to protecting your online identity and privacy.
A Rapidly Growing Crime
Identity theft is a rapidly growing crime.
- Cybercrime is very profitable and low risk.
- Criminals seldom get caught or prosecuted because most are located overseas.
- Using the Internet exposes you to the world's criminals.
- The vast number of gullible “marks” ensures success.
- Corporations are more interested in profiting from the information they gather online than securing that information.
- Data breaches weaken our security without significant penalties for that business.
People place themselves and their money at risk when they ignore security protocols and fail to learn about cybersecurity.
- Most criminal activity is based upon threats or transfer of trust.
- People don't understand the technology they're using.
- Mobile phones provide additional avenues of attack using deception and SIM card swapping.
- We treat cybersecurity like something imposed on us rather than something protecting us.
How much do you know about cybersecurity?
Test your knowledge about cybersecurity.
The content on this page will help you to avoid becoming a victim of identity theft.
It Used to Be Harder
Obtaining personal information is much easier than it used to be.
At one time you had to go to your bank branch, speak to a real person who would then compare your signature with a physical signature card stored at the bank to ensure that you were who you said you were before releasing funds or a providing a new credit card.
Credit Information Easily Accessed
These days credit card applications appear unsolicited in your mailbox and are easily obtained online.
- Verification depends upon electronic data rather than hard paper copies.
- The convenience of inter-branch banking and online transactions has resulted in poorer security.
- Compare the four-digit PINs securing an ATM to the requirements to avoid brute force attacks.
- Using your smartphone to do banking has additional risks, especially if your device is lost or stolen.
The convenience ends when there is a problem and the bank demands paper documents to prove your innocence.
Passwords: Your eSignature
For online transactions, passwords have replaced a signature (or the wax seal that kings once used).
Many people really don't understand this form of electronic verification and view it as something that is imposed upon them rather than something that protects them.
[R]ecent Verizon research shows…unsecure passwords are the cause of over 80% of all data breaches at companies.
— ZoneAlarm
Take Your Passwords Seriously
Unfortunately, many don't take their passwords seriously.
Afraid they'll forget a password, they make it simple and use variations of the same password for every account they create.
Though 91% of the respondents profess to understand the risks of using the same passwords across multiple accounts, 59% said they did so anyway. For 61%, it is the fear of forgetfulness that was the primary reason for password reuse. Fifty percent say they reuse passwords across multiple accounts because they want to know and be in control of their passwords all the time.
— DarkReading 2018
Once hackers have one password, they can use it to hack into other services, just like a Twitter hack that exposed users data because an administrative assistant reused passwords:
A hacker found a personal e-mail account for the administrative assistant previously mentioned.[T]he hacker researched social networking sites to find the answer to the "secret question" required to reset the account's password.
In going through the e-mails in the account, the hacker apparently found the password used by the administrative assistant on other sites, and correctly assumed that person used that password on their Twitter corporate account at Google Apps.
— Ira Winkler
Weak Passwords Like Signed Blank Cheques
Think of your passwords as a series of unsecured, pre-signed blank cheques. The only dollar limit is the size of your bank account.
Use a Password Manager
Learn how to create quality passwords and take advantage of other options like multifactor authentication to protect your online accounts.
A good password manager not only helps to provide unique and strong passwords for every site, but also can protect you by warning you when the site address doesn't match the address recorded for the site.
Unfortunately, password managers don't work on the CRA website because of very unusual and unnecessarily complicated login procedures. The CRA's suggestion? Manually enter the password!
Don't Post Answers to Security Questions
Be careful NOT to post the sorts of information on social media typically used for the “forgot my password” recovery.
We found that 51% of people believe there is no way a hacker could guess one of their passwords from information they've shared on social media.But we know hackers aren't dumb — if you're being targeted and don't have a strong password guarding your account, it would take a hacker seconds to do a search on your social media profile, learn the name of your pet, family member — even learn when your anniversary is — and use that info to guess your password.
Don't make it that easy for them — try to be a bit discreet on social media.
— LastPass Blog (2018)
Choose Your Software Carefully
You probably check the doors and windows in your house before going to bed at night.
You need to secure your computer and software with the same diligence.
Ignorance is Your Undoing
Many people don't understand the risks of using obsolete or unsecured technology, especially the software you use to access the Internet.
Cybersecurity researchers have discovered a malicious Android app on the Google Play Store that enabled the threat actors behind it to steal approximately $70,000 in cryptocurrency from victims over a period of nearly five months."Fake reviews and consistent branding helped the app achieve over 10,000 downloads by ranking high in search results…."
— The Hacker News
Online security is inconvenient but so are seat belts, door locks and insurance.
Choose a good security suite then learn how to use it to protect your computer and your privacy.
Victims Unfamiliar with Technology
Most of the victims of identity theft are using technology they don't understand.
- Victims use passwords that are easily guessed and often reused elsewhere.
- Their passwords may have been compromised in a data breach (that's why you change ALL your passwords when you're notified of a breach.)
- Victims don't use a password manager much less unique and strong passwords for every account.
- Victims run obsolete email programs and vulnerable web browsers with obsolete or insecure addons and vulnerable plugins.
- Victims are unwilling to learn about risky behaviour or change their habits to reduce those risks.
The politicians making the laws that are supposed to protect you seldom understand the effects those laws will have on privacy. They obtain most of their advice from the very companies that are exploiting consumers on the Internet.
Protect Your Identity
Everyone is Gathering Information
Everyone is collecting information about you and your profile is available for sale to anyone willing to pay.
Do NOT buy into the myth that privacy means you have something to hide.
Companies spouting the “nothing to hide” line claim they're “just collecting metadata”, but will accuse you of hacking if you returned the favour.
[T]here is another reason websites track you — it's because you're worth a lot of money.Websites record your activity so they can sell your information to third party advertising platforms, essentially delivering ads that they hope are relevant to you.
— Check Point blog
If they know your email address, they can send their advertising right to your inbox.
The more you reveal, the easier it is to target you — your marital status, how many children you have, where you live, your income, your hobbies, etc. These factors identify potential markets.
Loyalty Cards
Loyalty cards can provide you with free merchandise and more, but provide advantage to retailers such as allowing them to track your purchases. Apps on mobile devices have been used to track your location without your permission.
Retailers like Home Depot ask if you'd like an email receipt. That's a sneaky way to obtain your email address.
Your Purchases Reveal a Lot
The sorts of items you buy, particularly the precise combination of items, can tell a lot about you.
Target determined that a teen customer was pregnant before they or their family knew — based simply upon tracking product purchases.
Protect Personal Information
Do not post or release personal information over the phone. Never reveal the following sorts of information to an unverified caller:
- Social Insurance/Social Security Number (only legislated uses require you to disclose your S.I.N.).
- Mother's maiden name.
- Where you were born.
- Your birth year.
- Bank PINs.
- Passwords.
- Passport information.
- Driver's licence.
Be careful about revealing billing addresses and employment information as well.
Legitimate financial services organizations like banks and credit card companies will never send you an email asking you to provide personal or confidential information (such as your debit or credit card number, passwords or identification such as Social Insurance Number or Driver's Licence).
The successful completion of many credit card transactions may require that your shipping address match the credit card's billing address.
This information is not necessary for most other transactions.
Posting on Social Media Sites
People casually post things on social media or reveal them to strangers without thinking about the consequences.
Facebook and Google already know more about you than your family and friends do (and they never forget).
Information that allows you to recover a lost password should be something you remember, but strangers can't know. That security is lost if you post that information on social media.
These personal facts are commonly posted by people:
- Family genealogy.
- Pet names.
- Former residences and occupational history.
- Your school, favourite teachers and other educational information.
- Sports teams and celebrities you admire.
- Where you were born and where you have lived.
- Life milestones such as marriage including dates and locations.
Password Recovery
Unfortunately, these answer the commonly-used questions that password-recovery options employ.
Most accounts are compromised by using the password recovery mechanism which invariably requires the correct response to the very personal questions people post on social media.
Sure, you will remember the answers (the reason companies use them), but so will everyone that views your posts. It isn't just your friends and family — hackers use social media too!
These “security” questions are also too easy to research or bring up in casual conversation.
"The Cloud" Has Risks
Online storage and services (“the cloud”) have become unavoidable as we use our computers, smart phones, tablets and other portable devices to conduct business on the go.
While it may free you to access your information anywhere at any time, it also provides the same access to anyone in the world with an Internet connection.
- All that is needed to obtain access is your email address and password.
- Poor password choices make it too easy for hackers to obtain access.
The stories you read about hacks & security breaches are only the tip of the iceberg. Not only do many organizations fail to report breaches promptly, they often take months to do so, choosing a “slow news day” to minimize reputational damage.
That means that your compromised passwords and data are often on the Dark Web or in the hands of foreign governments long before you become aware of the problem.
- How do you secure the cloud? New data points a way (2020).
- 7 top cloud security threats — and how to address them.
Banning Encryption Short-sighted
Legislation is pending in some locations (including in the US and possibly Canada) to ban consumer encryption or to ensure that back doors for police access are added. This is very short-sighted.
- Effective encryption could help reduce the risk of hacks like those noted above.
- Back doors are vulnerable to unauthorized access. There is no such thing as a vulnerability that is only accessible to the “good guys.”
- Weaknesses in software, especially unknown (or zero-day) exploits, make us all more vulnerable.
Yes, encryption is used by criminals. So are roads, public utilities, the Internet, etc. Should we remove everyone's access to those resources as well?
It would be better to close more zero-day loopholes rather than hope that criminals and foreign governments don't use them to defeat our security protections.
Personal DNA Tests
Most people would be leery of any request to fingerprint them yet millions have ordered personal DNA tests without considering the potential privacy issues.
Tracking your genealogy has become very popular. Sites like Ancestry and 23andMe offer kits to take your DNA and use it to tell you more about your family history. There is nothing more personal than your DNA.
This has never happened before. It hasn't happened with fingerprints, it hasn't happened with DNA. Until now there's been a line, that unless you commit a crime we don't record the facts of your body.
— Alvaro Bedoya
DNA Tests Risk Your Privacy
Before purchasing and submitting a DNA test kit, consider the privacy risks for yourself and all those related to you. Also, consider if you'll be able to handle knowing that your DNA indicates a potential risk for cancer or other disease, particularly if there is nothing you can do to prevent it.
Genetic testing kits help you find the missing branches in your family tree, learn about migration patterns, and even reveal potential health issues.Personal DNA testing is more popular now than ever before, as it can be done quickly in the comfort of your own home and at an affordable cost.
— PCMag
If your DNA information is compromised, it is impossible to correct that loss.
Unlike your credit card number or your bank account password, if your genetic information is stolen or simply given away without your consent by a company that possesses it, it can't be changed.
— Consumer Reports
23andMe: Additional Risks
23andMe is one of several companies offering DNA testing kits. However, there are additional risks because of a 2023 data breach and the very real possibility that your DNA data could be sold to anyone without regard to how that data could be used. Any of 23andMe's promises of privacy or protections for your DNA data wouldn't necessarily apply to the purchaser, especially if the purchaser is outside of the United States.
The 23andMe Data Breach
After 6.9 million users had their data stolen from 23andMe, they sued. The company responded by blaming the users based upon the re-use of passwords revealed in a previous data breach.
While the users were negligent in failing to update their passwords, the company didn't go far enough to protect against brute force attacks which must have occurred to gain access to the data of all 6.9 million users.
After 23andMe's board of directors resigns, the president of encrypted messaging app Signal joins other security experts in urging 23andMe users to consider deleting their data.If you ever used 23andMe, you might want to consider deleting your data while you still can. The company's financial troubles are prompting concerns about what could happen to customers' DNA data if the firm goes under or is acquired by someone else.
— PCMag October 4, 2024
Deleting Your 23andMe Data
You can request that your data be deleted. Be sure to read the details before starting.
It's still possible to delete your data or your entire account. Navigate to Settings, scroll down to the 23andMe Data section at the bottom, and click View on the right. Enter your birthday, scroll to the bottom of the next page, and click Permanently Delete Data.
— PCMag March 24, 2025
23andMe has an automated account deletion process. If, at any time, you are no longer interested in participating in our Services, you may delete your 23andMe account directly within your Account Settings.If you participated in 23andMe Research, your Personal Information will no longer be used in any future research projects. If you asked us to store your genetic samples, they will be discarded. We will retain limited information about you, including records of this deletion request, and other information as required by law and otherwise described in our Privacy Statement.
— 23andMe
Privacy Costs
But these sites aren't as private or innocuous as they'd have you believe.
When you're consenting [to the terms and conditions], you're not only consenting to [use of] your own DNA, but you're in effect consenting on behalf of everybody you're related to. Our laws of consent are not really designed for something like this.
— B.C.'s Privacy Commissioner
In fact, they sell your DNA data to third parties and often retain more rights to your DNA than you do once you agree to their contract.
But the DNA and genetic data that Ancestry.com collects may be used against “you or a genetic relative.” According to its privacy policies, Ancestry.com takes ownership of your DNA forever. Your ownership of your DNA, on the other hand, is limited in years.
— Joel Winston
Other Potential Implications
There are other potential costs to these tests because DNA companies are bound to look at other means to profit. All sorts of third-parties could benefit economically from purchasing personal DVA results.
In an internal memo, Pentagon leadership has urged military personnel not to take mail-in DNA tests, warning that they create security risks, are unreliable and could negatively affect service members' careers. [S]ervice members were encouraged to get genetic informationfrom a licensed professional rather than a consumer product.— New York Times
Consider how health and life insurance companies could use DNA indicators of risk including potential cancers to affect either your eligibility or premiums. Imagine if DNA-indicated diseases were excluded from such benefits.
Potential employers could use this data to screen job candidates and it could affect your ability to collect from a class-action lawsuit if your DNA indicates a higher than average risk for the cause listed in that action.
If You're Going to Proceed
If you're going to get involved with these companies, realize that they hold all the cards. Be sure to examine their privacy policy and opt out (where possible) for your own protection.
Once your DNA (or that of a close relative) is provided to one of these agencies, there is no going back.
- 23andMe trouble sparks calls for users to delete their DNA data: Here's how.
- 23andMe confirms hackers stole ancestry data on 6.9 million users.
- 23andMe tells victims it's their fault that their data was breached.
- Ancestry receives German “big brother” award for misleading information.
- Your genetic data isn't safe — Consumer Reports.
- DNA tests expose more than we think.
- Genetic testing firms share your DNA data more than you think.
- Your DNA is a valuable asset, so why give it to ancestry websites for free?
- How DNA companies like Ancestry and 23andMe are using your genetic data.
- 5 biggest risks of sharing your DNA with consumer genetic-testing companies.
- Ancestry.com takes DNA ownership rights from customers and their relatives.
- The pros and cons of genetic testing.
- How to delete your data from every DNA testing service.
Recommendations
Much of the Internet is broken, a result of greed and exploitation at the expense of those who simply want information and entertainment but don't consider the risks of their behaviour.
It is recommended that you examine your security practices closely to see if they are up to protecting your online identity and privacy.
Anyone telling you otherwise is probably exploiting your ignorance.
Protect Your Phone
Your smart phone is a portable computer with access to a great deal of your personal data, not to mention a very common method of multifactor authentication.
That smartphone in your pocket is an identity thief's dream. It has your email, IM, social media, and other apps, potentially logged in and available. It contains personal data galore, including all your contacts.A thief who has unfettered access to your phone owns your identity, period.
— PCMag
Watch Out for Malicious Attachments
One of the most common methods of attack are to send a phishing email with an infected attachment.
Learn more about safer email practices including how to avoid malicious attachments.
Revealing Email Headers
If you have issues with an email you received, you'll be asked to look at and possibly submit “the headers.”
Use Encrypted HTTPS Sites Where Possible
HTTPS is a secure protocol used by websites that encrypts traffic between the site's server and your browser.
Few sites use the old HTTP protocol by default (but may load it if you directly request it based upon a link you're following or a bookmarked site).
If you load just the domain name (e.g., domain.com) into your browser's address bar, it should load a secure site if one is available. Be sure to change your bookmarks accordingly.
Today, most current websites are secured with HTTPS so HTTPS-only mode is a viable option to prevent you from loading insecure sites without a warning.
Choose a Safer Browser
Your choice of web browser can make a difference in your ability to remain safe online.
Keep it Updated
Whichever browser you choose, the most recent version will usually have improved security features and/or have known security issues patched.
Firefox Recommended
Firefox is a much safer browser to use. As an independent stand-alone product it is less vulnerable to cross-program security issues.
Because it isn't tied to an operating system or a search company, it can focus on its users rather than those controlling the purse strings.
Stop Using Google Chrome
Google Chrome has huge privacy risks, especially if you sign into your Google account while surfing (even if it is only for checking your Gmail).
Google makes their money by exploiting information you provide. Google NEVER forgets.
The widespread use of Chrome also gives Google a huge amount of control over how the Web works.
Don't Use Internet Explorer
Internet Explorer was so tightly integrated into Windows that any security issue in any Microsoft product put your entire computer at risk.
Microsoft should have killed it off with the release of Windows 10 when IE was retired by Microsoft but too many companies had embedded direct calls to IE (now redirected to Edge). The fact that components remain ( C:\Program Files (x86)\Internet Explorer) is a security vulnerability.
More About Browsers
Learn more about web browsers and plugs, vulnerabilities in Internet software and how to browse safer.
Additional Resources
More information about how to prevent identity theft:
- Prevent identity theft with these 11 essential steps.
- How to protect yourself against identity fraud.
- How to enable data theft protection measures.
- Fraud Awareness & Prevention.
- Privacy, identity & online security — US Federal Trade Commission.
- BetterDefend's articles on identity theft.
- How to best protect senior citizens from scams.
Report Identity Theft
Are You a Victim?
If you have been a victim of identity theft (or suspect you have), contact the police to report identity theft.
Begin Immediately
If you suspect you've been the victim of identity theft, the sooner you act, the sooner you can begin to resolve the issue.
- Canadian Anti-Fraud Centre (also known as PhoneBusters.com).
- Identity Theft Resource Center (1-888-400-5530).
A Long-term Problem
It will likely be harder to prove identity theft than to execute it.
If you are the victim of identity theft, you can expect to fight to regain your credit rating for years.
Victims report that it takes months or years to regain their credit rating, only to find that a new report forces them to start all over again.
While electronic data can quickly get you into trouble, financial institutions want physical evidence (i.e., paper copies of their official forms) that show you're not responsible.
Think of how hard it is to obtain physical copies of documents generated by someone else.
Huge Financial Costs
There are huge personal and financial costs if you become a victim.
- What to do if you think you've been scammed.
- So, your account was hacked. What now?
- Victim of an identity fraud incident? Do these 6 things.
The Canadian Anti-Fraud Centre at 1-888-495-8501 can help you through the process.
File a Report
You should file a report with your local police, your financial institution(s) and with credit reporting agencies.
But there's not much your local police can do for you. For starters, you'd have to show that an actual crime happened, which is much more difficult when it's digital.
— CNET
When reporting improper use of a credit card to our local police we learned that purchases had been made out of province and mostly without presenting the physical card. How someone could get away with paying off a utility bill for a fixed address with a stolen credit card is confounding.
Unauthorized Purchases
Check your bills for unauthorized credit cards or charges for goods or services you did not receive (particularly from a foreign country). In most cases you have to still pay the full bill and notify the credit card company about unauthorized charges within 30 days.
Try to identify unauthorized charges before your statement arrives:
Take advantage of your bank and/or credit card company's offer to text or email you when transactions are made on your account. This is the quickest way to identify unauthorized purchases on your account.
If that service is unavailable, you can log into your online accounts daily to check activity, including your banking services, credit cards and investment accounts.
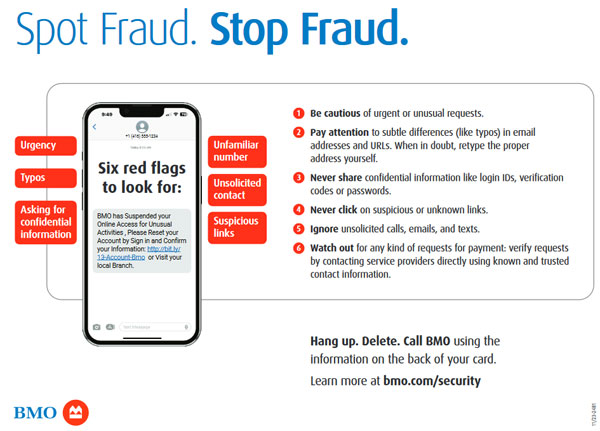
Beware of Unsolicited Calls
We're calling from VISA.…
Unsolicited phone calls about your credit card are usually fraudulent attempts to secure your credit card information.
In most cases you'll receive an automated call about “your MasterCard and VISA” but these can also warn you about unauthorized purchases on Amazon or other online retailers.
These calls may attempt to scare you with claims that very large purchases “have been noted on your credit card.” Notice they don't specify the card used.
Never respond to requests to prove your identity or verify your card details. Remember, they called you.
Call your bank, credit card company or online retailer using the phone number provided on your statements or the back of your credit card.
Credit Reporting Agencies
Reporting identity theft or fraudulent transactions on your credit card(s) to the credit reporting agencies helps to prevent further abuse, particularly if someone tries to open new credit in your name.
- Equifax (1-866-828-5961).
- Experian (1-714-830-7000).
- Innovis (1-800-540-2505).
- TransUnion (1-800-663-9980).
Free Credit Report
You are entitled to one free credit report each year which discloses who has made requests for your credit report as well as allowing you to dispute errors.
Credit Freeze
A credit freeze is a very useful tool in preventing unauthorized credit being established in your name. Unfortunately, it is not available to consumers in Canada outside of Quebec.
Also known as a security freeze, a credit freeze prohibits the credit bureau from sharing your credit information or personal data when a lender or creditor tries to access it.
So, if a fraudster steals your information and tries to open a new credit account in your name, they're unlikely to succeed as the lender won't be able to properly vet them.
- A credit freeze prevents access to your credit report to help protect you from fraud.
- Currently, credit freezes are only available to residents of Quebec.
- Alternatives to credit freezes are available to protect yourself from fraud, such as credit monitoring and fraud alerts.
Credit freezes are especially important during data breaches. If a bank, financial service provider, or even the CRA experiences a data breach, you might be at risk for hackers and fraudulent activity.
Unfortunately, however, credit freezes don't stop fraudsters from accessing your existing credit accounts altogether, or from conducting any other credit activities that don't require a credit check.
— LoansCanada
What About Subscribing to Monitoring Services
I'm a bit suspicious of such services, especially if they say they can scrub your data from the Dark Web.
So what, if anything, should you do to ensure your identity is safe? Should you subscribe to a dark Web monitoring service? Sign up for credit monitoring, which is typically offered when such an event occurs?My recommendation? Don't bother with a service touting that it can scan the dark Web on your behalf. As nefarious as it may be, the dark Web is made up of overseas technology hackers and is a moving target, an ever-changing threat landscape. A commercial service claiming to be able to keep up with these criminal gangs is just kidding itself.
— Susan Bradley
The same can be said for services claiming to protect the title to your home and similar assets against theft or fraud.
Related Resources
On this site:
- Resources index
- Phishing & email scams
- Phone fraud
- Your privacy at risk
- Oversharing on social media?
- Spam: unsolicited emails and mailing lists
- Passwords: your digital signature
- Safely disposing of computers
Return to top
RussHarvey.bc.ca/resources/identitytheft.html
Updated: March 29, 2025