Malware
Detection & removal
Popup Warnings | Removal | Spyware | Keyloggers | Stalkerware
See also: Ransomware
All trademarks, company names or logos are the property of their respective owners.

What is Malware?
Malware is software designed with malicious intent. It secretly gathers information about you (sometimes called spyware) or your private communications and attempts to gain access to restricted or secure systems. It then forwards this information to the malware's owner.
Slow Computer?
If your computer seems to be slow, this is one indication that you're infected. Malware runs constantly, stealing your computer's resources which slows down legitimate programs and processes.
You Need a Security Suite
Traditional antivirus software cannot deal with malware unless it contains special anti-spyware/anti-malware components and maintains a current database of malware and how to remove it. This is why the term security software is more appropriate for the suite of complementary programs that protect your computer and its data.
Potentially Unwanted Programs
Brand Name Computers with Bloatware
Some software that comes with name-brand computers is called Potentially Unwanted Programs (PUPs).
While you've agreed to install these programs when you accepted the computer vendor's licence, you want to remove such programs in most cases. At the very least they are bloatware and likely a threat to your privacy or worse.
- Isn't it time we declared our independence from bloatware?
- Should I Remove It? helps remove unnecessary programs.
- Krebs's 3 Basic Rules for Online Safety.
Addons to Free Software
PUPs such as McAfee Scan, Yahoo! Toolbar, Google Chrome, etc. can be installed along with downloaded free software. This is a method many developers use to “pay” for software they provide for free.
These programs can usually be deselected either prior to download or during the install. Rather than simply clicking through the various download and installation screens, ensure that you understand what you're actually installing. If you're unable to deselect the unwanted software you may not wish to install that program.
Malware is Profitable
Unlike viruses, malware is extremely profitable.
Stealthily redirecting hundreds to sites, they can take advantage of increased advertising rates for the ads on those sites because of increased, albeit unwarranted, traffic.
- Botnets like Emotet uses hidden padding and “invisible” white text to fool users and security programs. If you follow instructions and enable editing, you defeat Microsoft's protection against malicious macros.
- Botnets like TrickBot and Nitol are big business. They can hack banks or create grass roots political movements.
- Calling scammers by their real names is a YouTube video showing a sneaky attack on Jim Browning's computer while he tracks them down.
- Not all security products detect all malware.
- The Microsoft Security Intelligence Report July—December 2014 (PDF) provides an insight into how malware and other exploits are developed and used to compromise computer security.
- Fixing the #1 problem in computer security: A data-driven defense discusses appropriately aligning computer security defenses with the threats that pose the greatest risk to a company's environment.
Popup Warnings that Won't Go Away
One form of malware are popups that warn that your computer is infected but have nothing to do with any security software. These may include ominous audio warnings and are often difficult to dismiss.
These popup “warnings” are launched by visiting corrupted websites. Your browser is merely processing a malicious script launched by an infected website.
Stop and Think
Don't panic. These are scams designed to get you to act without thinking.
Stop and think — you'll avoid falling victim to the scam.
After all, you do have decent security software installed, don't you?
Don't Call That Number
Never call phone numbers displayed in warnings or error messages.
Calling that number will not resolve any security issues. However, it will result in an expensive service contract that will not provide any protection.
Don't Provide Remote Access to Your Computer
If you let someone at the other end of that phone call have access to your computer its security will be compromised. The only way to ensure future protection will be to do a clean install of your operating system and programs.
CTRL-ALT-DEL
To get rid of the error message
- hit the Ctrl-Alt-Del keys simultaneously;
- select Task Manager from the list that appears;
- close the offending process.
This may be more difficult if you don't recognize normal processes, but closing all your browser's processes usually resolves the issue.
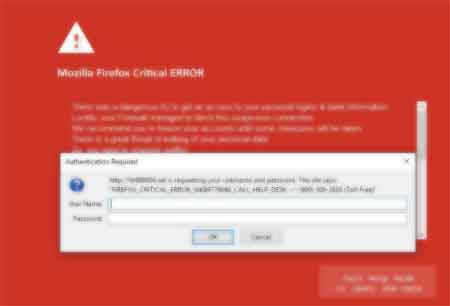
Firefox “Critical Error”
One example is the Firefox Critical Error where Firefox is locked with a fake login screen over a red background.
This malware is either installed by malware on your system or by visiting an infected site. The annoying audio warnings are designed to panic you into acting without thinking.
The following warning (or something similar) appears in the background:
There was a dangerous try to get an access to your personal logins & bank information. Luckily your Firewall managed to block this suspicious connection.
We recommend you to freeze your accounts until some measures will be taken.
There is a great threat of leaking of your personal data.
So, you need to respond swiftly!
Newer versions will have better grammar and can be harder to spot because foreign scammers are using ChatGPT and other AI programs to generate warnings.
This is a Scam
DON'T call the “support” number or fill in the login information.
- Calling the phone number displayed will cost you for unneeded services and/or have your system infected with additional malware.
- The login screen (authorization request) is an attempt to gather your username and password to be used to hack your accounts.
How to Fix the Problem
To close the “error” Windows users should
- press the Ctrl-Alt-Del keys simultaneously (but only once);
- select (highlight) Start Task Manager from the menu that appears;
- select (highlight) Firefox from the list of programs;
- select (highlight) End Task.
This should close Firefox (and with it the popup warning).
Cleanup Your Computer
Now you'll want to remove any recently installed programs that you've added and to do a full scan of your system with a reliable security program.
Consider obtaining professional help with cleaning up your computer. There may be more than one malware program installed on your computer.
Avoid dangerous download sites. Download from a legitimate developer's site where possible.
Other Scams
The Firefox fake login screen is only one of many variations.
Corrupted Windows Licence Key Scam
One scam reports that your Windows licence key has been corrupted and offers a toll-free number to call.
Fake “Support” Phone Number
Don't call the number.
Microsoft NEVER provides a phone number in legitimate error messages. Neither do other legitimate companies.
This is fake “warning” is a scam run by thieves.
They'll take your money then ask for remote access to your computer so they can “fix” the issue.
This is only an excuse to gain access to your computer and its information. You're more likely to have malware installed than end up with a cleaner computer.
I would never trust a computer where remote access was provided to unknown (and untrustworthy) providers of fake “support” services like this.
My recommendation is that you backup your data then do a clean install of your computer's operating system and programs after wiping the hard drive(s).
Ignore the Audio Warnings
Perhaps the most disturbing is the audio-based warning that your computer has been infected because it doesn't seem to have any solution other than to follow the instructions.
Again, DON'T call.
- Press the Ctrl-Alt-Del keys simultaneously (but only once);
- select (highlight) Start Task Manager from the menu that appears;
- select (highlight) Applications tab;
- select (highlight) the offending program from the list of programs;
- select (highlight) End Task.
If this fails, restart your computer (using the power button, if necessary).
Command Line Trickery
This form of malware tricks users into installing malicious content.
A new campaign employing ClickFix attacks has been spotted targeting both Windows and Linux systems using instructions that make infections on either operating system possible.ClickFix is a social engineering tactic where fake verification systems or application errors are used to trick website visitors into running console commands that install malware.
As a general policy, users should not copy and paste any commands into Run dialogs without knowing exactly what the command does. Doing so only increases the risk of a malware infection and theft of sensitive data.
— BleepingComputer
Malware Removal
Security suites are strongly recommended because only such suites can deal with the multifaceted threats facing computer users today. Such suites should contain software for removing malware and spyware from your system and to protect you from future infections.
Ransomware
Ransomware is special form of malware which encrypts the files on your computer and holds it for ransom. Beginning with CryptoLocker and evolving from there, this class of malware cannot be recovered except by paying the ransom and hoping the thieves don't simply walk away with your money.
You can only hope to prevent ransomware infections. Recovery is seldom possible except by wiping the computer and restoring your data from (hopefully) recent backups.
Recommended Security Software
See my recommended security solutions for help in selecting effective antivirus software.
Windows Defender
For a long time Microsoft's Windows Defender provided decent (but not excellent) anti-malware protection (much better than its anti-virus protection) and most security products could work along side it.
However, the quality of protection has improved tremendously and Windows Defender has earned excellent scores in some recent reviews.
After years of lagging behind competitors, Microsoft Windows Defender has earned a coveted AV-Test "Top Product" award. The free, built-in antivirus software in Windows 10 performs just as well as — or even better than — many of its paid competitors. Your Windows PC can now repel the vast majority of malware threats right out of the box.
— Tom's Hardware
These reviews are for Windows Defender running on a fully-updated Windows 10 or 11 system.
Other Safe Solutions
However, running more than one alternative anti-malware product at a time may cause a conflict (they can fight each other rather than the malware).
I recommend the following stand-alone products and services to deal with a malware infection:
- Malwarebytes Anti-Malware detects and removes worms, Trojans, rootkits, rogues, spyware, and other dangerous malware from your home PC.
- Malwarebytes Anti-Malware for Mac.
- Spybot Free Edition, available for private use, requires installation. Spybot — Search & Destroy 1.6.2 is recommended for recovery.
The best prevention requires a security suite with built-in anti-malware protection.
Beware of Fake Malware-removers
There is a disturbing trend of placing ads on websites that appear to “find” malware on your system. They offer to remove the infections if you purchase their product.
Don't fall for these tactics.
- These are rip-offs or fakes.
- Most include an unlikely number of “infected” files.
- Many include malicious ads for additional software.
- This software is more likely to create problems than to resolve them.
If you buy the subscription, you're likely to get a call trying to up-sell you on other products (you've demonstrated that you're not tech savvy).
How to Verify Links
You should always check to see where a link is going to send you if you click on it. Fake links abound.
- Hovering over (NOT clicking) any link in a browser should show the destination address.
- Be wary of links that take you off-site or to mysterious domains.
- You can search WHOIS records to determine who owns the site. Be wary of recent or short-term domains.
- How to avoid fake download buttons.
See How to Tell Fake Links to learn more about how website links work.
Obtaining More Information About Malware Removal
Unfortunately, many of the resources formerly linked from this page are no longer maintained.
- BleepingComputer virus, spyware & malware removal guides.
- Microsoft's tips to protecting your computer from malware.
What is Spyware?
Spyware is ANY SOFTWARE which employs a user's Internet connection in the background (the so-called “backchannel”) without their knowledge or explicit permission.
— Steve Gibson
The term “spyware” has been mostly replaced with the term “malware” and includes any program that has harmful or malevolent intent or purpose, even if it is disguised within an apparently useful program.
Your Personal Information For Sale
Internet companies, whose apparent “business model” is the exploitation of consumer trust and ignorance, are sneaking their spyware systems into our machines for their own purposes.
—Steve Gibson
See Your Privacy At Risk for more.
Big Names Don't Necessarily Guarantee Safety
The extent of this secret information collection may shock you. It is an explicit attack on personal privacy for commercial gain.
Free email services like Gmail began the trend, followed by cell phone services. Unfortunately, privacy has all but disappeared as corporations seek to know anything and everything about all of us.
Uncle Sam Gets Involved
Edward Snowden revealed a huge spying network organized by the NSA and other U.S. government agencies (as well as their counterparts virtually everywhere on the planet). It involves the largest ISPs and software companies. George Orwell must be rolling in his grave.
Company policies can and often do change. In many cases, short-term profits have proven to be more appealing than long-term customer loyalty in these companies.
One example is the Tim Hortons app scandal where the app was tracking you even after you left Tim Hortons, data that was probably worth millions to Tim Hortons.
The penalty for blatantly abusing their users privacy? A free coffee and donut.
Microsoft's New Revenue Model
Starting with Windows 10, Microsoft seeks to know more about us than previous Windows versions (the sort of private information they accused Google of harvesting).
Windows 10 collects personal information and displays ads within your system based upon that information while claiming Windows 10 is the most secure Windows ever.
Unfortunately, Windows 11 is no better, experimenting with ads when you search for files on your computer or while using File Explorer.
Spyware Tactics
Microsoft also used spyware-like tactics in forcing Windows 7 and 8 users to upgrade to Windows 10:
- Windows Update was used to install the GWX nagware which downloaded the files to the user's computer without permission.
- When it self-activated the Windows 10 upgrade, the program “interpreting” the user's closing of the offer with the red X to mean permission to install (the opposite of what it has meant on computers, including Windows systems, since the very beginning).
- To stop the upgrade you had to click next then decline the licence agreement — hardly an intuitive process.
- Many users found themselves unexpectedly restarting their computers running Windows 10. In the case of one client, the update failed TWICE, requiring a clean install of Windows 7 because the computer could not recover from the uninvited upgrade.
- Microsoft also installed ads promoting Windows 10 as part of “security fixes” for Internet Explorer.
Many consultants recommended disabling Windows Update because Microsoft was deceptive in what was actually being installed (“updates to Windows”).
I refused to upgrade to Windows 10 until most of the early privacy issues had been resolved.
Unfortunately, Microsoft made the requirements for Windows 11 so high that few computers more than a couple of years old could meet them. Supposedly, this was for security reasons, but other than the TPM and processor requirements, Windows 11 could run on much older equipment.
Learn More About Spyware
- GRC Discussion Group for Spyware is a forum for discussion about spyware.
- The Ethics of Anonymous Surveillance for Profit displays one example of such information gathering.
Keyloggers
Spyware isn't the only method of stealing information. There is also keyloggers.
- Keyloggers come in software and hardware varieties.
- Each has its advantages, depending upon the circumstances.
Hardware Keyloggers
The hardware keylogger is a small device that is plugged in-line with your keyboard in order to record your keystrokes.
Work Computers
Keyloggers may be installed by your employer. Courts have recognized the right of an employer to monitor the use of a company-owned computer.
Hardware Keyloggers
Since hardware keyloggers aren't software their operation is not detectable using software.
Different than Keyboard Adapters
Don't mistake a older keyboard adapter for a keylogger.
Such an adapter would have a different connector on each end.
Keyboard adapters were used to connect an older keyboard to a new computer or a newer keyboard to an older computer. These are rare today.
Public Access Computers
You need to be very careful about using public-access computers (like the ones at Kinko's or Internet cafés).
A New York man collected over 450 bank account passwords in Kinko's stores using a software keylogger.
Assume Zero Privacy
Assume that your computer activities are being monitored, and avoid providing user names and passwords or credit card information on these connections.
Clear the Cache
You might wish to ensure that you can clear the cache before you use these to enter user names and passwords.
Don't Enter Sensitive Information
You cannot ensure there is no keylogger device or access to the data you enter, so you may wish to reconsider the need to access banking or other sensitive information.
Use Virtual Keyboards
Some systems offer a virtual keyboard that uses the mouse to select input.
Look for the little virtual keyboards beside the user name and password entry like the one on the right of this LastPass example:
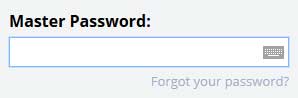
You can also see a live example on the login page for Islandnet.com.
Stalkerware
Stalkerware (or spouseware) is a sleazy market that caters to abusive and controlling people that are usually close to us.
Stalkerware, a type of commercially-available surveillance software, is installed on phones without device owners' knowledge or consent to secretly spy on them.The apps track victims' locations and allow abusers to read their text messages, monitor phone calls, see photos, videos, and web browsing, and much more.
— EFF
These companies pretend that it is sold as a method of protecting your child or monitoring employees' use of a company-issued cellphone.
Child Monitoring
If you think you're protecting your child, think again.
Your child's data collected is stored on servers that have probably already been hacked.
Do you want your child's photos and location data stored on potentially insecure servers controlled by a company with questionable ethics?
[B]y using this software on their kids, the parents aren't the only ones getting access to their data. The companies providing the service do as well.
— Vice
Employee Monitoring
Companies can legally monitoring employee use of a company-issued computer or cellphone.
However, consider what would happen if a server containing you company's sensitive data were hacked.
Illegal Monitoring
Stalkerware is mostly used illegally.
Not only is it a massive invasion of privacy, but stalking is illegal, whether electronic or otherwise.
Targeted individuals may bring a cause of action (lawsuit) against an operator on legal grounds of: invasion of privacy, public disclosure of private facts, breach of confidence, and intentional infliction of mental suffering.
— The Citizen Lab
- Eva Galperin: What you need to know about stalkerware TED Talk.
- When spies come home a Motherboard series about powerful surveillance software ordinary people use to spy on their loved ones.
- How to protect yourself from creepy, phone snooping spyware.
- EFF, antivirus companies, and human rights groups launch coalition to combat stalkerware.
Related Resources
On this site:
- Resources index
- Security basics
- Security strategies
- Security software
- Ransomware
- Identity theft
- Malicious attachments
- Phone fraud
- Phishing & email scams
Return to top
RussHarvey.bc.ca/resources/malware.html
Updated: May 22, 2025