Security Software
Antivirus, malware & firewall protection
Recommended Software | Evaluating Solutions | Fixing Issues
Update Your Software | Current Alerts | Hoaxes
All trademarks, company names or logos are the property of their respective owners.

We call it antivirus, but in truth it's unlikely you'll get hit with an actual computer virus. Malware these days is about making money, and there's no easy way to cash in on spreading a virus.Ransomware and data-stealing Trojans are much more common, as are bots that let the bot-herder rent out your computer for nefarious purposes. Modern antivirus utilities handle Trojans, rootkits, spyware, adware, ransomware, and more.
— PCMag
Security products, by their very nature, require deep penetration into your operating system and frequently “call home” for security updates. That is a reason to be careful in your selection of security software.
You Need a Security Suite
The term “anti-virus” now generally refers to a security suite, but you should check to be sure.
To remain protected, your computers as well as mobile and IoT devices must be protected by a security suite of products that must include antivirus, antimalware, anti-phishing, anti-ransomware protection plus an effective advanced two-way firewall.
That protection is ineffective unless you're running an up-to-date version that is currently maintained. Security products are almost always playing catch-up.
Cyber attackers are constantly tweaking new attack techniques, honing existing ones or combining them into an attack wave.
— AV-TEST
- Multi-faceted and simultaneous blended threats can overwhelm any protection unless the software is designed to deal with all of them simultaneously.
- Because threats develop and change so rapidly, current security software relies more upon recognizing malicious patterns of infections than databases of past attacks.
- State-sponsored hacking is a form of cyber warfare that is a serious threat due to massive budgets and extremely sophisticated equipment.
- Some infections are difficult to repair, particularly ransomware which encrypts your data and extorts money via untraceable bitcoins.
- Malware (sometimes called spyware) can go unnoticed yet risks your privacy by stealing information and slows down your computer. Protection is specialized software with access to a current database of malware and removal instructions.
- Keyloggers capture key strokes including passwords and other private information. There are both hardware and software keyloggers.
If your security software fails and your data is compromised, it can have serious consequences for your reputation, especially for businesses and high-profile individuals.
Free Security Software Options
There is no excuse for not running security software. Most vendors offer FREE versions of their security software.
However, keep in mind that not all security software is as effective. Be certain you're getting enough protection before making a decision.
Is it reasonable to save money by eschewing third-party security protection and just relying on what's built into the OS? Well, probably not.In most cases, you'll be safer springing for third-party security or using a top-tier free solution. Depending on what operating system is involved, going beyond the basics is always a good idea, and sometimes a necessity.
— PCMag
Avast Sold Personal Data
Avast collected personal data then sold that data while misleading consumers about its privacy practices. This should concern everyone using “free” products.
The complaint says Avast violated millions of consumers' rights by collecting, storing, and selling their browsing data without their knowledge and consent while misleading them that the products used to harvest their data would block online tracking."Avast promised users that its products would protect the privacy of their browsing data but delivered the opposite. Avast's bait-and-switch surveillance tactics compromised consumers' privacy and broke the law," said Samuel Levine, the head of the FTC's Bureau of Consumer Protection.
— BleepingComputer
Features to Look For
In addition to ensuring that the various required components of the security suite are covered, you need to look for these features to remain properly protected.
Real-time Protection
Some security products don't have real-time protection and are more suited to fixing an infected system than preventing infections in the first place.
Your security software must include real-time protection that detects threats to your computer and software without having to run a scan. This includes ensuring that the programs in memory are monitored for exploits and malicious activities.
Web Filtering
Web filtering watches your web browser to warn you about hacked website or downloads that redirect you to malicious sites or files. Web content should be scanned before it is accessed or downloaded. Real-time protection does this automatically.
It should also include the ability to block malicious, hacked or inappropriate websites (porn, gambling, drugs, etc.) — often referred to as parental controls. Abandoned websites are often picked up by malicious actors looking to take advantage of existing links to those sites.
VPN Recommended
While many of us once used our computers at home or work accessing the Internet through networks we control, that is not true for today's mobile world. We now regularly use public WiFi in coffeeshops, malls, businesses and many other locations.
Public WiFi and borrowed Internet access points are vulnerable because unencrypted wireless traffic can be intercepted by other users.
A VPNs secures your wireless traffic by encrypting it before it is broadcast to the Internet. The need for a VPN depends upon what you use it for. Three legitimate reasons to use a VPN are:
- to combat censorship;
- location spoofing; and
- to encrypt data.
While most browsers now encrypt data securely (providing you and the websites you visit are both using HTTPS), there can be circumstances where you'd like to increase that security by using a VPN to protect your traffic when using public WiFi.
Computer Scans
While realtime scanning is designed to protect you while surfing the Web and using other software, some downloads don't show their true nature while being retrieved from the remote site.
The real-time scanner should catch these files when they are opened, but a full-computer scan (or a scan of a particular file or folder) will test the files to see if they are malicious.
Threat emulation can evaluate unknown files in the cloud to see if they exhibit abnormal behaviour. Because this is done remotely, your computer is not placed at risk.
Keep ALL Your Software Current
Ensure your security software is always current.
New threats can overwhelm your security software, especially if you don't update it regularly or fail to upgrade it to a new version when your installed version is no longer supported.
That means using a currently-supported version with all its available updates. Checking frequently for updates to your security software is critical to remaining secure and should be done a minimum of once per day.
In addition, you must ensure that your operating system and the programs on your system are all current for your computer to be protected from zero-day and other newly-discovered vulnerabilities.
- Install recommended updates and service packs for both your operating system and installed software programs or apps.
- Upgrade or uninstall obsolete software.
To check the software version:
- Windows: Help ⇒ About
- Mac: program name ⇒ About
Business Users
Just as you install alarm systems and good quality locks to protect your physical business premises, you need to protect your virtual premises by investing in excellent security software.
For too long computer security has been ignored by businesses, particularly when it comes to protecting customer data they gleaned off the Internet.
Consider Managed Services
If your business falls into the category of 38% of small businesses that don't regularly update their security software solutions, or is a SMB worried about the growing rise in cyber-attacks, then there are basically two avenues to explore: managed antivirus and non-managed antivirus solutions.Managed antivirus, sometimes referred to as centrally managed antivirus, is a software option that is designed to protect your business systems from viruses and other threats. It is referred to as central because the protection it offers comes from a single source, i.e. a network server.
So, instead of each individual device having separate antivirus software installed, everything flows through a single network server. Centrally managed antivirus is likely to be administered by an I.T. partner, an organization hired to implement and oversee the protection of your business. In that sense, you are outsourcing the security of your business systems to third party security providers.
Can that be cost-effective? That will depend on the size of your organization and the way it functions.
— ZoneAlarm Blog
Consider Your Investment
When viewing the cost of security software, consider what you've invested into the hardware and software (never mind your time and data).
Businesses that fall victim to ransomware or a security breach can suffer irreparable damage to their reputation. You will certainly lose productivity and an estimated 60% of small businesses will never recover.
Recovery Can Be Expensive
At the very minimum, you'll be without your computer while it is in the shop. What damage could that downtime do to your personal or business commitments?
Restoring your computer's operating system and software can be expensive but the recovery of lost data may not be possible at all if your backups fail or are not current enough.
By purchasing decent security software and training your staff in security basics you may avoid these costs.
Backups Ensure Data Recovery
Keep a current backup of everything important to you. These backups are your only method of recovery if an undetected threat cannot be treated.
In the worst case scenario, you could purchase a new computer and replace all your software, but your data is irreplaceable. A secure and current backup could be priceless.
For your most important data and frequently-modified data, frequent backups to a thumb drive or similar device could be critical. However, do not leave the device plugged into the computer since that exposes it to the same vulnerabilities as the computer.
Ransomware Recovery
Most current security suites provide some protection against ransomware but failure could be catastrophic to your business. Not only is paying to recover data costly, but there is no guarantee that you will get your data back. Ransomware-as-a-service allows amateurs to engage in this practice without knowing (or caring) about actual recovery methods.
You can view the efforts and documentation around CryptoLocker ransomware in 2013. Ransomware has evolved significantly since then, but it will demonstrate some of the challenges in dealing with such an infection, including the uncertainty.
Automatic Backups
Be sure to evaluate the cost of automatic backups to always-connected devices or services:
- Backups to devices continually connected to your computer are just as vulnerable to ransomware as the computer itself.
- Ransomware also targets cloud storage because that is where the data has gone.
It may be inconvenient to have to remember to connect a removable drive or to log into your online cloud storage service when you schedule your backups, but that would keep malicious actors from accessing your backups when they attack your computers. With automatic overnight backups you can accomplish this by scheduling the shutdown of your computers and the backup service following the backup process.
No Guarantees with Ransomware
Several companies provide tools that can help recover files if you send them a copy of an encrypted file with the unencrypted original to help determine the correct recovery tool but there is no guarantee. Ransomware is a rapidly evolving risk.
Check Point ZoneAlarm Anti-Ransomware remains one of the most effective ransomware-specific security tools we've tested. It detected all our real-world ransomware samples, though its recovery system missed some files.
— PCMag
Paying the Ransom Encourages Future Attacks
If you choose to pay the ransom, you're only making future attacks more likely. You can't be certain that your system is safe afterwards even if you obtain a working recovery key. Remember, you're dealing with crooks, not a reputable business.
If, as appears true, some security companies negotiate with the ransomers, that creates a symbiotic relationship involving the company you're paying to protect your data and those threatening you.
No Operating System or Device is Safe
While Windows has carried the reputation for being more vulnerable, you should consider ensuring that you can recover from an attack.
Depending on your operating system, adding antivirus protection beyond what's built in ranges from a good idea to an absolute necessity.
— PCMag
What About the Mac?
The Mac has an undeserved reputation for being “safe” from viruses and malware.
Still think Macs can't get viruses? That outdated thinking puts you and your data at risk.The platform with the higher number of virus encounters? Mac users. That's right, the same group in which only 34% claim to install antivirus software.
It's seriously time to rethink that position.
— PCMag
You need to be running decent security (antivirus) software on your Mac.
- The best MacOS antivirus software for home users.
- The best MacOS antivirus software for business users.
What About Linux?
Like Macs, many Linux users are under the impression that they don't need antivirus protection. Again, it is time to change that opinion.
Mallox, previously a Windows-only malware, is putting Linux and VMWare ESXi systems into its crosshairs, marking a significant evolution for the operation.
— BleepingComputer
Linux is considered to be more secure than other operating systems. However, it's increasingly a target of attackers, as Linux systems are used for critical roles like, web servers and internal file servers.In addition to being susceptible to Linux-based and cross-platform exploits, unprotected Linux machines can also become distribution points for Windows, Mac, and Android malware.
— Sophos
You need to be running security (antivirus) software on your Linux computer.
AV-TEST.org doesn't yet test Linux security software (Linux has a much higher profile in server software) but that is bound to come in the future as the home use of Linux increases.
You Need to Be Vigilant
Many threats, including ransomware, evolve rapidly and employ zero-day vulnerabilities, weaknesses in software that are immediately exploitable (even before they are discovered).
A new campaign employing ClickFix attacks has been spotted targeting both Windows and Linux systems using instructions that make infections on either operating system possible.ClickFix is a social engineering tactic where fake verification systems or application errors are used to trick website visitors into running console commands that install malware.
As a general policy, users should not copy and paste any commands into Run dialogs without knowing exactly what the command does. Doing so only increases the risk of a malware infection and theft of sensitive data.
— BleepingComputer
Security software that uses virus signatures can only protect you against known threats. Newer or evolving threats are harder to detect so most security software looks for unusual or malicious activity (threat emulation) to prevent unknown threats from infecting your computer.
Prepare for Disaster
Be prepared for disaster before it happens.
Backup your data regularly so you'll still have a copy of your data if you're infected with ransomware or anything else your security software fails to protect you from. Anything not backed up could be unrecoverable. Schedule backups accordingly.
Copying current documents to a USB thumb drive or portable drive between backups can mean the difference between losing a week's data or recovering everything.
Hidden File Extensions
You should unhide “known” file types because they are known to Windows, but don't warn you about potential security risks.
Windows hides these “known” file extensions by default. Many users don't know which files types are potentially dangerous. For example, many assumed .SCR files were screen saver files. While they can be used for that purpose, they are scripting files which can be extremely dangerous to open.
Malicious file types include .JS, .EXE, .SCR, .COM and .BAT. These are unsafe to open, especially when received as an email attachment.
Disable Macros in MS Word
Spammers often use macros in an attached Word document to infect your computer. Disable macros in MS Word: (Options ⇒ Trust Center ⇒ Trust Center Settings & Macro Settings). Choose “Disable all macros with notification.”
Even with macros disabled, many zero-day vulnerabilities can be exploited in MS Office files.
Watch for Unusual Activity
Be vigilant about what you download. Only install software from verified sources.
If you notice unusual file activity, disconnect your network connection (disable WiFi and unplug the network cable).
While you may not protect your own data, disconnecting from the Internet can protect other computers and devices on your network, particularly if you share files between them.
Avoid Risky Behaviour
Pause before clicking: Stop. Think. Connect.
People tend to value convenience over caution. Pause to allow the time to consider the potential cost of your actions. Common sense goes a long way. Files don't install themselves; you have to initiate some action. Think before you perform an action you may regret.
Be Wary When Opening Email
Malware generally spreads though malicious email attachments (including images, documents and ZIP files) leaving you susceptible to data loss and identity theft. This problem is illustrated in Trustwave's Tale of the two payloads.
It has become very common to receive phishing emails that contain fake notices of unexpected invoices and similar tactics designed to get you to open malicious attachments or visit fake sites designed to look like the real site.
Don't trust either the attachments, the links or the contact information. No legitimate organization should be using Gmail to send business emails (watch for knock-off domains as well).
Links Can Be Faked
Fake links can be used in emails, websites or text messages to misdirect. Often the number listed in such phishing attempts will connect you with a scam call centre.
Be wary of websites hosted on recent/short-term domains and of shortened links like those used on X (formerly Twitter). Both can be used for malicious purposes.
CBC Marketplace brought together top scambusters to fight scams. You can watch how scammers use fake emails, texts and phone numbers to scam you out of your money.
Oversharing on social media?
Information posted online, particularly in social media, can be used to personalize the attempts to scam you. It can also be used to hack your passwords by learning answers to common password recovery questions.
Recommended Software
Paid Security Software
I recommend the following paid security software products:
Free security software provides options for those that truly cannot afford protection, but most free products provide less security and potentially collect and sell personal data to fund those products.
ZoneAlarm Extreme Security NextGen
ZoneAlarm Extreme Security NextGen is recommended for folks that want a good security suite that works without much hands-on maintenance:
- It is a complete security & privacy suite that includes anti-ransomware.
- It guards you against the most sophisticated cyber threats and attacks.
- It is less complex to run than the legacy product and has a modern interface.
- It is supported on Windows 7/10/11, Android, iOS.
Most of my clients and I used the legacy ZoneAlarm Extreme Security (declared a legacy product on August 26, 2022) for more than 10 years without incident. Many clients continue to run ZoneAlarm Extreme Security NextGen without any reported incidents.
ZoneAlarm also sells a stand-alone Anti-ransomware service (additional protection for your primary security software).
Check Point ZoneAlarm Anti-Ransomware is the most effective ransomware-specific security tool we've seen. In testing, it showed complete success against all of our real-world samples.
— PC Magazine
Kaspersky
Kaspersky Premium provides excellent real-time protection, proactive detection and instantly isolates and removes dangerous attempts to download malicious scripts on websites you visit.
- Kaspersky Premium includes a free VPN and premium versions of Kaspersky's password manager and protection for kids.
- Supported on Windows, macOS, Android &iOS. Details….
I originally purchased Kaspersky Total Security (now Kaspersky Premium) to protect my Mac computer because ZoneAlarm Extreme did not work on Macs. When I ran into problems using the new NextGen product, I switched over my Windows computers from ZoneAlarm to Kaspersky.
Kaspersky has been consistently one of the best anti-virus products in tests for years.
Because Kaspersky is a multinational corporation operating in 200 countries and territories I feel it is safe enough to use, especially given the increased vigilance it will receive as a result.
For more than seven years, Kaspersky has been taking flak from intelligence agencies in the US and elsewhere. The kerfuffle only escalated with the start of the war between Russia and Ukraine. Yet at the same time, Kaspersky's researchers have played a major part in defense against the newest malware attacks.
— Kaspersky
If you feel uncomfortable with the U.S. ban, move to ZoneAlarm or another product.
Mac and Linux Solutions
Mac and Linux have traditionally been safer than Windows for security, but this is no longer true.
- Mac users, see Security Software on my Mac resources page.
- Linux users, see Security Software on my Linux resources page.
Free Antivirus Solutions
ZoneAlarm Free Antivirus + Firewall
- Free Antivirus + Firewall is reliable and powerful.
- Supported on Windows 7/10/11 (Windows 11 supported with version 3.3.410 and later).
- Full details….
ZoneAlarm Extreme NextGen provides better protection, adding web secure and anti-ransomware.
Microsoft Defender
This Microsoft security product has been called Microsoft Defender, Windows Security Center and Windows Defender in its various incarnations.
Once considered poor protection, it now has much better reports. Effective protection requires a fully-updated Windows 10 or 11 system.
Defender's biggest plus is its minimal impact on system resources. It also offers a Offline Scan which can scan for and delete persistent malware before it has a chance to load.
However, Defender doesn't yet warrant eliminating other protection.
Windows Defender's own developers seem to consider it a Plan B, rather than a main solution. If you install a third-party antivirus, Windows Defender goes dormant, so as not to interfere. If you remove third-party protection, it revives and takes up the job of defense again. The best antivirus programs, even free antivirus tools, perform significantly better in testing and offer more features.
— PCMag
While acknowledging that Windows Defender has improved greatly over the last few years and that Windows 11 improves security, PCMag security expert Neil Rubenking states that you still need third-party antivirus software. The redubbed Microsoft Defender Antivirus gets mixed results from independent malware testing labs and falls short of the competition in phishing protection.
— PCMag
And now an incident that should pour cold water on plans to save money by depending on Windows Defender (the free version of Malwarebytes was installed but that doesn't provide realtime protection).
Microsoft Defender, the antivirus app that comes enabled in Windows Vista and later, reportedly failed to catch a type of malware that hijacked a victim's Google account in the Chrome browser and stole over $24,000 in cryptocurrency.“He got access to my Google passwords because my Bitwarden was unlocked and then deducted the wallet extension's passwords.”
— PCMag
Windows Defender shuts down when another security software is running and this has been weaponized:
A new tool called 'Defendnot' can disable Microsoft Defender on Windows devices by registering a fake antivirus product, even when no real AV is installed.The trick utilizes an undocumented Windows Security Center (WSC) API that antivirus software uses to tell Windows it is installed and is now managing the real-time protection for the device.
When an antivirus program is registered, Windows automatically disables Microsoft Defender to avoid conflicts from running multiple security applications on the same device.
— Bleeping Computer May 2025
What About Other Antivirus Solutions?
Other products may be excellent security software solutions but I have not personally tested them, at least not recently.
Some require significant system resources (mainly RAM) and most have a firewall inferior to ZoneAlarm Extreme NextGen.
More about evaluating solutions.
Malwarebytes
Malwarebytes can be downloaded and installed for free. However, without a premium subscription, it doesn't automatically scan your system and recent tests by AV-Test were less than stellar.
It is a good interim solution for checking an infected computer. Long-term security requires a subscription.
ISP-Provided Packages
Many ISPs include security software protection either as a part of their regular services (some charge a fee). Most are intensive memory hogs and not as effective as commercial products.
Even though many ISPs automatically check email for spam and viruses you still need a security suite installed to protect your computer and data.
Evaluating Security Software Solutions
While you can purchase security packages in retail stores, online sites offer software at reduced rates, provide 24/7 access to instant updates and technical support. Purchase directly from the vendor — never via third parties with unknown agendas and privacy practices.
Save a copy of the installation file and the licence key (preferably on removable media in case you suffer a catastrophic loss of your operating system) so you can repair or reinstall your security software in the future.
Not All Products Equal
Assessing and comparing security products is difficult. Security software deals with the ever-changing world of online threats.
Reviews are essentially taking a snapshot of a series of products at a single point in time. Highly rated products that have just completed an update could be rated less positively in a week or a month.
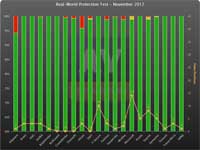
AV-Comparatives.org tests show significant variations in the ability of different security products to prevent infections:
Results vary by month as vendors update their products and fix issues.
- green were automatically blocked;
- yellow were user dependent; and
- red were compromised.
I strongly recommend checking the reviews of products suitable for your operating system before finalizing your choice of products. AV-Test includes recommendations for home & business users for Windows, MacOS, Android and Internet of Things.
Often one product will excel in one area but be weak elsewhere so be sure to include your specific needs into the evaluation process. Both the strengths and weaknesses of specific products can change over time so be sure to view a current assessment.
Verify the system requirements (optimally the recommended rather than minimum requirements) to ensure your computer can run the software without slowing things down.
- AMTSO security features check tools test the correct installation, configuration and operation of specific security products.
No matter how good your security product is, the developers face state-sponsored hackers that are continually looking for weaknesses and are usually better funded.
Don't trust blanket statements that say that the code is “military-grade” or “NSA-proof” these mean nothing and give a strong warning that the creators are overconfident or unwilling to consider the possible failings in their product.
— EFF
Avoid creating your own “suite.” Running multiple security programs can conflict with each other and prevents detection rather than improving it. One security program can appear to be attacking the system when viewed by competing security software.
Paid or Free?
In addition to various levels of protection, many companies offer two classes of products:
- paid versions for which you need to purchase a licence; and
- free versions which are available at no charge (provided you can meet the licence requirements).
I strongly recommend sticking with a paid subscription because it will offer more frequent updates, better security and requests for help from paying customers will always get priority. Some free versions may not perform as well as you expect.
In its recent endurance test, which was carried out over a period of 6 months, AV-TEST tested 18 Internet security suites for their protection, performance and usability. The test shows: more than two-thirds of the protection packages can be recommended, but the best performance does cost some money. Paid software packages are also the most secure.
— AV-TEST
The cost of repairs to your computer if a free product fails will far exceed the cost of most security products. If you truly cannot afford to purchase your security suite, there are basic (and sometimes excellent) free protection for home users.
Purchased software generally offers better protection, especially when threats are evolving quickly.
- Free software provides protection for those that truly cannot afford to purchase protection.
- Free security software is usually not licensed for businesses.
- Free security software often updates only once a day.
Free addons like browser extensions can increase your vulnerability and threaten your privacy. Be certain you need the extra functions or features they provide.
Microsoft Security
Microsoft enables the Windows firewall by default and checks for the presence of a current antivirus solution, enabling Windows Defender if security software is not detected.
Base-line Protection
These capabilities provides for a base-line protection on a fully-updated currently-supported Windows system but is insufficient on its own.
Microsoft Defender Antivirus does a fine job of securing Windows 10 and 11 PCs that have no other protection, but it doesn't beat the best free or paid third-party tools.
— PCMag
Third-party security software is designed to work alongside Windows Defender. That is NOT true for any other third-party product.
Use a Security Suite
A security suite that includes all the security protection is recommended. Avoid shopping component-by-component to meet your needs.
- The best Windows antivirus software for home users.
- The best Windows antivirus software for business users.
- The best MacOS antivirus software for home users.
- The best MacOS antivirus software for business users.
- The best antivirus software for Android.
Consumer Protection
Companies that use misleading language or outright lie about the suitability of software need to be exposed.
Avast is harvesting users' browser histories on the pretext that the data has been 'de-identified,' thus protecting your privacy. But the data, which is being sold to third parties, can be linked back to people's real identities, exposing every click and search they've made.
— PCMag
Consumers don't have the ability to assess claims made by software vendors.
No consumer would realistically have an inkling that their antivirus software could be selling their browsing data and—even more sensitive information such as mouse movement — to an array of third parties.
— US Senator Mark Warner
Consumers, including small businesses, can check out the evaluations found on reliable websites and magazines to evaluate antivirus and other security products. I strongly recommend AV Comparatives for independent reviews of antivirus software.
- Latest tests shows current test results.
- Summary reports provides historical performance.
- Test results by platform includes tests for home users, business users & IoT.
- Repair tests for Windows shows how well Windows security products did in recovering from a virus attack.
False Positives
The number of false positives (safe files tagged as viruses) should be few or none. Most antivirus programs look for certain traits that are common to virus activity to detect unknown threats. Unfortunately, this can occasionally flag legitimate programs.
- False alarm tests shows the reliability of infection reports.
Files such as password hacking utilities for recovery specialists are legitimate but can be flagged by security software. This sort of software should not be on most people's computers.
Automatic Scans and Updates
Ensure that your security software will update automatically and provide for a scheduled scan to detect issues missed while running a realtime scanner (which checks files as they are opened).
Enterprise Protection
Enterprises should consider a Managed Security Services Provider (MSSP) because these larger businesses involve a different level of risk. Managed security provides security via the network rather than on individual machines.
Keep in mind that moving to a MSSP is not without risk.
The Kaseya ransomware attack on July 2, 2021 infected 800 to 1500 small to medium-sized companies. Kaseya and each infected business would have to pay independently (and paying the ransom only encourages future attacks).
Issues with Antivirus Software
No security software is ever a finished product. Conditions are continually changing and, without constant updates to both the product and its methods of detection, the software cannot do the job it was designed to do.
First, Check for Updates
At any one point in time, specific security products can be more or less effective than their competition.
Ensure that there are no updates available starting with new virus definitions (installed automatically) then seek newer software versions (requiring manual download and installation).
Scan Your System
Once everything is updated, do a complete scan of your system including archived (zip) files.
Multiple Security Products can Conflict
If updating your software doesn't resolve issues, you need to verify that there are no competing security products installed on your system.
McAfee Security Scan Plus (installed with other software as an optional download) shouldn't conflict but is also unnecessary so it adds risk. Don't install it; uninstall it if it is on your systems.
There is the potential for conflicts and problems when using multiple firewalls or security programs.
If you have more than one antivirus program running at the same time–or more than one firewall–you're asking for trouble. Two such programs, trying to do the same thing at the same time, will slow down your system. Worse, they can cause conflicts.
— PCWorld
Today's programs use “threat emulation” to detect new and unknown threats which looks like malicious activity to a second security program. Rather than improving security, multiple products leave your system vulnerable.
Microsoft's Windows Defender and Windows Firewall are generally either allowed or disabled by most security software. Because MS Defender is included as part of Windows, it is the only exception.
Acronis True Image
I stopped recommending Acronis True Image backup software when it added anti-ransomware and antimalware in 2021 because you couldn't disable that unproven protection.
This is problematic if you have other security software installed because Acronis True Image can conflict with your chosen and trusted security software. Unwanted software can slow or harm your computer.
Acronis True Image now allows you to install only the backup software by running a custom installation and unchecking the security options.
Use a Security Suite
I strongly recommend installing a decent security suite rather than independent antivirus, anti-spyware, anti-ransomware and firewall programs to avoid bloat and ensure compatibility.
Watch for add-on security features in other software (such as Acronis True Image) which can interfere with your security software's ability to protect you.
Can Security Software Slow Your System?
Security software has been known to have significant impact on your system performance. There are several reasons for this, including the necessary complexity of modern protection, but there can be other reasons including:
- startup and background processes
- unwanted programs
- malware
- older hardware
- insufficient RAM
Startup and Background Processes
Many programs are configured to run with Windows (or other operating systems) to make them appear to run quickly when you choose to launch them.
Unless you're running a particular program on a legacy system that is your primary system, most of these startups can be disabled.
Windows 10 and 11 provide a control of these (Start ⇒ Settings ⇒ Apps & Features ⇒ Startup) but I strongly recommend CCleaner for this purpose. Click on the Tools then select Startup. Disable startups rather than deleting them so you can recover if you make a wrong choice.
Unwanted Programs
Windows 10 and 11 install a lot of additional software by default but that isn't the only source.
- Manufacturers can add even more, including “customer participation” software (bloatware that tracks what you do with their software).
- During the download and installation of programs, watch for unwanted added software.
Uninstall any software you don't want or need (Start ⇒ Settings ⇒ Apps & Features).
Malware
One of the first signs of a malware infection is a slowing down of your system.
Malware, which includes viruses, adware, spyware and more, is seriously harmful to your computer. Aside from exposing your sensitive information to hackers, disrupting your computer operations, and causing frequent freezing and crashing, malware can seriously slow your computer down, making it almost impossible to make any use of it at all.
— ZoneAlarm Blog
If your security software isn't up to the task of protecting you, you'll have to find anti-malware software to remove the infection or seek professional help.
Legacy Hardware
If you're running a current operating system (Windows, Mac, Linux, etc.) on an older computer, the performance can be hampered. Developers for new hardware so they can provide new features and take advantage of modern technology. Your computer may be suffering as new updates are released even if it was responsive when newer.
The other aspect of hardware is the size of your hard drive. Solid state drivers are much faster but can be much smaller. Legacy driver are cheaper, but don't work well when they are nearly full.
Insufficient RAM
RAM (or “memory”) is where a lot of the processing of information on a computer happens. When you don't have enough RAM the computer offloads some of its load onto the hard drive which is much slower than RAM. This results in significant slowdowns.
RAM is one of the least expensive upgrades, although it will depend upon your hardware as to how much RAM it will support and whether it is used efficiently.
Onboard video (motherboard-based video) uses part of the system RAM. By purchasing a separate video card (not possible for laptops or some name-brand computers) you release this RAM, replacing it with the video RAM on the card (more is better).
Finding Help
While there are some generic similarities between security products (they provide the same function), you'll need to locate help specific to the program(s) you're running.
Start with Vendor's Site
First, seek help on your product's support website and their support forum. Search for your specific problem, using an error message or other specific search criteria.
Internet Searches
Generic searches on the Web can be helpful, but you'll need to ensure that the suggestions don't get you into more trouble or land you on a malicious site.
Maintain Your Software
All software requires maintenance.
Update Security Software
Regularly download and install security software definitions and program updates.
- New virus and spyware definitions usually update automatically.
- Even though your security software updates automatically, it is a good idea to regularly update manually.
Major updates provide new features while interim updates fix security gaps.
Install Program Updates
If you download an update from the Web, it has to be manually installed by clicking on the installer program you downloaded.
Update Your Operating System
Set your operating system to automatically check for updates. These include feature updates (which replaced the service packs in older versions of Windows). It is also a good idea to check for updates manually.
Updates Improve Security
Updates to your operating system do more than install new features. They remove zero-day vulnerabilities and improve security.
Service Packs
Service packs are significant updates to your operating system and provide a baseline for maintaining security. Windows 11 now has one feature update per year as well as periodic security updates.
Obsolete? Upgrade or Uninstall
Upgrade or uninstall any software that becomes unsupported.
- Don't run unsupported versions of any operating system.
- Upgrade your software when your vendor no longer offers security updates.
Base Engine Updates
Some security products don't update the base engine automatically. You may need to purchase the newest version to get current security but check to see if you can download an updated version from the vendor's site first.
Microsoft Programs Vulnerable
Built-in programs are tightly tied into Windows and vulnerable even if you're not using them.
- Microsoft Office vulnerabilities have been used to compromise email programs and inject threats into the system's web browser.
- Microsoft Edge cannot be uninstalled so it needs to be updated, even if you're not using it.
- Internet Explorer is obsolete and pending removal in Windows 10.
Hardware Issues
Some vulnerabilities are hardware-based.
Spectre and Meltdown
Meltdown and Spectre were discovered in early 2018 that affects virtually every computer and mobile device produced since 1995.
Hardware released after 2018 shouldn't be as vulnerable. New processors have been re-engineered to avoid a similar problem in the future.
Security Patches
The patches significantly affect system performance and AMD restart issues.
Current Alert Listings
New vulnerabilities are found all the time. This site is not capable of tracking them all, but provides some examples to help you learn what to watch for.
What You Can Do
Take precautions when opening unexpected email attachments.
- STOP and THINK before acting.
- Check email addresses.
- Be wary of attachments and links.
- Update affected software.
Threat Emulation software included with ZoneAlarm Extreme can analyze suspicious files for threats.
Referring to online backup servers as being “in the cloud” is misleading.
These are large clusters of computers and storage devices, running imperfect software, managed by imperfect staff and too easily accessible from anywhere in the world.
There's not much that average users can do, other than install updates for various online services whenever they're available.
— Wired
Checking For Alerts
You can find current alert listings on these sites:
- Kaspersky Secure List.
- McAfee Threat Center.
- Symantec Security Center.
- Canadian Centre for Cyber Security.
- ZoneAlarm blog.
- Live cyber threat map.
Threat Evaluation
Learning more about threats:
- ZoneAlarm cyber security glossary.
- How to check if a website is safe.
- Types of computer security threats.
- Cyberattacks & data breaches.
- Data breaches: Threats and consequences.
- Who's hacked? Latest data breaches and cyberattacks.
Error Messages
If your security software generates an error or detection message, you can use that to learn more about what was detected by searching the web using the identifiers.
Different vendors can describe the same infection differently.
Fake Error Messages
Beware of fake error messages.
Be Wary of Hoaxes
There are many forms of hoaxes and fake news, including social media, news reports, emails and websites. Learn to verify information.
Know Your Security Software
Get to know your security software so that you can use it effectively. Learn its limitations and know how it responds to threats.
- Don't respond to fake virus and spyware warnings.
- Don't get fooled by popup warnings that won't go away.
- Never call phone numbers displayed in warnings or error messages.
- Don't install multiple antivirus programs on one computer.
The best defense is to keep your protection current and to know how your security software works. Check your security software vendor's website for the FAQ or support section.
Popups telling you that you're infected or that security problems have been detected are seldom true except those generated by the security software you have installed.
Fake Virus & Spyware Warnings
Watch out for website “ads” that "report spyware on your system."
These ads are simulated (but realistic-looking) “infection reports.”
If you install their software, its search displays large numbers of “infections” to be removed only if you purchase their product. Scam!
Popup Messages
Fake pop-up messages are rip-offs or fakes. Most report an unrealistic number of infections. Don't be scammed.
Legitimate Microsoft error messages do not contain phone numbers.
Fix popup warnings that won't go away.
Telemarketing Scams
You many also receive calls from telemarketers telling you your computer is infected.
Simply hang up.
Related Resources
On this site:
- Resources index
- ZoneAlarm security products
- Kaspersky security products
- Security basics
- Security strategies
- Mobile security
- Malware & spyware
- Ransomware
- Firewalls: your first line of defense
Return to top
RussHarvey.bc.ca/resources/antivirus.html
Updated: June 14, 2025