Updating
Dealing with obsolescence
Update Your Device | Replace Obsolete Apps
Downloading | Software Security | Installation Hints
All trademarks, company names or logos are the property of their respective owners.

Downloading but not installing updates is like buying new batteries but not placing them in a flashlight.
[Y]ou'd think that the purchase of devices with firmware or software drivers would be up to date right out of the box. In reality, devices often arrive with out-of-date software and demand that you update immediately. But if you let that slip by, as many consumers do, the device is potentially insecure. Consumers are sometimes put off by the extra time that takes, not realizing how important it is.
— Susan Bradley
Update Your Device
There are several aspects to updating your device including running a currently-supported version of
- the operating system (OS);
- the software; and
- the drivers (software that talks to hardware).
Is Your Operating System Supported?
One of the most important security measures you can take is to ensure every device is running a currently-supported operating system whether it is Windows, macOS, Linux, Android or iOS.
When your device's operating system is no longer supported, either upgrade it, replace the device or take it offline permanently.
If you run an unsupported operating system you risk not only your data, but your privacy as the warning from Microsoft indicates:
An unsupported version of Windows will no longer receive software updates from Windows Update. These include security updates that can help protect your PC from harmful viruses, spyware, and other malicious software, which can steal your personal information.Windows Update also installs the latest software updates to improve the reliability of Windows — new drivers for your hardware and more.
— Microsoft
This is true for all the varieties of operating systems. An unsupported operating system is a major vulnerability.
Install Critical Updates to Your System
All operating system vendors provide security and other updates to their software. Updates include fixes to problems and support for newer hardware. It is recommended that you update when updates become available, especially critical security updates.
WannaCry hit organizations around the world hard in May 2017, infecting over 200,000 computers in three days. Yet a patch for the exploited EternalBlue vulnerability had been available for a month before the attack.Updates and patches need to be installed immediately and have an automatic setting.
— Check Point Blog 2021
Patch Tuesday
Microsoft's Patch Tuesday provides both security updates and other non-critical fixes that have been pending since the previous month. While there have been issues with these updates in the past, there is a significant risk in delaying installation:
On the second Tuesday of each month, Microsoft and other tech companies release patches for consumer and enterprise users. These updates, including bug fixes and security enhancements from the previous month, are known as “Patch Tuesday.” The monthly update is an important opportunity to ensure that security features and applications are up to date.Since exploits from the previous month are detailed on Patch Tuesday, the following day often sees a spike in copycat attacks targeting unpatched systems. Organizations should prioritize applying critical security updates to mitigate this risk.
— Tech Republic
Keep Your Software Current
Once you've determined that your device is running the most current operating system, check that all the software (apps) running on it are currently supported by the vendor. All software becomes more dangerous to use unless it is updated regularly.
Vulnerabilities in Software
Most people only consider the newer technologies and features when upgrading their software or hardware but it needs to be updated regularly.
New versions address critical security vulnerabilities and can greatly improve stability and the ability to defend against malicious attacks.
Older, but supported, software may not include newer security features. It may also be dependent upon hardware such as computer motherboards and routers as well as recent versions of your mobile devices.
Just like the operating system, an unsupported software risks not only your data, but your privacy.
Software is generally supported (including the provision of free updates) until the vendor releases their next major version.
Mozilla releases new major versions of Firefox and Thunderbird regularly. Apple releases a new version of macOS annually. This provides the ability to respond quickly to security and hardware issues that may otherwise be hindered by existing components within the current build.
Most application vendors provide a upgrade discount to existing customers.
Check for Updates Regularly
“Check for Updates” at least weekly to determine if a newer version is available.
What Version Am I Running?
To find out what version is currently installed:
- Windows: Help ⇒ About
- Mac: Program Name ⇒ About.
Update to the latest available version or replace the software.
Some programs will then automatically update to the next version; others will open the download page on the vendor's website.
If the program doesn't auto-update, you MUST download the update then install the major updates from the vendor's website.
Remaining Current
If there is a new major update, you generally have to purchase it unless the software is freeware.
Be thankful that your software's vendor continues to provide updates and security fixes or you'd be forced to find a new program from a different vendor.
Interpreting the Version Numbers
Software version numbers are used to differentiate between different releases of the same software — usually major versions with minor updates.
For example, version 7.4.2 would breakdown as follows:
- The first number (7) indicates the major version number (the seventh generation).
- The second number (4) indicates a minor update.
- The third number (2) indicates a revision or potentially a bugfix.
Obsolete? Upgrade or Uninstall
Once software ceases to be regularly updated or is declared unsupported by its vendor, it is referred to as legacy software because vulnerabilities are no longer being fixed.
Uninstall Legacy Software
Legacy software needs to be upgraded or uninstalled and replaced.
New computers and software can be expensive.The problem with relying on an older computer is that updating to newer software — from apps to operating systems — can become more difficult. For example, your old applications may not work under the latest version of your computer's operating system without potential cost-extra upgrades themselves.
More importantly, relying on outdated operating systems, file- and print-sharing utilities, and applications can expose your computer and all the data you keep on it to tremendous risks.
— Acronis
Quit Using Legacy Operating Systems
This also applies to replacing Windows and other operating systems.
If your computer or device does not allow an upgrade to a currently supported version of its operating system, you must replace that device.
Purchase an Upgrade
If the vendor provides a newer supported version, updating the app is probably the best solution since you're familiar with that app's capabilities. In most cases the vendor will provide a discount for upgrades to the newer version.
Delete Unsupported Apps
If an upgrade to a supported version is not possible, even though the app is still useful you must uninstall it.
Replace If Upgrading Unavailable
Replace legacy apps with one that is newer and currently supported that provides the same function.
Purchasing a different application also provides the opportunity to review your requirements and to seek out new or improved features.
Whatever you decide, be sure it is safe to use and respects your privacy.
Keep it Clean
Uninstall any unwanted software. Regularly clear any unnecessary programs and data from your computer.
Unwanted software (sometimes labelled PUPs) can include the extra software that installs with your operating system or is included with your computer as well as third--party software piggy-backed on downloaded software or because of a misleading download page.
One example was the rapid adoption of Google Chrome because it was installed as an add-on to other free software. Once installed, Chrome made itself the default browser. If uninstalled, it made the legacy Internet Explorer the default browser — an unsatisfactory result for privacy or features.
Update Supported Software
As new vulnerabilities are discovered, supported software is updated to patch against it.
Keeping your operating system and your applications up-to-date is the best way to eliminate the vulnerabilities to your data. You'll avoid crashes by ensuring your system is running the most stable, enhanced version of the software you rely on — and will close the gaps that can give hackers a toe-hold in your system.
— Acronis Blog
Legacy Software: Dangerous to Use
Legacy software is software that has been declared unsupported by the vendor. Not only will there be no new features or upgrades, but vulnerabilities will no longer be addressed.
Over time, more and more unpatched vulnerabilities are discovered and exploited, making any legacy software increasingly dangerous to use, but especially the most popular brands.
No Security Updates
Legacy software no longer receives security updates from the vendor.
There is little financial incentive for vendors to upgrade older software and it is often difficult or impossible to add security features without completely rewriting the program.
New Vulnerabilities in Legacy Software
Just because a product is no longer maintained doesn't mean that new vulnerabilities won't be discovered and exploited.
Malware, zero-day exploits and other threats thrive in an environment of legacy software lacking the updates that repair these vulnerabilities.
Newer, supported versions of the software, will continue to receive security patches. Hackers then check legacy software to see if they have these same vulnerabilities.
Anytime a new vulnerability is publicized, our threat intelligence team observes widespread scanning for vulnerable systems.
— Unit 42
Legacy products will become more dangerous to use over time because old vulnerabilities are revealed when new software is patched:
Attackers are becoming faster at exploiting previously undisclosed zero-day flaws, according to Palo Alto Networks.The company warns in its 2022 report covering 600 incident response (IR) cases that attackers typically start scanning for vulnerabilities within 15 minutes of one being announced.
— ZDNET
Downloading Software
Be careful where you obtain software. Downloading and installing software from third-party sites can put you at risk. Your best options are to download from the vendor's site or from the official store for your operating system.
Assessing Software
Search for what others have said about a program using the program name as the search criteria. Blogs often provide interesting insight to the usability of such programs and their relative merits. Be careful to assess based upon current versions of the program. My recommended software is software I recommend to my clients.
Keep it Updated
All software requires maintenance, especially security software (be sure to update the updater regularly).
When a program is no longer maintained, uninstall it then find a currently-supported replacement.
Avoid Unwanted Programs
One of the things to look out for are the third-party optional programs (known as PUPs). These may be installed along with other products like Adobe Reader and CCleaner.
Krebs's 3 basic rules for online safety:
- If you didn't go looking for it, don't install it.
- If you installed, update it.
- If you no longer need it, get rid of it!
Scroll carefully through the installation option screens and be-select any extra software like Google Chrome, McAfee Security Scan, etc. before downloading or installing the software you actually wanted to install.
Refuse to download software from any site that makes it difficult to determine the correct download link. OlderGeeks.com is strongly recommended for reliable and tested software downloads.
32- or 64-bit?
Software is often available in both 32- and 64-bit versions. 64-bit versions are faster but you can only run them on 64-bit systems.
You can install 32-bit software on 64-bit systems, but not the reverse.
The Operating System's Store
Use the official store supported by your operating system where possible, especially for mobile devices.
- Apple Store
- Google Play
- Microsoft Store
The use of the official store is no guarantee that the apps you download have been vetted or are malware free.
Many apps on these stores have questionable experience and more than once there has been apps released that didn't follow proper security protocols thereby placing their users' privacy at risk, but the odds are better than downloads from an unknown source.
Online Vendors
Windows has a long history of supporting software from a wide range of vendors — much larger number of vendors than any other operating system.
Only install software you've downloaded from a recognized vendor's site. See installation hints for suggestions the help avoid problems.
Windows 10S won't install software downloaded from the web and Windows 11 settings may prevent that as well.
What About Mirror Sites?
Mirror sites should be avoided unless they are listed on the vendor's site and always contain the most recent version.
Shareware
Unlike regular software, shareware allows you to try it out to see if it works for you. After the trial period, you need to purchase a licence to continue using it.
While many shareware vendors provide excellent software and support, they are often one-person operations. Support can disappear without warning.
I've used many shareware programs over the years, including NoteTab Pro which is what I use to build and maintain this site.
Open-source Software
Open-source software is generally free and shares its program source with anyone wishing to view it. This can provide for greater confidence in the software if it is widely used and vetted.
Examples of popular open-source software include LibreOffice and VLC Player.
Freeware
Freeware is similar to shareware, except it is free to use without purchasing a licence.
I recommend searching for reviews or comments before using either shareware or freeware.
Free Software
There is some excellent free software available to you, including LibreOffice, Firefox and GIMP.
Unfortunately, many of the free utilities, screen savers and similar programs available on the Web contain either malware or collect information about you or install unnecessary third-party software.
A quick search should reveal any issues.
“Free to Play” Games Manipulate Us
While free to download and play, many such games are very profitable. How else could they afford to advertise during prime-time television?
"Free to play" games manipulate us through many techniques, such as presenting players with a series of smoothly escalating challenges that create a sense of mastery and accomplishment but which sharply transition into a set of challenges that are impossible to overcome without paid upgrades.
— Cory Doctorow
Software Security
Think about the security of your device when installing new software.
Install Security Software
I strongly recommend using security software on all your devices.
Choose your security software with care. You are trusting it to protect your data, your privacy and to secure your system from exploits.
Not all security software is as effective. See my recommendations.
You also need to protect your mobile devices. Most security software vendors support these in some fashion. However, mobile devices tend to be less safe than a computer.
Keep it Updated
Security software must be constantly updated to deal with emerging threats.
The time from the discovery of a vulnerability to when it is exploited is now less than a day. Zero-day exploits are usable immediately (zero days until exploitable) and affect even obsolete products that no longer receive updates.
- Check for updates at least daily.
- Weekly scans are a bare minimum.
- Real-time scanning is critical for today's threats.
Learn more about security software….
Secure Your Network
You cannot afford to be without an effective firewall. Today's computers and devices are continuously connected to the Internet.
No firewall is like leaving your front door open for anyone to walk into your home uninvited. Not everyone is polite enough to resist the temptation and curiosity captures too many.
Your Privacy Threatened
“Nothing to hide” is a falsehood perpetrated by those profiting by collecting and reselling your information.
Your privacy has never been under attack as intensely as it is today. You need to protect yourself using legitimate privacy tools.
Your Router
Your router not only secures your high-speed access to the Internet, but it allows you to share it between both hard-wired (LAN) and wireless (WLAN) computers, laptops, tablets, smartphones, game consoles, TVs and “smart home” devices.
While many issues have been fixed in newer routers, there are undocumented and unpatched vulnerabilities (zero day exploits) that both governments and hackers take advantage of.
More than half the routers currently in use are easily hacked. The recommendation is to replace your router if it is more than a few years old, especially if listed here.
Learn more about securing your network….
Strong Passwords
Passwords are an essential part of life today. They are used for everything from accessing your email to the millions of websites and forums that require you to identify yourself using a username/password combination.
Passwords and encryption can be effective tools — but only if you use them correctly.
Single Sign-on Flawed
Never choose to log into a third-party site using your Facebook or Google account (single sign-on). Instead, create a new login account using a strong and unique password.
Long and Strong
Make your passwords long and strong using random upper and lower case letter, numbers and symbols (some symbols are not permitted by some sites or vendors). Generally, the longer your passwords, the harder they are to hack.
Protect Your Passwords
Be sure that each site or account has a unique password. Reuse of passwords makes you vulnerable to identity theft.
Increasingly, sites are using your email address as your identity, making it very easy to hack your other accounts if you use weak passwords or use the same password on multiple sites. The following is only one example of how password reuse can have significant financial repercussions:
A total of 5,500 CRA accounts were targeted in what the federal government described as two “credential stuffing” schemes, in which hackers use passwords and usernames from other websites to access Canadians' accounts with the revenue agency.
— Times Colonist
Use a Password Manager
Everyone has far too many accounts on the Internet. Humans have too much difficulty creating and remembering effective passwords. You need a password manager.
I strongly recommend Bitwarden. Bitwarden is secure, encrypts the passwords BEFORE uploading them and can be shared between your various computers and devices.
Multifactor Authentication
Multifactor authentication (MFA) provides additional security that isn't available with even a strong password.
Recovery Options Weak
Instead of hacking your password, the “Forgot password?” recovery option on a site can provide a much easier place to obtain unauthorized access to your email account.
People post too much personal information about themselves on public places such as social media sites where the answers to typical security questions can be harvested. The nature of these questions are such that many are easily guessed:
- your favourite sports team(s);
- your favourite authors or movies;
- your best man or maid of honour at your wedding; and
- your home town or favourite teacher.
Many of these are items that you're prompted to include on your Facebook profile.
Protect Your Email Account
Some security protocols require you to respond to an confirmation sent to the registered email address for a requested password change. If your email account is protected by a weak password, this mechanism can be compromised.
Learn more about protecting your passwords….
Reliable Backups
There are many causes of data loss, including:
- hardware failure (hard drive or backup media)
- ransomware attacks
- lost devices
- theft or vandalism
- environmental disasters (fire, flood, earthquake)
More and more our private information is electronic and stored on our computers or devices.
From the dawn of civilization until 2003, humankind generated five exabytes of data. Now we produce five exabytes every two days…and the pace is accelerating.
— Eric Schmidt (2010)
Learn more about backup strategies….
Planning for Recovery
The first step in planning for recovery is to ensure that you regularly backup all your data using reliable systems and schedules. The more frequent the backups, the less that can potentially be lost.
Having multiple generations of backups ensures that a problem with one set can be resolved with an older backup (you might not get everything, but most of it will be there).
You should also plan for disaster by ensuring off-site backups either via cloud backups or physical backups stored offsite.
Unfortunately, cloud storage data is threatened by poor security and government data collection policies.
Installation Hints
Ensure a smooth installation experience and help avoid potential issues with optional software that you neither need nor desire.
Use Trusted Sources
Always download software from a trusted source, like the vendor's site.
Avoid the ads at the top of search results. Sponsored links are seldom good choices.
Uncheck Optional Downloads

Watch out for “pre-checked” options like this example:
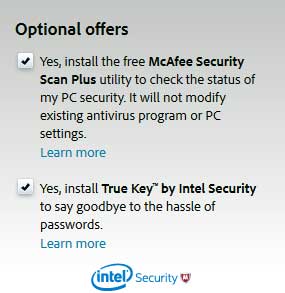
These added items help to keep this software free, but it are still optional.
Uncheck any pre-selected options before downloading the software (unless you truly want or need it).
Once downloaded, you seldom can avoid installing this extra software.
Assumed Consent Illegal
Canada's Anti-Spam Legislation, makes presumed consent illegal.
The manner in which you request express consent cannot presume consent on the part of the end-user.Silence or inaction on the part of the end-user also cannot be construed as providing express consent.
For example, a pre-checked box cannot be used, as it assumes consent.
— CRTC
Most software is sourced outside of Canada and may not abide by Canadian laws.
Check During Installation
After downloading the software, check for unwanted options while installing.
Google Chrome has become very popular by surreptitiously installing itself as the default browser as a paid add-on to other free software such as AVG, Defraggler and Adobe Flash:
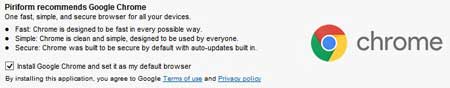
Although it was an “optional” addon, it was pre-selected. Folks simply clicked through the options without checking them for extra software or anything else.
Review the Options
When installing the software, carefully review the options. Watch for:
- any extra (optional) software;
- permission to share app-usage data or help improve the app;
- third-party licence agreements; or
- unacceptable licence terms
Uncheck options you don't want before clicking “Next.”
Unwanted software can slow or harm your computer.
- Malware can be introduced.
- Add-on security software can compromise your protection.
- Google Chrome might replace your browser without asking.
- Toolbars can invade your privacy.
Some apps ask for unnecessary permissions that threaten your privacy.
Assumed Consent Illegal
Canada's Anti-Spam Legislation, effective July 1, 2014, includes definitions for presumed consent and express consent. The Act has significant fines for non-compliance.
The manner in which you request express consent cannot presume consent on the part of the end-user.Silence or inaction on the part of the end-user also cannot be construed as providing express consent.
For example, a pre-checked box cannot be used, as it assumes consent.
— CRTC FAQ about CASL
Invest in Good Software
Much of the software listed on this page is free. You have no obligation to pay for or donate to the vendor.
But consider this:
- The software developer will likely be making new improvements or fixes only if there is income as a result.
- Free software is usually supported by the sales of paid versions of the product.
- Some free software, like Mozilla Firefox, is supported completely by donations.
- The paid versions usually have more features and are updated more frequently.
- Purchasing shareware or providing a donation to the developer of useful software makes it more likely that it will be available to you in the future.
Subscription Services
Software traditionally was purchased outright with the understanding that it would be supported for a number of years. Microsoft Office was supported for 5–10 years, with new features and improvements only provided in the first five years and security fixes after that.
More recently, software companies have moved away from that, to provide traditional software licensed as a subscription service or Software as a Service (SaaS is more commonly aimed at corporate users).
Microsoft 365 is an example of software that used to be a one-time purchase which is now paid via a monthly fee (often annualized).
Don't Use Pirated Software
Don't be tempted to download “free” copies of commercial software unless it is legal.
Pirated software usually contains malware (and if it doesn't, the site you obtained it from is probably infected).
- There are free alternatives for most commercial software packages if you truly can't afford them.
- Few people need the full functionality of commercial software outside of a corporate environment.
- Some open source software (e.g., GIMP or LibreOffice) compare very favourably with their commercial counterparts.
Related Resources
On this site:
- Resources index
- Security strategies
- Security policies
- Security software
- Malware & spyware
- Firewalls: your first line of defense
- Passwords: your electronic signature
- Encryption: protecting your data
- Your privacy at risk
- Restoring privacy
- Oversharing on social media?
- Spam: unsolicited emails and mailing lists
- Identity theft
- Phishing & email scams
- Phone fraud
- Mobile security


