Home Networking
Configuring and securing your network
What is a Network? | Setting Up Your Network
Configure Your Router | Secure Your Router | WiFi Security
Guest Accounts | Troubleshooting
All trademarks, company names or logos are the property of their respective owners.

Wi-Fi is a Wi-Fi Alliance standard. WiFi is used to refer to generic wireless.
Don't be a victim! Malicious cyber actors may leverage your home network to gain access to personal, private, and confidential information.Help protect yourself, your family, and your work by practicing cybersecurity-aware behaviors, observing some basic configuration guidelines, and implementing the following mitigations on your home network, including:
- Upgrade and update all equipment and software regularly, including routing devices
- Exercise secure habits by backing up your data and disconnecting devices when connections are not needed
- Limit administration to the internal network only
- — National Security Agency
Consider these recommendations to ensure that your network is secure:
- Create a security policy for the computers in your home or business.
- One person should be responsible for network configuration and security.
- Use only currently-supported software and hardware.
- Use quality security software.
- Follow best security practices to avoid phishing attacks and identity theft.
See the National Security Agency's guidelines: Best practices for securing your home network (PDF).
What is a Network?
A network is a collection of interconnected computers and other devices that are capable of talking to each other. In simple terms, networking is connecting two or more computers or devices together to share files, high-speed Internet access or resources like printers and scanners.
- The most immediate network is the one inside your home or business (your home network).
- The next is your connection to your ISP (another network).
- Your ISP connects to the Internet (a world-wide network) through a regional collection of related networks.
Connections to the network can be either wired (via a network cable) or wireless (via WiFi) or both.
- Devices like smartphones and tablets only connect via WiFi (wirelessly).
- Most recent laptops only connect via WiFi. Older ones can also connect via a network cable.
- Most desktop computer connect via a network cable but many recent computers have built-in WiFi.
Let's have a look at how each of these may be involved in the chain of connections from your computer to the website or service you're trying to reach.
Your Home Network
Your most basic home network is your computer connected directly to a modem provided by your ISP (usually a router/modem combination). The router provides access to all other connected devices connected to your network as well as to the Internet. Whether these devices can talk to each other (i.e., share information) depends upon how the network and the devices are configured.
Your network should be secured using unique long and strong passwords for both your router and your WiFi.
Your ISP
Your ISP (Shaw, Telus, Rogers, etc.) provides your connection to the Internet via their own network (which includes all their customers' networks).
Your ISP then connects through a network of additional connections to the Internet (originally designed to withstand a nuclear attack by switching automatically to whatever routing is available).
Problems Connecting?
If you cannot get access to the Internet, check your router. Testing with more than one browser on more than one site will tell you if the issue is with a particular browser or site or if the connection isn't working at all.
If the problem is with your ISP's connection to the Internet, there is nothing you can do except wait for them to restore access. You may need to reset your router once connection is restored.
ISP Resources
How your Internet comes into your home or office as well as what is supplied can differ with your ISP. It is mostly Rogers (formerly Shaw) or Telus in Victoria:
Public Networks
Public networks include free community WiFi networks, coffeeshop WiFi, public library networks and other similar Internet connection that you don't control.
You may be connected using your own laptop, tablet or smartphone or you may be using a public computer (such as those provided by a library or school).
If you're having difficulty connecting on a public network, you'll need to talk to the staff to determine how to resolve the issue. Sometimes the staff are unable to fix the issue, particularly if the service is managed remotely.
You Can't Trust Public Networks
If you are using public access from a connection that you don't control (something other than your home network) or one that isn't secured properly (you haven't changed the default passwords or enabled security) then you are placing your computer, devices and data at risk.
Everyone on an insecure (public) network such as a coffee shop can potentially “see” the information you are sending and received on that WiFi service. All it takes is some software that is easily obtained on the Internet.
Even if you're using a gated network (one that requires you to sign on), you can't trust it unless you control that network.
NEVER sign in to Internet banking or similar risky activity on a public network.
Cellular Networks
Cellular networks are those provided by cellular ISPs. These networks are separate from the typical home or business network and usually have relatively small data caps. Cellular networks are fairly reliable (the number of cell towers and their location determines the strength of your signal) but can sometimes go down.
Cellular service is more secure than free WiFi. However, just like your home network, everything you do on your cell is visible to your cellular provider unless you use a VPN.
Other than ensuring your cellular service is turned on for your device, there is little you can do to resolve connection issues other than to move to an area with better reception or call your cellular provider for assistance.
Securing Your Network
It is important that you secure your own network. It is beyond the scope of connection issues, but there are resources on this site that will help you to do that.
At the very least, you should change the default admin password used to manage your router and the password(s) to connect to WiFi. There are more advanced settings, but be sure you understand the changes you're making.
Setting Up Your Network
Creating networks has become easier and less expensive. Most high-speed ISPs provide some sort of a router-modem combination.
The process involves three basic steps:
- Configure your router;
- Secure your router; and
- Add other computers and devices.
Considering What You Need
Before you begin, lets go over some basic preparations. You'll want to determine what you need your network to do so you plan for those requirements and any future expansion.
This includes how your network of computers will be connected as well as how much Internet capacity you need and how many devices may be active in your home or office.
How Much Do You Need?
- Light users: If you only use the internet for basic tasks like email and occasional web browsing, you won't need a lot of speed.
- Moderate users: If you use the internet to stream video, music, or occasionally to do online gaming, you'll need more speed.
- Heavy users: If you download a lot of music and movies or play online games frequently, you'll need a fast connection.
- — Verizon
Verizon's “What is a good internet speed?” is based in the U.S.
While Verizon's plans and discounts are irrelevant to Canadians the guidelines for determining the sort of bandwidth requirement including those for remote workers & distance learners, file sharing, video streaming and gaming are excellent.
You'll then need to take that information and seek out similar capabilities in plans available from the providers in your area.
There's more discussion about the factors affecting bandwidth requirements below.
Wired or Wireless?
Further down is a discussion about the capabilities of both wired and wireless connections. Wireless speeds and bandwidth has increased significantly. While this may still affect how you place your equipment and affect how many devices can use your network simultaneously, it avoids having to place computers beside your router or drilling holes in walls.
How Many Devices?
First, consider what devices will need connection to the Internet and to each other. The largest part of this for most people will be easy access to the Internet.
Think of the Internet connection like a hose or a pipe. Think of using a garden hose and the massive hoses used by fire fighters. One is fine for watering the grass but you need the other if you wish to put out a house fire or pump out a flooded basement.
If you're only connecting one computer for surfing the Web, social media and checking your email, your needs are going to be far less than a family where there are four computers, four smartphones, two tablet or more.
Working from Home?
If you're working from home (or attending online courses) then the Internet is more than a form of entertainment. Weaknesses in security and dropouts can affect your business or education.
If you are using online meeting software like Zoom or Webex, your experience will be improved if you have sufficient bandwidth and your spouse or kids won't be forced to stop using the Internet during important meetings.
“Smart” Devices
Don't forget the various smart components in your home like security cameras, locks, assistants (e.g., Google Nest Mini), Amazon Ring, thermostats, light controls and more. More and more devices are requiring access to the Internet including the fancy exercise equipment you see on TV, TVs themselves, streaming services, and much more.
I'd recommend reviewing the privacy issues these devices pose including checking Mozilla's *Privacy Not Included for a privacy report.
Think About Future Use
Don't just think of what you're doing today, consider the potential for the next several years. Your needs are highly likely to increase as you use higher definition video and do more streaming than traditional TV programming.
It isn't uncommon for ISPs to require you to commit to a contract to get their best prices. Don't be locked into a plan that may not work for you or your family next year.
Do You Need to Share Between Devices?
Today's operating systems (e.g., Windows, macOS) are designed to start working on a project on your computer then finish it on your phone or tablet. You may also wish to sync files between a desktop and laptop computer or share family photos with all the devices in your home.
Knowing what you plan to do enables you to prepare your network.
- How to find the upload and download speed on your PC.
- How to share an Internet connection.
- How to connect two computers.
- How to view files on a networked computer.
- How to network computers: Windows or macOS.
Wired or Wireless?
Most current routers provide for two types of connection to the network:
- Wired (LANs) using Cat 5 (or faster Cat 6) Ethernet cables. Routers usually provide for up to four wired connections.
- Wireless (WLANs) using radio signals that carry the information between the various devices on the network. Wireless networks allow you to connect dozens of devices.
The most secure method on connecting is by using network cables. However, unless you're able to run these cables throughout your home or office, the location and number of devices that can connect this way is limited.
WiFi Expands Accessibility
Wireless networks are easier to set up, but there may be limitations because of the walls or other interference between the router and certain areas in your home or office.
Tablets, smartphones, printers, TVs, virtual assistants (e.g., Google Home) and many other devices are now capable of connecting with wireless technology. You can add this capability to some devices with third-party hardware.
WiFi Security Considerations
There are also special WiFi security concerns.
Be wary of any device that requires you to downgrade the security of your wireless network. Most such devices are older and you have to remember that wireless signals can reach the neighbours and out to the street in some cases.
Connecting Through Electrical Wires
Although there has been a lot of progress in wireless technology using repeaters and other options, some locations are difficult to reach.
Special networking hardware designed to connect through the electrical wiring in the building can bring connectivity where you have difficulty running either network cabling or getting a reliable wireless signal.
Security Considerations
This is not a good solution if you're in an apartment, basement suite, duplex or similar situation where other tenants are sharing the same electrical box.
The main issue with all Powerline network devices having the same out-of-the-box default network name is when you live in an apartment, dorm, or other situation where the electrical wiring is shared. If two or more different apartments start using Powerline networking products with the same network name, then they are essentially sharing their network with each other, which could lead to all manner of security and privacy issues.
— Lifewire
Buying a Router
While the router supplied by your ISP might work well at home, if you're a business or are having difficulties with your network you can try these resources:
- Choosing the best wireless router.
- Best WiFi routers for a large house or office.
- The 8 Best WiFi Extenders.
Planning Resources
The following sites have more information about planning and setting up a network:
- How home networking works on Howstuffworks.
- How to set up and optimize your wireless router from PCMag.
- The ultimate guide to home networking from PCWorld.
- Home Network on Wikipedia.
Configure Your Router
The router controls access to the Internet as well as connections between computers and devices on your network.
Take care to secure your router. Without proper security and updating your router can be compromised, endangering the devices on your network.
Access Your Wi-Fi Router's Settings
Having trouble with your wireless?
Here's how to sign into your router to change your home network's name, password, security options, and various wireless settings.
— PCMag
Be sure you understand the changes you're making.
An Overview
This is a very brief overview of the connection process. You will need to carefully follow the instructions that came with your router which may differ from this generic guide. Most routers come with setup instructions.
Your router may be configured as a separate high-speed modem connected to an external router or as an all-in-one combined modem/router supplied by your ISP (most common). See Routers: Your Hardware Firewall for special instructions on securing your router.
Don't Use Wireless to Configure a Router
Always configure a router using a wired connection. A wireless connection risks losing the signal when the router reboots during setup.
Connect to the router directly with an Ethernet cable until the setup and configuration is completed. Once complete, you can return to a wireless connection if you wish.
Router Setup
The first step is to setup and configure your router.
Follow these steps in order (unless directed differently by your router's installation guide) so that any problems can be rectified before you move on:
- Make sure the high-speed connection is working on the computer connected to the modem or router.
- You don't want to complicate things by tackling the rest of the network before determining that your Internet connection is active.
- Make a note of the items that your router installation guide suggests you record.
- You will need this later to configure the router.
- Install the router's software when setup tells you to.
- This software makes changes to your computer. Be sure to include any recovery options.
- Advanced users may prefer to use their operating system's configuration tools.
- Remove the network cable from the back of the computer and plug it into the WAN port on the back of the router.
- Connect a network cable from one of the numbered ports to the back of the computer.
- It does not matter which numbered port but I tend to use port 1 for my main computer.
- Do not use an “uplink” port.
- Set your router up using the instructions provided by the manufacturer.
- This is where you will need the settings you recorded earlier.
- This sometimes requires rebooting the modem, router and computer.
- Check your Internet connection on your computer.
If the computer can't access the Internet, you'll need to figure out where you went wrong before continuing.
Secure Your Router
Once you have your router working, log into the router software interface and ensure that you've secured your router from being hacked.
The configuration varies by manufacturer, so have a look at your router's manual or help menu.
Use a network cable to perform these options.
Configuring the security settings is usually achieved by entering a local IP address (e.g., https://192.168.1.1) into your browser's address bar.
- Replace the default router login password with a unique complex password and optimally the login username as well.
- Disable any remote access to your router (check your router's documentation to locate and configure this setting).
- Replace the default WiFi security and passwords with the best security your device allows.
Don't Configure Routers Online
Some router manufacturers (such as Netgear) don't provide a local IP address. Instead, they have moved the configuration of their routers into the cloud:
Type http://www.routerlogin.net in the address field of your browser, and then click Enter.
Configuring routers on the Internet makes it easier for your router to be hacked, especially if HTTPS is disabled.
The site now redirects to the more secure https://www.routerlogin.net/ address.
Try These Local Addresses
First, try entering 192.168.1.1 or 192.168.0.1 into your browser's address bar.
If these don't work, search for documentation for your particular brand and model of router. Often you can find answers in online forums.
Update Your Router Firmware
Just like other hardware and software, it is very important that you update your router hardware and software when possible, replacing it when it is no longer secure.
Ensure your router's firmware is always up to date.
Replace Aging Routers
If you can't update your router and it uses wireless G (or older) or is vulnerable to the KRACK security flaw replace your router.
If your router is provided by your ISP, you might talk to them about upgrading. Alternatively, disable WiFi and use only wired connections.
KRACK WiFi Security Flaw
A WiFi critical flaw in the WPA2 security standard, KRACK, affected virtually all devices. Windows and Apple devices are only partially affected and currently supported versions have been patched with updates.
WiFi Security
WiFi security protects your network from being attacked or used by unauthorized devices to access the Internet.
Guest Access
Don't compromise your WiFi security by allowing outside users (guests) to use your primary network. Instead, set up a guest WiFi network so that guests can access to the Internet but remain isolated from the main network.
Wired Network More Secure
Wired networks are more secure because they don't transmit information except to the connected devices via the network cables.
However, WiFi is more convenient and more practical for most home users.
Disable WPS
I strongly recommend that you disable WPS.
WPS is “push-button” technology that makes configuring devices on a wireless network easier. Easier, but a serious security risk.
Secure Your Wireless Network
It is very important that you secure your wireless network — you do not want your network or Internet service accessed by others. It is relatively easy using the tools provided by the manufacturers of wireless equipment.
Since no encryption is totally secure, use a wired network if you are concerned about confidential information. Be sure to disable the wireless capability on the router.
Wireless Security
A wireless key provides security for your wireless network just like a password provides security for your email account:
- The WiFi SSID is like your email address.
- The WiFi security key is like your email password.
In both cases, this information is public.
Security Protocols
There are several protocols used to secure wireless networks. The most common are (in order of increasing security):
- WEP;
- WPA; and
- WPA2.
WEP Not Recommended
WEP is an obsolete encryption method.
- WEP security uses only the digits 0–9 combined with letters A–F and sends a portion of the WEP security key each with each transmission so it is less secure than more recent encryption methods.
- The longer the key, the harder it is to break, and is therefore more secure. Use 128-bit encryption where possible and always mix letters and numbers in a random order.
WPA
WPA was designed to overcome all know security issues with WEP. WPA utilizes 128-bit encryption keys and dynamic session keys to ensure the wireless network's privacy and security. There are two general variations:
- WPA-Personal uses a pass-phrase or pre-shared key (sometimes referred to as personal mode) and is used for home and small office networks. This is sometimes referred to as WPA-PSK.
- WPA-Enterprise verifies network users through an authentication server and is used in large networks.
WPA2
WPA2 uses an AES encryption algorithm for increased security. Most current routers support some form of WPA. WPA2-Personal and WPA2-Enterprise versions operate in the same manner as their WPA counterparts.
Learning More
Check out these sites for more information about wireless security:
WiFi Resources
- The Wi-Fi Alliance has lots of resources on wireless networking.
- How to set up a wireless network (WiFi) connection.
- How to connect to WiFi in Windows 10.
- 10 Wi-Fi configuration tips from Apple for better wireless connectivity, performance.
Adding Other Computers
Once you are sure the main computer is working correctly and the network is secured, you can connect the other computers and devices to your network — one at time.
- Add the other computers that will be connected using a network cable into one of the remaining numbered plugs. Be sure to check their connectivity as you go. You may need to reboot each computer so that it sees the new network address or change the IP address.
- Add the wireless computers one at a time. You will need to configure each computer's wireless receiver according to the instructions you got with the unit.
- Add any other wireless devices like printers, scanners, smart phones, tablets, etc. one at a time. Use the instructions and/or software that came with these devices. Once connected most will prompt you to verify access by printing or scanning a test page. Do this on your primary computer first, then verify the capability where remote printing is enabled elsewhere on the network.
See sharing files between computers to learn how to share files between computers on your network.
Guest WiFi Accounts
“Hey, what's your Wi-Fi password?” You probably hear these words every time new guests enter your home, especially if your place gets poor cell reception.As a good host, your first thought may be to hand over the login details. However, allowing guests to use your main Wi-Fi network can expose all connected devices to threats like data breaches and the spread of malware.
— Norton
You want to separate visitors' access from the rest of your network. This will ensure that your own network remains separate and secure — so you can protect your own devices from threats from your guest's devices and online activities.
Dual-band Routers
Many routers now offer dual-band access (two bands, one at a higher speed). Each is protected by a separate SSID and password and runs its own network. Use the second Wi-Fi network as your “guest” network so you don't compromise the Wi-Fi password on your primary network.
Give priority to your own requirements by using the higher bandwidth Wi-Fi and the wired network for the internal network. The lower bandwidth Wi-Fi will provide access to visitors and unknown devices without compromising performance on your in-house network.
Ensure Adequate Coverage
You'll want to be sure your coverage has adequate bandwidth for additional users as well as being accessible from where your guests will be using it. Test your guest Wi-Fi in areas where guests will be wanting access. Don't forget to test your outside deck if you entertain there.
If your house is full of dead zones and slowdown spots, your guests are going to have a bad time. So, if you've ignored that spotty Wi-Fi coverage because it only really affected the guest room, I'd say there's no better time than now to fix it up.You may also need to invest in a good Wi-Fi extender or mesh system, which will rebroadcast your router's signal to the furthest rooms, ensuring you always get a strong connection, no matter where you are.
— PCMag
- How to set up a secure guest Wi-Fi network.
- Hosting this summer? Here's how I set up my wireless network for guests.
Troubleshooting
Before troubleshooting your network, you'll need to ensure that you have a working Internet connection.
Renewing the IP Address
Rebooting your computer is not the only method for renewing the network address. You can use ipconfig at the command line following the instructions here:
- Click on Start then type cmd in the search box.
- Click on the cmd.exe that appears. When the command line window appears, click on it and a cursor will appear at the end of the last line.
- Type ipconfig /release to release the current IP address.
- Now type ipconfig /renew to renew the IP address. Not all devices may be active.
- Now, close the command line window and ensure that you can access the Internet and your network is available.
Network & Internet Settings
- Right-click the network connection icon; then
- click Open Network & Internet Settings
Alternatively, open Settings ⇒ Network & Internet.
This is where you can configure your network and determine the current status of your network connections.
Windows 10 displays a simplified diagram and is found in Settings:
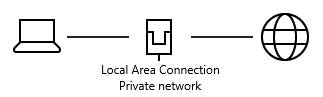
The icon will be different if you're using wireless to connect or if you're off-line.
There should be solid lines between your computer, the network and the Internet. If there isn't, click on Troubleshoot problems and follow the prompts.
More About IPCONFIG
The following resources can tell you more about the ipconfig command options:
Boosting Your WiFi Signal
We have connected devices all over the home these days. If you require connection in an area that isn't easily reached from your router's location, there are some ways to boost the signal.
WiFi repeaters, boosters and extenders are pretty much the same thing — devices to improve WiFi coverage. Even though you won't find a clear difference between “repeaters” and “extenders” not all of them will work the exact same way.
— NetSpot
- 10 ways that you can boost your WiFi signal.
- What is Mesh WiFi? (& why you should absolutely get one) - YouTube.
- How to boost a WiFi signal (recommended for those that like illustrations).
- Best WiFi extenders - TechRadar.
- The best WiFi extenders - Tom's Guide.
- Best WiFi extenders: Top devices for boosting your WiFi network.
- The best wireless range extenders - PCMag.
Related Resources
On this site:
- Resources index
- Internet connection issues
- Sharing files between computers
- Security basics
- Security software
- Malware & spyware
- Ransomware
- Firewalls: your first line of defense
- ZoneAlarm security products
- Vulnerabilities in Windows
- Passwords: your electronic signature
Return to top
RussHarvey.bc.ca/resources/network.html
Updated: June 14, 2025

