Terminology
Software, hardware & Internet
Introduction | File Names | Software | Hardware
Internet Connections | Software Versions
All trademarks, company names or logos are the property of their respective owners.

Common terminology like the hardware capabilities shown on the image above can be confusing for many people.
This page was designed to provide basic explanations of terminology used on this site. It may include links to other sections of this page or elsewhere on the site as well as outside (external) links which contain additional details.
Wikipedia has more detailed information.
Introduction
A “computer” includes hardware, an operating system as well as the applications installed on that computer.
Hardware is the physical components that make up the computer, including the main computer (motherboard, processor, RAM, hard drive, video card, etc.), keyboard, mouse and monitor.
It also includes peripherals like the printer, scanner, microphone and speakers. Computer components are defined here. Often components like video cards and network cards are embedded on the motherboard, especially with laptops and brand-name desktop computers.
The operating system (OS) is a special type of software that allows the user to interface with the device's hardware and applications.
The applications (sometimes referred to as apps) are the software programs that run on the computer or even specific hardware (e.g., Intel or Silicon with macOS software). Most software specifications indicate which operating system(s) are supported and usually a different installer is provided for each supported operating system.
Computer File Names
File names are the names given to specific files (documents, images, PDFs etc.). Many of the same rules apply to the folders (or directories) containing these files.
The naming conventions can differ between operating systems. Most current operating systems allow long file names, including spaces and punctuation, for most documents.
Current Virtual Reality Technology is Improving.docx would indicate the name of a Microsoft Word document containing 52 characters and spaces.
- Windows uses extensions like .docx, .jpg, .txt, etc. to identify the program that should open the file.
- Macs use a hidden file for that purpose (it shows up as ._.DS_Store on Windows computers).
Size Limitations
Windows will allow up to 256 characters and spaces. This limitation includes the names of the series of directories (or folders) between the root of the hard drive (e.g., C: or D:) and your file.
Most current operating systems display directories as folders, but they can also be displayed as a series of folder names separated by a back slash. For example, this Windows file:
D:\Documents\Ref\Facts\Technology\Virtual Reality Improving.docx
- is a Microsoft Word file
- with a 30-character file name
- located on the Windows D: drive
- whose total size is 64 characters when including directory information.
The use of drive letters is a feature of Windows. Some other operating systems have different methods of designating the location of files and folders.
Nested Folders
As this series of “nested” folders (folders contained within folders) gets deeper, the total number of characters involved gets longer. Our example above has four folders nested within each other:
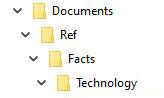
Even if you are able to access the file and open it in Word, your backup software may be unable to copy it, especially if the files are saved into another nested folder on the external drive (adding additional characters in the path).
Is it Case Sensitive?
Unless you know otherwise, assume that all file names are case sensitive (i.e., it matters whether or not the letters are upper or lower case). Even if your operating system isn't fussy, website filenames (URLs) are.
For example, Homepage.html and homepage.html may both open as local files within Windows, but requesting homepage.html online when the actual file name is Homepage.html on the Internet will not work. For this reason, I tend to use all lower case when naming web pages.
Email addresses, on the other hand, are NOT case sensitive.
Software Basics
Software includes both the operating system and the applications that run on that operating system.
For the most part, software is designed to run on a single operating system although it can be ported (or translated) to run on more than one.
Java was a language that was intended to overcome this limitation, but significant vulnerabilities have made this less appealing and it is no longer in common use on consumer computers.
Open Source
Software is generally classified as either “open source” or “closed source” based upon who can legally examine or modify the source code.
Open Source Products Can Be Viewed or Altered by Anyone
In open source software, the source code (the programming behind the software) is open to anyone to view, alter and modify. Software like LibreOffice and Firefox are open source and developed by large teams of individuals.
Open-source software (OSS) is a type of computer software in which source code is released under a license in which the copyright holder grants users the rights to study, change, and distribute the software to anyone and for any purpose.
— Wikipedia
When a product is open source, it means that any security flaws or unreported collection of private information is much easier to discover, at least when there are significant numbers of people looking at the project.
Wherever security or privacy is important to you (and they always should be) you'll want to look for well researched open source software.
Closed Source (Proprietary) Software is Locked
Most commercial software is proprietary and its source code is closed to outside developers. Microsoft Word and Adobe Photoshop are strictly controlled by Microsoft and Adobe respectively.
Some software has source code that only the person, team, or organization who created it — and maintains exclusive control over it — can modify. People call this kind of software "proprietary" or "closed source" software. Only the original authors of proprietary software can legally copy, inspect, and alter that software.
— OpenSource.com
Because the source is closed, it is harder to determine if the developer's claims about security and privacy are true, particularly given the current trend to classify such research as “hacking” and therefore exposing researchers to significant penalties — even jail.
If the widespread collection of private information (metadata) by companies was classified in the same manner we would all be more secure.
Operating Systems
The operating system (sometimes abbreviated as OS) is the main software running on a computer and will dictate a great deal about what hardware will work and what software is available to run on any particular computer or device.
PCs and Laptops
Current computer operating systems include various versions of Microsoft Windows, Apple macOS (Mac) and Linux as well as some lesser-known ones like IBM OS/2.
Mobile
Mobile devices run operating systems as well: Apple's iOS or iPadOS and Google's Android are examples.
Raspberry Pi
Programming is a valuable skill as well as a fulfilling hobby. Once people were able to program most computers but is either locked or requires expensive programming software.
The Raspberry Pi, a very basic computer, was developed to reintroduce the challenge of computer programming and experimentation at a price that anyone can afford (from $35).
The Command Prompt
Earlier versions of PCs ran command-line operating systems like DOS which forced people to understand something about programming.
Newer operating systems have been designed to be so user-friendly that the vast majority of today's users lack any real understanding of what is going on in the background.
Windows still has command-line options using the Command Prompt which vary between Windows versions.
- Command Prompt: What it is and how to use it.
- 10 ways to launch the Command Prompt in Windows 10
- Windows Commands.
Windows 10 offers the Windows PowerShell as a Command Prompt alternative.
Windows PowerShell is a task-based command-line shell and scripting language designed especially for system administration. Built on the .NET Framework, Windows PowerShell helps IT professionals and power users control and automate the administration of the Windows operating system and applications that run on Windows.
— Microsoft
- PowerShell documentation.
- Starting Windows PowerShell
- Windows PowerShell scripting tutorial for beginners.
Linux retains command-line options, mostly for power users.
- 13 Linux network configuration and troubleshooting commands.
- Linux network commands used in network troubleshooting.
Swift
Swift, a program originating at Stanford University, is freely available to develop applications for the Apple operating systems:
Swift is a powerful and intuitive programming language for macOS, iOS, watchOS, tvOS and beyond. Swift code is safe by design, yet also produces software that runs lightning-fast.
— Apple
Applications
Applications (or apps) generally refers to software programs that can be installed onto a computer. It can also refer to the utilities and other software that comes preinstalled with an operating system (e.g., NotePad in Windows).
Applications used to be called programs or software programs on computers. Because of the convergence of computers and mobile devices it is more common to also refer to programs on computers as apps.
On mobile devices these are usually referred to as apps (short for applications) which are downloaded from the device's app store.
Windows 10 has an app store that has some significant issues (it was built for the now-defunct Windows Phone). If you're running Windows 10S (S for “secure”) you can only install apps from the Microsoft Store.
Programs Usually Run on Only One Operating System
In most cases a program is designed to run on a single operating system (e.g., it will run on Windows but not on the Mac).
Where there are both Mac and Windows versions you generally have to purchase each version to run them on both systems. The licence for software like legacy Microsoft Office is seldom transferable between operating systems even if you stop using the old operating system.
Exceptions
As software moved to cloud-based versions and people began to use more than one device, solutions like Microsoft 365 (formerly Office 365) allow the user to install the application on more than one device and/or operating system.
This software tends to be licensed on a monthly or annual basis rather than sold.
Java
Technologies like Java were developed to provide cross-platform compatibility (meaning that software will run on more than one operating system). Unfortunately, the universality of Java combined with Java's security vulnerabilities has led to the recommendation to stop using it.
SaaS
SaaS (Software as a Service) lets remote servers do the heavy lifting, allowing less powerful devices to handle more difficult computing tasks than they could in the past.
Windows 10 uses SaaS including employing Bing for local search results
If you do your taxes online, use Google Docs or a Chromebook, you are using SaaS.
Software Classification
Software is often referred to in generic terms based upon its purpose.
Instead of referring to a specific piece of software running on a single operating system (e.g., Pages running on macOS) you can refer to generic software classes (e.g., word processing or spreadsheets) rather than the program itself (e.g., Microsoft Word or Apple Numbers).
Software falls into different classes. Examples:
- word processing suites include Microsoft Office and LibreOffice;
- Internet software includes Firefox and Thunderbird;
- graphics software includes GIMP and Irfanview;
- utilities include CCleaner and Defraggler; and
- security software includes security suites like ZoneAlarm Security.
Moving into the “Cloud”
An emerging trend is storage in the “Cloud” which is the generic term given to any service or software located on servers accessed via the Internet. Webmail is an example of a cloud-based email service.
Be Aware of Data Breaches
It is important for you to understand that the Cloud is not as untouchable as it sounds.
Many of cloud services have suffered significant data breaches where user data has been stolen — usually because the security protection was much less capable than these companies used for their own data.
Mobile Often Dependant Upon Cloud
The cloud has been an important component in the development of powerful mobile devices.
Cloud-based storage provides interconnectivity to multiple devices wanting to access the same information from anywhere.
SaaS is Cloud-based
The Internet has permitted the development of programs that run on remote servers rather than on device itself (SaaS).
Rather than purchasing and upgrading software on your computer, you pay a company a monthly fee to maintain the program (or are presented with ads to pay for a free service).
WordPress and Gmail are obvious examples, but many programs that formerly ran on your computer like Microsoft Office and Photoshop have been replaced with cloud-based software like Microsoft 365 and Creative Cloud.
Some features in Windows 10 are web-based, such as the search function (which is why you see results from Bing as well as from your own computer).
Chromebooks are almost entirely web-based, which is how they can be so much less expensive.
Cloud-based Storage
Examples of cloud storage are DropBox, Apple's iCloud and Microsoft's OneDrive.
Hardware Basics
Hardware, as noted earlier, is a generic term for the physical aspects of your computer and the devices connected to it (like scanners and printers) as well as the components that make up the computer itself.
32- or 64-bit Computing
When using the terms 32-bit or 64-bit in computing, we're primarily describing how memory is addressed. This affect both hardware and software.
When attributing 32- or 64-bits to software (programs or operating systems) we are describing the hardware requirements to run that software:
- 64-bit software will only run on a 64-bit operating system installed onto 64-bit hardware.
- Most 32-bit software will run on both 32-bit and 64-bit operating systems.
- 64-bit operating systems cannot be run on 32-bit hardware nor can 32-bit operating systems support 64-bit programs even if that operating system is installed on 64-bit hardware.
64-bit is Faster
64-bit hardware can utilize larger amounts of RAM (system memory).
Just as larger amounts of traffic can move faster on an 8-lane highway than on a 2-lane roadway, 64-bit hardware allows for more RAM to be utilized and run faster.
- 32-bit systems can only “see” approximately 3.5 GB of the maximum 4GB RAM that 32-bit hardware can support.
- 64-bit systems can see all 4GB and can support up to 128GB of installed RAM.
32-bit is Disappearing
We're at the end of a transition period between 32- and 64-bit software and hardware which began over 10 years ago. Just as earlier systems running 4- 8- and 16-bits has been phased out, 32-bit hardware is becoming obsolete and 32-bit operating systems will not be supported in the future.
The same bottlenecks happen when programs are forced to run in the more restricted 32-bit environment that you see when two lanes of traffic are merged into one.
- Issues with 32-bit software and drivers in 64-bit Windows.
- 32-bit and 64-bit Windows FAQ.
- Wikipedia's 64-bit article covers the history as well as the technical architecture.
Why Did it Take So Long to Transition?
Because 64-bit systems will run 32-bit software, there wasn't enough pressure to end the dominance of 32-bit software until the majority of users ran 64-bit operating systems on 64-bit hardware.
Virtually all recent computers come installed with 64-bit operating systems.
That transition is also happening for mobile devices.
Web Browsers as an Example
Most web browsers have been available in 64-bit versions for some time, but until recently most people tend to continue to use 32-bit browsers because many plugins (especially Flash) were only available in 32-bit versions.
The emerging dominance of mobile devices (which never supported plugins) has caused plugins to be phased out in favour of native HTML5 technologies and 64-bit browsers are almost universal because they are faster.
Drivers: Software that Talks to Hardware
If your computer is asking for drivers, it is looking for the specialized software that tells hardware how to work on your system.
Automatic Driver Installation
In most cases current computers are smart enough to determine what drivers are required and will download and install the correct version automatically — if drivers are available for that device on your operating system version.
Many manufacturers don't provide updated drivers for legacy hardware like printers and scanners.
If Not, You Need to Know More
If your computer doesn't automatically install drivers, you'll need to know the specific version of the hardware and your operating system (including whether they are 32- or 64-bit) in order to get the correct drivers when visiting a support website to download drivers for your computer's hardware.
You'll need to know:
- the specific model of the device you're trying to install (some have very specific versions);
- the operating system and version you wish to install it on; and
- whether the computer is running a 32-bit or 64-bit operating system.
Avoid Third-party Driver Sites
Use only the manufacturer's support website to download drivers.
Third-party sites may install malware (which can cause your computer to quit working properly) and often source drivers from users rather than the vendor.
An Example
Drivers are designed for a specific piece of hardware (HL-2240D printer) to work with a particular operating system (Mac) at a particular version level (macOS 10.14).
See Brother's listing for that printer on their support site:
32-bit Drivers Don't Work with 64-bit Systems
Even though most 32-bit software runs on 64-bit systems, 32-bit drivers will NOT run on 64-bit systems — one reason that older hardware may not run on newer systems without updated drivers.
The driver's download page will indicate if both 32- and 64-bit are supported.
HP's Color LaserJet CP1215 requires a different driver on a 64-bit version of Windows 7 than for a 32-bit version of Windows 7. No CP1215 driver is available for macOS.
Excellent Support for Current Hardware
Support for Windows drivers tends to be excellent — at least for current hardware running on a currently-supported version of Windows.
- You may have difficulty finding support for older hardware for newer Windows versions or for newer hardware on older versions of Windows.
- Because Apple hardware is proprietary you should have fewer problems except when trying to install third-party hardware not specifically designated as Mac-supported.
- Linux support for newer hardware has improved tremendously but you'll want to ensure you can obtain the necessary drivers before purchasing hardware.
New Drivers Seldom Available for Old Hardware
Manufacturers of some hardware are reluctant to provide drivers for older hardware on newer operating systems, wanting you to upgrade to newer hardware.
While this is understandable from an economic point of view (particularly for very old hardware), it is a poor environmental decision.
Supporting manufacturers more likely to provide updates to older hardware for newer operating systems is one way to encourage continued availability.
Computer Components
Hardware is the physical components of the computer including both the external components you can see (the monitor, mouse, keyboard, printer, etc.) as well as those that you can't see (like the processor, video card, hard drive, RAM, etc.).
Components may be attached to the main computer case (sometimes referred to as the "box") which contains the internal components of your computer or can be integrated (like the laptop's keyboard, touch-pad and screen).
Devices like smartphones and tablets (as well as newer integrated touch devices) are less likely to support external hardware except via Bluetooth (e.g., keyboards and speakers). Support varies by manufacturer and model.
The Motherboard
The motherboard (sometimes called the mainboard or logic board) is the main circuit board in a computer or device. All internal components connect to the motherboard in some fashion including the RAM, hard drive(s), power supply, USB ports, etc.
The motherboard is generally housed within a casing providing access ports for supported external devices like the keyboard, mouse and monitor.
It is easier to access the motherboard and other components in desktop computers, especially those built in local computer shops. Name brand desktop computers and laptops seldom provide access for consumers.
The Processor
The processor is the “brains” of the unit and is where programs are run. Most computers run Intel or AMD processors but there are others such as Apple's M1.
Modern processors are actually clusters of processors, designed to share the load and reduce heat.
The RAM
RAM is the volatile memory that a computer uses. When the computer stops, information in RAM is lost. The capacity is usually specified in gigabytes except in older computers.
The Hard Drive
The hard disk drive is a data storage device. Unlike RAM, information stored on a hard drive does not disappear when the computer is turned off (once it is saved).
Hard drive capacity is usually specified in gigabytes or terabytes and comes in 3 main formats:
- Hard Disk Drives (HHDs) are cheapest but slower and potentially noisier;
- Solid-State Drives (SSDs) operate like a flash drive and are much faster but tend to cost more and have lower capacity; and
- Solid-State Hybrid Drives (SSHDs) which the SSD technology for faster boot times with the greater reliability of HDDs.
SSDs shouldn't be defragmented but can be optimized, a function available in software like Raxco PerfectDisk and Defraggler.
Each hard drive format has benefits and risks.
It's undeniable that replacing your spinning HDD with an SSD is worth it. They make your computer boot faster and make programs more responsive. If you really need that speed boost for productivity or faster loading times in games, then an SSD will definitely be worth it.
— WePC
- How to choose between SSD, SSHD, and HDD storage for better laptop performance.
- HDD vs SSD vs SSHD compared.
The Video Card
The video card displays the output to the monitor and can be onboard (built into the motherboard) or external (a dedicated video card attached via the expansion slots on desktop computers).
The capability of the video card determines the resolution and quality of the video display.
Onboard video cards use a portion of the system RAM, so adding an external video card with its own video RAM can help to speed up your computer.
HDMI has replaced the traditional video connection on most computers, starting with laptops (its smaller form factor allowed for narrower cases).
USB
USB ports provide a “smart” hardware interface for the connection of many external hardware devices to your computer such as mice, printers, external hard drives, flash drives and more.
Unlike many earlier connections, the device tells the computer what it is and the requirements to run it so that the necessary drivers can be installed.
USB is designated as USB1, USB2, USB3 (usually designated with a blue bar inside) and USB 4 (Thunderbolt) with speed and capabilities increasing as the number gets higher.
USB-C is rapidly replacing these older USB form-factors. Not only is it smaller (similar in size to micro USB) but is now replacing many traditional laptop power connectors.
The USB-C connector looks similar to a micro USB connector at first glance, though it's more oval in shape and slightly thicker to accommodate its best feature: flippability.
— PC Mag
More about USB and its various technical specifications.
Other Components
The computer can also contain specialized ports for external SATA hard drives, VGA or SVGA or HDMI video connections.
It can also have built-in capabilities for wireless technologies like Bluetooth, infrared and WiFi or support for alternative storage mediums such as Blu-ray or the SD cards used by your digital camera.
Network Components
Networking refers to the technology interconnecting computers grouped together using wired or wireless connections.
A network is a collection of computers connected either via network cables (a LAN) or via wireless signals (a WLAN).
Security and performance is generally better on workplace networks than in home networks.
The Internet (notice the capital “I”) is also a network — one connecting many different types of computers and devices to servers all around the world.
Because virtually all of today's computers and devices are connected to the Internet, security software is an important consideration. See Internet terminology.
The Network Adapter
The network adapter is a the computer's interface to a network via the modem or router and provides for Internet and local area network (LAN) access.
Desktop computers generally have built-in LAN while laptops and mobile devices have WLAN (wireless) connections. Older laptops may have LAN connections, but most now only support wireless.
A WLAN adapter can provide wireless access if a wired connection is inconvenient or impossible.
Modems & Routers
The modem is the device that connects you to the Internet.
In earlier days people used a low-speed telephone modem to dial-up a temporary connection.
Today's always-on high speed Internet connections are provided via either a cable modem (where a cable TV vendor is the provider) or ADSL modem (where a telephone company is the provider).

Routers allow you to connect more than one computer or device to your the Internet via the modem using either a wired or wireless (WiFi) connection. Those devices are also networked together so they can communicate with each other.
Routers also provide hardware firewall protection, which combined with your software firewall, keeps your devices safe from unauthorized access to your network.

WiFi (not shown) connects many devices wirelessly to the router.
Combination modem-routers which includes both the modem and router functions are provided by most ISPs. You don't need to worry about the Internet Connection (B in the diagram above).
There are other devices in some networks, but most users don't need to worry about them. See Modem, router, and access point: What's the difference?
Change Security Settings
During set up, the router/modem must be wired to at least one of the computers. After that, all network and Internet access can be done wirelessly, although the wired connections are generally much faster and more secure.
Wireless Network Standards
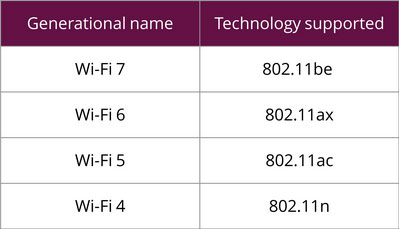
You'll see a number designations for various wireless components: 802.11n/ac/ax/be. Older designations are obsolete.
These wireless standards all share the "802.11" part at the front, but the letter at the end is the most important, designating the standard.
It is most common to just refer to the last letter when speaking about the devices. For example, 802.11n is usually called wireless N.
Wi-Fi Standards
Wi-Fi™ is a certified standard:
Wi-Fi is a trademark of the non-profit Wi-Fi Alliance, which restricts the use of the term Wi-Fi Certified to products that successfully complete interoperability certification testing.
— Wikipedia
* Elsewhere on this site I've used WiFi to refer to wireless technology, but the Wi-Fi designation is implied.
Wi-Fi Generations
Industry is moving to calling these levels by their generational name to make it easier to understand than the 802.11 nomenclature:
Only Wi-Fi 5 and later are as fast or faster than the 100Mbps throughput that wired Ethernet networks are capable of handling.
Mixing WiFi Standards
Many routers can only be configured with one standard at a time. Dual-band routers allow you to set two separate standards (e.g., n/ac) on the same network, providing access for older devices incapable of newer generational standards and can provide more reliable service than a single-band router.
More About Wi-Fi Standards
- The WiFi Alliance has more information about these standards as well as a listing of certified devices and public hot spots worldwide.
- The Wikipedia IEEE 802.11 article includes information and history about the standards including some not in common use.
- 802.11 Standards Explained: 802.11ac, 802.11b/g/n, 802.11a.
- 802.11ac vs 802.11n WiFi: What's the difference?
- What is 802.11ac WiFi, and how much faster than 802.11n is it?
Change Default Router Passwords
It is strongly recommended that you change the default passwords on your router. These default settings (usually simply “admin”) are easily obtained from support sites and can be used to hack into your home or business network.
Logging into your router via a router manufacturer's website (e.g., http://router.asus.com) is not recommended because the connection is unsecured. You want to use local access (e.g., https://192.168.50.1) instead (the http://192.168.1.1 listed in the manual is incorrect).
Disable WPS
You should also disable WPS (a push-button setup for connecting wireless devices).
While convenient, WPS makes your router more vulnerable to being hacked (for several seconds after you press the WPS button, WPS opens your network to outside access without the protection of your password).
About Specifications
When you buy a program or a hardware device it will usually have a set of specifications that indicate what operating system it is designed for as well as the minimum hardware requirements (and optimally, the recommended hardware requirements).
Higher Capabilities = Higher Satisfaction
Your satisfaction with your purchase will improve the more you exceed the minimum requirements — which is why the recommended requirements are so useful.
If you have a different version of the operating system or if your hardware is not at least as good as the system requirements then you should not buy the program.
If you purchase a device without consulting the manufacturer for suitability ensure that the vendor guarantees it will work (accepting the product back for full refund if it does not). Opened software is seldom returnable.
Windows Experience Rating
Microsoft included a "Windows Experience" rating in Windows Vista, 7 and 8. This evaluates your hardware and tells you how well your computer will perform certain tasks.
The higher the score the better, but anything less than 3.0 will mean you will have a less than satisfactory experience with even basic tasks.
The example below has a base rating of 1.0 (the lowest rating):
| Component: | What's Rated: | Experience Rating: |
|---|---|---|
| Processor: | Calculations per second | 3.9 |
| Memory (RAM): | Memory operations per second | 3.9 |
| Graphics: | Desktop performance for Windows Aero | 1.9 |
| Gaming graphics: | 3D business and gaming graphics performance | 1.0 |
| Primary hard disk: | Disk data transfer rate | 5.9 |
This sort of rating was typical of “Vista Basic” systems — essentially a crippled version of Windows Vista.
These units were 32-bit computers built for Windows XP rather than the more demanding 64-bit Windows Vista. Needless to say, the lifespan of these systems was very limited and consumers were shortchanged.
While the poor video rating could be improved with a new add-in video card, you would be better off looking for a newer, more powerful computer to begin with, like the following:

Mac Computers
Because Apple bundles its operating system with proprietary hardware, this is less of an issue until your computer begins to age (Apple may not allow updates even though the hardware supports it).
That said, Mac computers often last for 10 years and are therefore a better value even though the purchase price is more than most Windows machines.
All Computers Slow Down
All computers and software become slower as they get older because the software that takes advantage of newer technology requires more advanced and powerful hardware.
Upgrades can be made to your computer to improve performance but at some point it becomes physically impossible or simply uneconomical. You'll need to purchase a newer computer.
A Slow Computer May Be Infected
If your computer is relatively-new and you experience significant slowdowns, you should check for malware, potentially unwanted programs (PUPs) or other unwanted software installed with downloads. Ensure you don't have any security software conflicts.
Boot Environments
The boot environment is the hardware initialization that precedes the loading of the operating system. It configures the hardware recognition.
This boot process is often obscured by a full-screen logo displayed when your computer starts.
BIOS
BIOS was used to configure the boot environment for personal computers (PCs) dating back to the early IBM-PC. It provided an environment for configuring hardware separate from the operating system.
BIOS loads before the operating system and determines how hardware like memory, USB and video are configured (although much of this is now automatic).
Wikipedia's BIOS Wiki has more detailed information.
UEFI
Most modern computers use the UEFI boot environment but some computers may have been upgraded and using a legacy BIOS boot environment.
UEFI provides a more modern approach to this boot environment and adds hardware-based security. See the Wikipedia UEFI Wiki for details.
UEFI also provides for a more security via Secure Boot and a Trusted Platform Module (TPM 2.0) — a requirement for Windows 11.
Windows 8.1 and Windows 10 take advantage of UEFI technology to speed up the system startups and shutdowns, but only if the hardware supports it. Windows 11 requires UEFI with Secure Boot and TPM 2.0 plus some other security measures.
Windows 7 or earlier does NOT support UEFI technology. Windows will not boot if you enable the security options on a UEFI system.
Local Area Network Options
Some computers can boot using resources on the LAN rather than what is contained on the computer's own storage devices but network boot is seldom available outside commercial environments.
Internet Connections
Connecting to the Internet uses networking technology. The Internet is a global network rather than a local network, so security is even more important.
Internet Terminology
Some terminology that is commonly used:
- The Internet or the Web (notice that both are capitalized) is the huge world-wide network (World Wide Web) of connected computers and devices.
- Your Internet Service Provider or ISP is the company that provides your access to the Internet. ISP can also refer to a company that provides an email account that is not part of your Internet access service.
- The server is a cloud-based network of computers that host email, websites and other web services.
- The internet is both the road and the destination.
- Search engines like Yahoo, Google, Bing and DuckDuckGo are the compass and the map.
- Facebook (or Twitter or YouTube or Instagram)…are also websites: places you visit on the web.
- The browser is the car that gets you everywhere.
- — Mozilla
Understanding Your Browser
Your browser is the software used to view websites and to navigate the Web. There are many browsers but Firefox is recommended.
Firefox is a browser — one built specifically for people, not profit. If it's not your browser, maybe it should be? — Mozilla Blog
The image below shows the main areas of the Firefox browser window. Knowing the terminology helps to communicate what's happening in your browser.
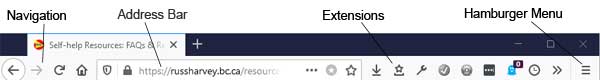
- Navigation includes forward and back arrows, reload button and home button.
- The address bar shows the address (https://russharvey.bc.ca) and displays a padlock when the site is secure (https).
- Extensions include icons for bookmarks, downloads and addons.
- The hamburger menu provides access to the other browser settings.
These features and their location can vary by browser and operating system. Most modern browsers allow you to search directly from the address bar.
Your Internet Connection
People connecting to the Internet via their ISP should know these terms:
- LAN refers to a local area network — a group of computers connected via CAT5 or CAT6 network cables (CAT6 is faster).
- WLAN refers to a wireless connection to a local area network (via WiFi) rather than with network cables.
- Most networks today are comprised of both LAN and WLAN elements.
- A server can refer to
- a remote external computer accessed via the Internet (such as the email server for your ISP or a server hosting a website); or
- a specialized computer that runs and manages a network in an office environment.
IP Address
Whenever a device (computer, tablet, smartphone, etc.) is connected to a network or to the Internet (a very large network) your device is assigned a unique IP address.
This address is a series of numbers based upon Internet protocols (hence IP or Internet protocol). Your IP address reveals your ISP and at least a general location
Your ISP assigns a public IP address to your router which in turn assigns private IP addresses to all the devices connected to that router.
- See Mozilla's What is an IP address? to learn more.
The Internet is Vast
Most people recognize the public part of the Internet which includes social media, information portals, news sites, blogs, business information, public databases, and more.
Search engines were developed to help you find what you're looking for in this vast network of sites.
The Deep Web
Not all of the Internet is open to the public.
The deep web is the very large part of the Internet that is unavailable to the general public such as contents of your email or Dropbox.
Danger, Will Robinson, Danger
Other areas are purposely hidden and dangerous for most people to visit.
- The dark web is that part of the Internet that is purposely hidden unless you know exactly where to look.
- This is where hackers go to obtain their tools or to purchase data stolen in data breaches.
If your computer is acting strangely or is slow, your computer may be infected with malware or could be part of a botnet using your computer to attack other computers.
- A botnet is a network of compromised computers (or Internet-connected devices) that are controlled by a third party without the owners' permission.
- Most botnets are a result of a malware infection.
Configuring Email
When configuring an email client you'll run into several terms that might not make sense to you. You don't need to know the specifics but do need to understand the differences.
- An email server can refer to
- the email server for your ISP; or
- a specialized computer that runs and manages email on an office LAN.
- An email client is
- a standalone email program on a computer; or
- mobile device that can send and retrieve email messages.
- A webmail client is a remote server-based email service that allows you to manage your email using your web browser.
- This may includes services like Gmail or web-based access to your ISP's email server.
- Some webmail services offer a mobile app or provide access to email clients.
Email Settings
If you're using an email client supported by your ISP, then they'll indicate the settings and where to enter them.
Otherwise, you'll need to configure your email program from the generic settings provided by your ISP. You may require help determining what goes where.
Send/Receive Settings
Most configurations begin with settings related to how to send or retrieve emails:
- The name allows you a description of yourself and possibly your role in an organization (e.g., Joe or Joe Smith, Manager).
- This entry is flexible and does not form part of the security protection for your email account.
- The user name (usually designated as “username”) is unique to your email account.
- It may be assigned to you by your ISP or you may be able to choose it yourself.
- Account settings usually require the full email address ([email protected]) but may only need the first part (joesmith) or an account designation (AC1245).
- The password is the secret character string that protects your email account.
- This is probably the only non-public piece of information of the three (especially if your email address is your username).
Email Security
Each username-password combination is unique to the particular account and should be kept secret to protect your email account from being hacked.
Since your email account is accessed via the Internet, it is accessible to anyone that knows or can guess your password.
Learn more about passwords and security precautions.
Email Protocols
Once you've setup the login details, you need to tell the email program how your email is to be handled and what protocols are to be used.
IMAP, POP and SMTP are email protocols used when configuring email retrieval. Once setup, email will be managed transparently if the settings are correct and you have entered the right password.
IMAP allows you to maintain the same mail on multiple email programs, computers or devices simultaneously, each mirroring what is on the server. Deleting messages with IMAP on any of the connected devices will remove them from both the server and ALL devices connected to that account with IMAP.
POP3 retrieves mail from the server, generally deleting it following successful retrieval. You can opt to leave it on the server for a period of time or permanently.
SMTP is a protocol for transmitting email messages to the server from which they are distributed to the intended recipients.
Because most people now use multiple devices, IMAP has become the default configuration regardless of its shortcomings. POP/SMTP protocols and their documentation are disappearing from ISP support sites.
Choosing the Right Protocol
Either POP/SMTP or IMAP will work on your desktop, laptop, tablet or smartphone provided you've set them up correctly and your ISP supports those protocols.
However, your experience in syncing and storage of messages may differ:
| Function: | POP | IMAP |
|---|---|---|
| Sync Received Email | Maybe1 | Yes |
| Sync Sent Email | No | Yes |
| Store Mail Locally | Yes | No2 |
1Ensuring all your devices retrieve all messages sent to your email account requires special settings (discussed below) and has certain drawbacks.
2IMAP mirrors the server on all devices. When you delete a message on any device or the server, it is deleted everywhere. This makes IMAP unsuitable for storing important messages like receipts for tax preparation or important documents.
Neither of these protocols will sync either your contacts or your calendar natively.
- Microsoft Exchange provides this support.
- Apple currently supports the syncing between iOS and macOS devices.
POP3/SMTP Combo
POP3 combined with SMTP works fine where the emails are being sent and retrieved by a single email client on a single computer. Mail can be saved (archived) on the computer then deleted on the server once your email program has successfully downloaded the messages. Your emails are kept private and are not as vulnerable to hacking as mail left on the server.
There are limitations when using POP on multiple email clients or devices for the same account.
- Sent messages are stored ONLY on the computer or device from which they are created unless you BCC: yourself.
- If more than one program or device is deleting messages after retrieval there is the potential for having messages spread between devices with no device or program with ALL the mail.
To have all mail on all devices you need to leave the messages on the server until all devices have retrieved them.
- Check the mail management setting for the affected email account(s) under properties or settings.
- Set one device or computer to automatically remove messages after a set period of time (e.g., 15 days).
- Because messages aren't being deleted from the server right away, unwanted messages should download to all devices.
- You can log into your ISP's webmail interface to manually delete any unwanted messages.
If your mobile device is used only when away from your computer, delaying deletion of emails on your main computer or device might work for you as long as
- you only need any incoming messages while you're away;
- your mobile device doesn't delete messages from the server that it downloads; and
- you BCC (blind-carbon-copy) to yourself any important outgoing messages including replies to incoming messages.
When you get back to your computer, you can download the messages you viewed earlier to the computer hosting the primary email records as well as the BCC copies of your sent messages.
IMAP
IMAP resolved this issue by mirroring the same information on the server and on all connected email clients and devices, including sent, received and archived messages.
Unfortunately, IMAP has its own limitations.
- Deleting messages with IMAP on any of the connected devices or the server will remove it from the server plus ALL devices connected to that IMAP account.
- Email on the server is accessible via the Internet and can be hacked from anywhere worldwide.
Most email accounts have limits on how much you can store on their servers.
- Once you pass that limit the ISP may simply delete the oldest messages or “bounce” incoming messages (often arbitrarily and without warning).
- You can purchase extras storage, but some ISPs limit the amount of space you can purchase.
Remember, IMAP depends upon the server to manage messages. Once all the devices have synced a deleted message, it is gone forever.
Server Settings
In addition to the protocols there are other settings, some of which are dependent upon how your ISP configures its servers and partly on whether the connection is secure or not.
- POP defaults to port 110, IMAP to port 995 and SMTP to 587 but may be set to something else depending upon the security settings.
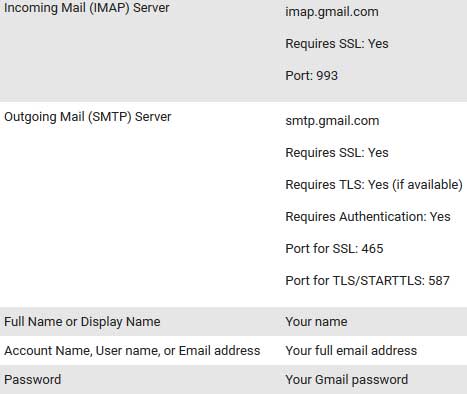
- Security is generally one of Regular, Secure to regular port (STARTTLS) or Secure to dedicated port (TLS). Older email programs may not support secure connections.
For example, Gmail settings as indicated by Google Support:
Learning More
Wikipedia has more about the various protocols involved.
FTP
File Transfer Protocol (FTP) is a standardized network protocol used to transfer files between a client and a server over the internet or any other TCP/IP network and is one of the oldest protocols on the Internet.
FTP is so old it predates email—and at the beginning, actually played the role of an email client.
— Tedium
People once used FTP to download files from sites like Adobe and Hobbes OS/2 Archive.
Browsers Ended FTP Support
All web browsers except the obsolete Internet Explorer have removed support for FTP in their modern versions.
The File Transfer Protocol (FTP) has long been a convenient file exchange mechanism between computers on a network. While this standard protocol has been supported in all major browsers almost since its inception, it's by now one of the oldest protocols still in use and suffers from a number of serious security issues.The biggest security risk is that FTP transfers data in cleartext, allowing attackers to steal, spoof and even modify the data transmitted. To date, many malware distribution campaigns launch their attacks by compromising FTP servers and downloading malware on an end user's device using the FTP protocol.
— FileZilla FAQ
Mostly Used for Updating Websites
Unless you maintain a traditional website, it is unlikely that you'll run into or require FTP programs like FileZilla (which have moved to the more secure SFTP protocol).
Software Versions
Finding the version number varies by operating system and product but is usually indicated in the help menu (look under the program name in macOS):
- Windows: Help ⇒ About
- macOS: Program Name ⇒ About.
With the move to wider screens, the text menu is hidden by many programs including most modern browsers, replaced with a “hamburger” menu (≡), vertical ellipsis (⋮) or horizontal ellipsis (…) on the right of the browser toolbar.
Major and Minor Upgrades
Software versions tend to run in major and minor updates and may include pre-release (or beta) versions.
For example, version 7.4.2 could breakdown as follows:
- The first number (7) indicates the major version number (the seventh generation).
- The second number (4) indicates a minor update.
- The third number (2) indicates a revision or potentially a bugfix.
Generally major revisions include significant changes to the program and could be incompatible with earlier versions or require newer hardware.
Inconsistencies
Version numbering may not be consecutive. The vendor still needs to track pre-release versions (7.4.0 and 7.4.1 may never have been released).
A vendor may skip a major version increment (such as Windows 10 did) or considers a normally-minor update to be a major update (such as Windows 8.1).
Some vendors add a fourth build number (such as version 32.0.0.03).
Paid Software
If you purchased a piece of software, minor revisions are usually free but you'll need to purchase a licence upgrade once the major revision changes.
In our example, all updates that begin with the same full version (e.g., if you purchased version 7.0, updates 7.2,1 , 7.6.0 and 7.9.2 would be free).
However, once the version moved to the next version (8.0 in our example) most vendors would charge a fee to purchase the updated version.
- Vendors often provide a discount to existing product owners to encourage them to stay current with their software.
- Some vendors provide all updates to anyone holding a licence for a product for life, but this is rare.
What is Beta Software?
Beta software is pre-release software that is released into the field after its initial in-house testing (called “alpha”) to determine how it performs with other software, hardware and accessories.
Unlike regular software releases, beta software can contain serious bugs.
For Experienced Users Only
Beta software should not be installed or tested except by experienced users and NOT on production equipment (computers that you need to be dependable).
Beta testers are aware of the risks that unreliable software can pose to their computers and data when testing pre-release software.
I once beta-tested an FTP program (software to upload files to a web server) with a bug that deleted all the local AND remote files without asking. Fortunately, I had backups.
Tracking Beta Versions
Pre-release betas (new, never released, software) are generally assigned a "0" (zero) for their major release followed by the minor revision (e.g., version 0.4).
When the software is released to the public the product usually considered to be at version 1.0.
Future betas (sometimes called a “technical preview”) generally carry the major revision number they'll have at final release. The method for identifying the various pre-release builds varies by vendor.
Beta testers usually need to register, agreeing to the beta conditions and acknowledging the risks.
Ongoing Betas
The public seldom sees betas other than those just prior to the release of new software or major updates. However, some software, particularly open source software, has ongoing betas open to the public.
One example of ongoing beta software is Firefox Developer Edition, beta software which allows web developers to gain access to tools and platform features at least 12 weeks before they are released to the standard Firefox.
Related Resources
On this site:
Return to top
russharvey.bc.ca/resources/terminology.html
Updated: May 29, 2025